Android malware uses VNC to give attackers hands-on access

A new Android banking and remote access trojan (RAT) dubbed Klopatra disguised as an IPTV and VPN app has infected more than 3,000 devices across Europe.
Klopatra is described as a powerful trojan that can monitor the screen in real time, capture input, simulate gesture navigation, and features a hidden Virtual Network Computing (VNC) mode.
Researchers at cybersecurity company Cleafy say that the new trojan does not appear to be connected to any documented Android malware families and appears to be the project of a Turkish-speaking cybercrime group.
Klopatra was developed to steal banking credentials via overlay attacks, exfiltrate clipboard content and keystrokes, drain accounts over VNC, and collect cryptocurrency wallet app info.
A stealthy, evasive threat
The malware infiltrates victims’ devices through a dropper app called “Modpro IP TV + VPN,” which is distributed outside of the official Google Play platform for Android.
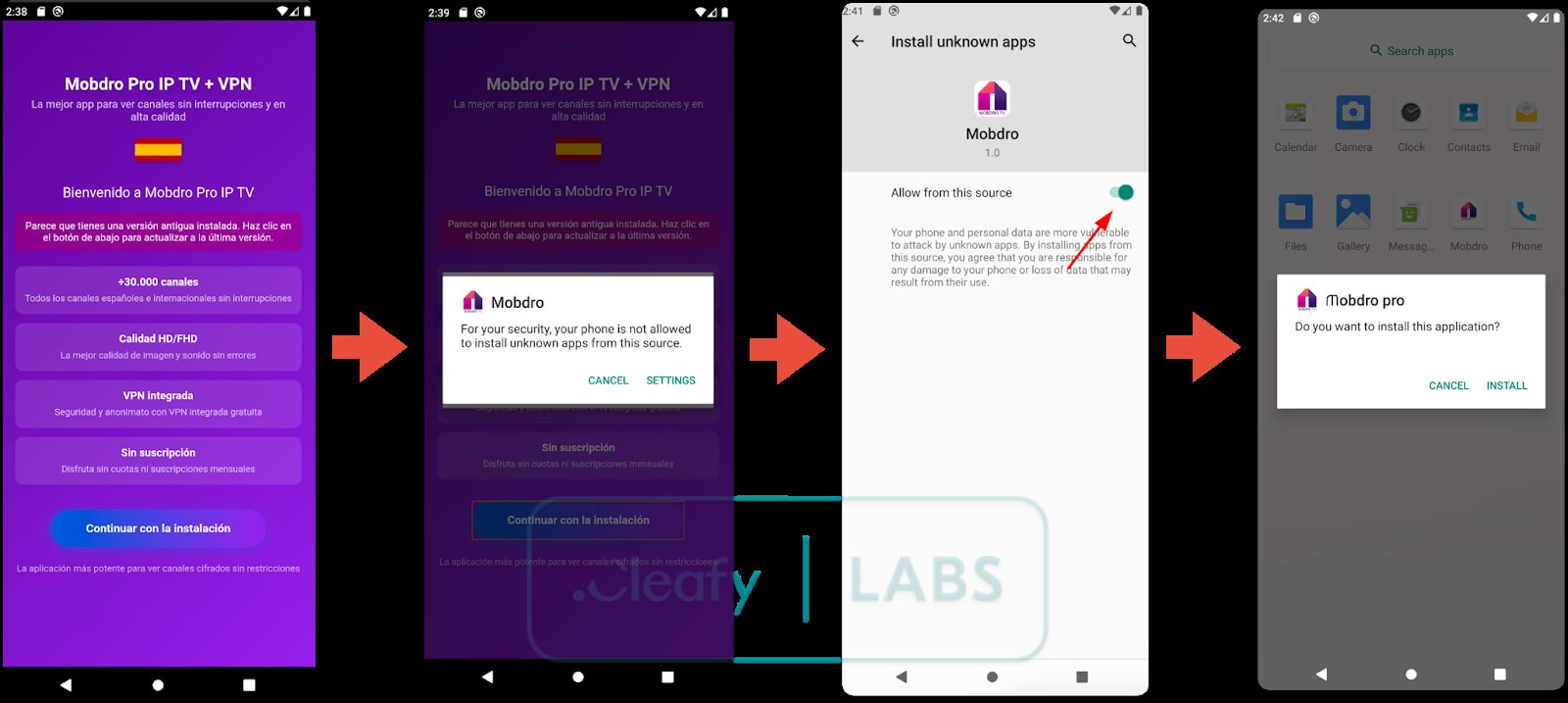
Source: Cleafy Labs
Klopatra integrates Virbox, a commercial-grade code protector that obstructs reverse-engineering and analysis, uses native libraries to reduce its Java/Kotlin footprint, and also NP Manager string encryption in recent builds.
Cleafy reports that the malware features several anti-debugging mechanisms, runtime integrity checks, and emulator detection capabilities, to ensure it’s not running in an analysis environment.
Klopatra abuses Android’s Accessibility service to grant itself additional permissions, capture user inputs, simulate taps and gestures, and monitor the victim’s screen for passwords and other sensitive information.
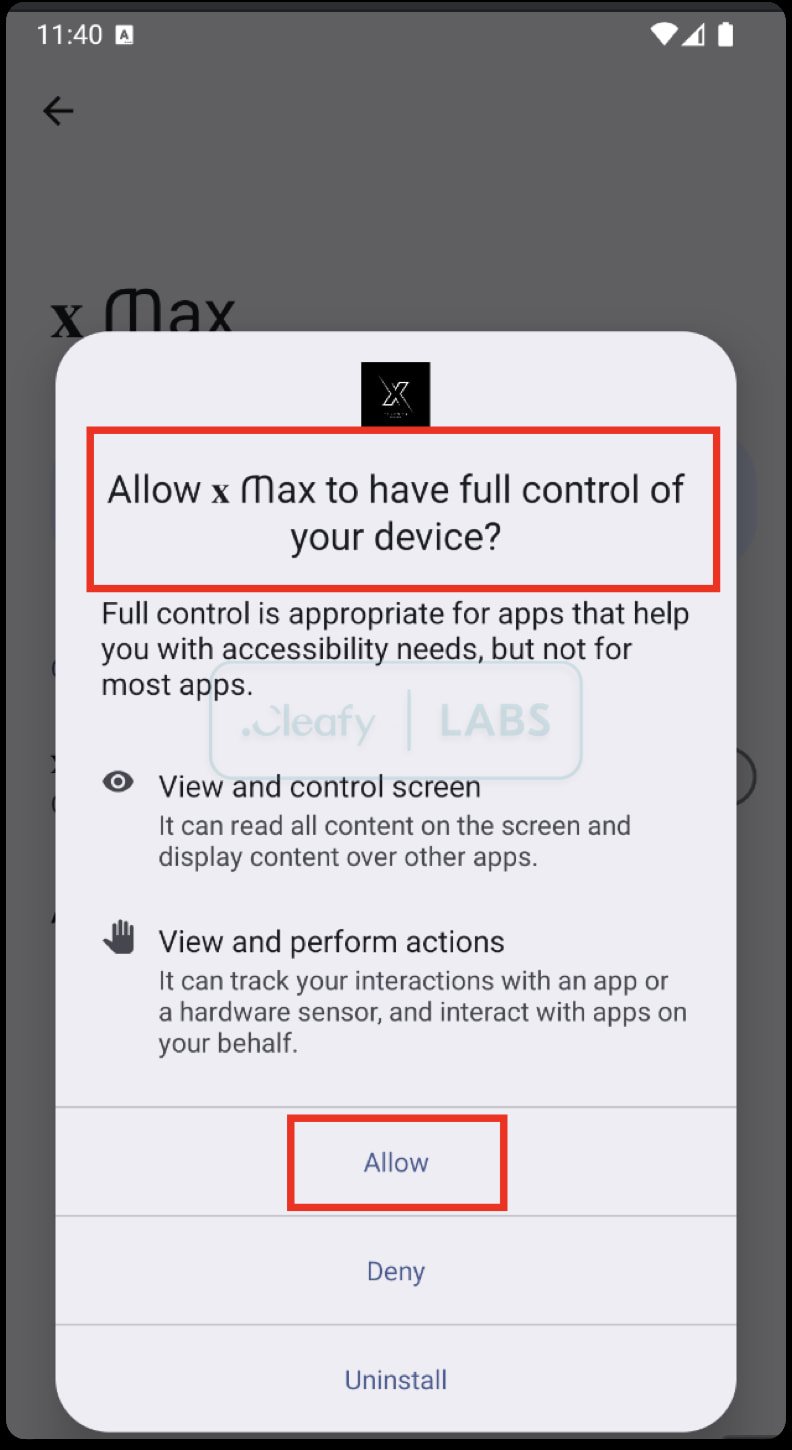
Source: Cleafy Labs
One key feature is a black-screen VNC mode that allows operators to perform actions on the infected device while it appears idle (with a locked screen) to the victim.
This mode supports all the required remote actions for performing manual bank transactions, like simulating taps on defined screen coordinates, swiping up/down, and long-pressing.
The malware checks if the device is charging or if the screen is off to determine the ideal moment to activate this mode without the user realizing it.
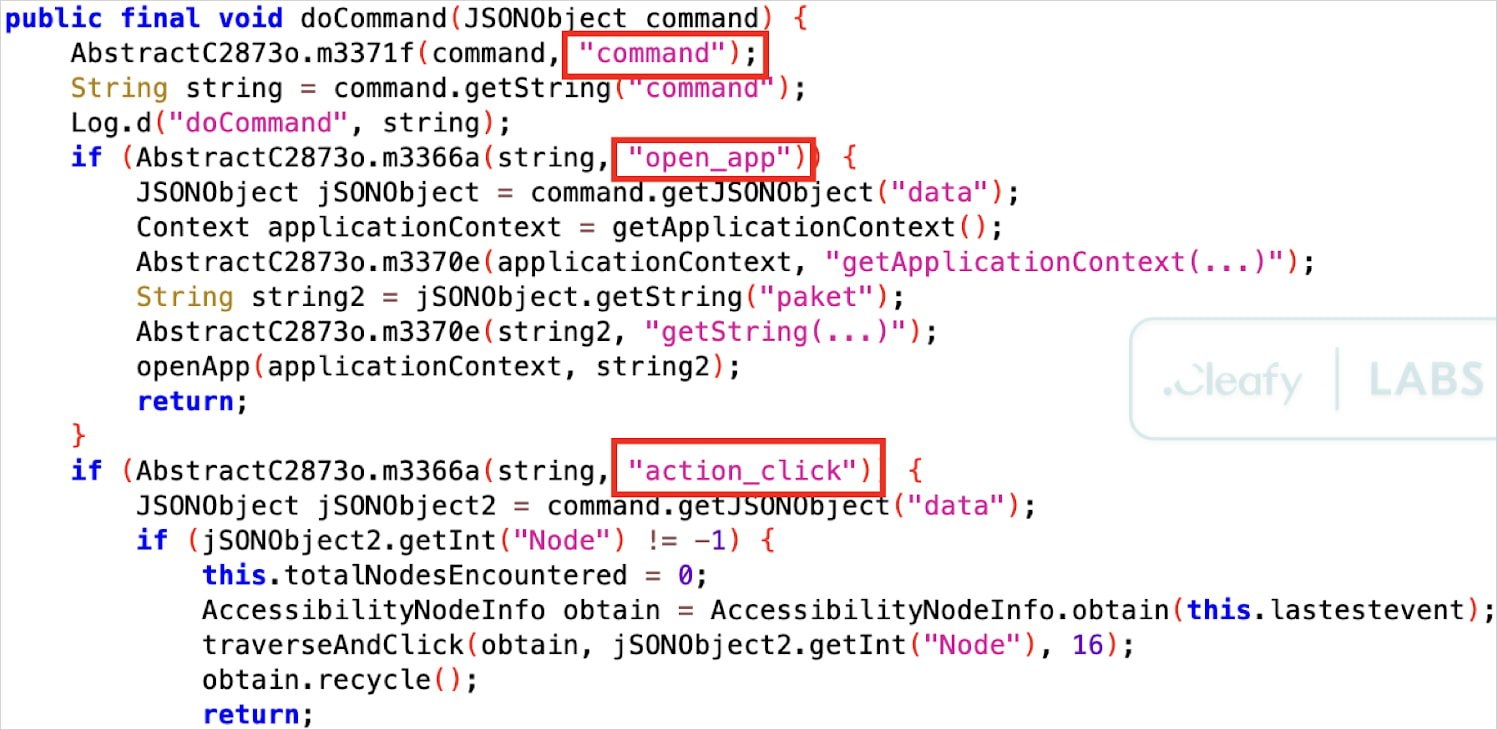
Source: Cleafy Labs
To avoid detection, Klopatra also contains a hardcoded list of package names corresponding to popular Android antivirus products, and attempts to uninstall them.
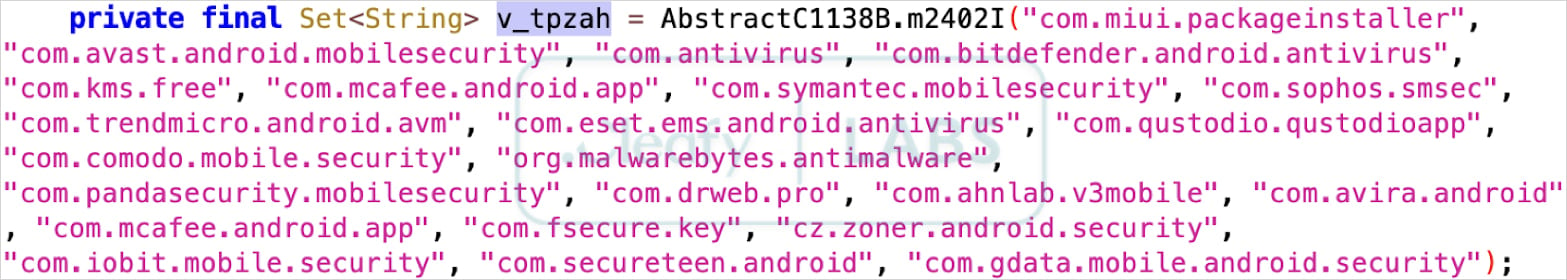
Source: Cleafy Labs
Operator exposure
Based on language artifacts and notes about development and monetization, Cleafy researchers believe that Klopatra is operated by a Turkish threat actor.
The researchers exposed multiple command and control (C2) points that appear connected to two campaigns, which count 3,000 unique infections.
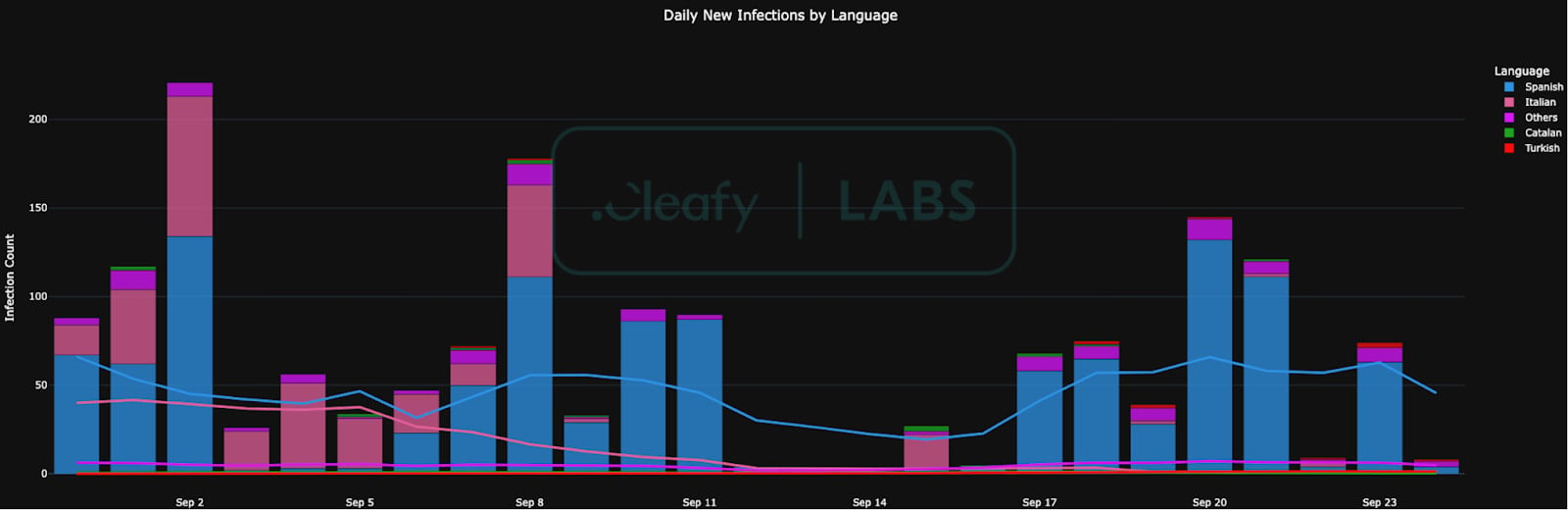
Source: Cleafy Labs
Although the operators of the malware use Cloudflare to hide their digital tracks, a misconfiguration exposed origin IP addresses, which allowed linking the C2 servers to the same provider.
Since March 2025, when Klopatra first appeared in the wild, there have been 40 distinct builds, a sign of active development and quick evolution for the new Android trojan.
Android users are advised to avoid downloading APK files from obscure websites, reject Accessibility Service permission requests, and keep Play Protect active on their device.
Source link


