Chinese hackers breach more US telecoms via unpatched Cisco routers

China’s Salt Typhoon hackers are still actively targeting telecoms worldwide and have breached more U.S. telecommunications providers via unpatched Cisco IOS XE network devices.
Recorded Future’s Insikt Group threat research division states that the Chinese hacking group (tracked Salt Typhoon and RedMike) has exploited the CVE-2023-20198 privilege escalation and CVE-2023-20273 Web UI command injection vulnerabilities.
These ongoing attacks have already resulted in network breaches at multiple telecommunications providers, including a U.S. internet service provider (ISP), a U.S.-based affiliate of a U.K. telecommunications provider, a South African telecom provider, an Italian ISP, and a large Thailand telecommunications provider.
The threat researchers said they’ve spotted compromised and reconfigured Cisco devices on their networks, communicating with Salt Typhoon-controlled servers via generic routing encapsulation (GRE) tunnels for persistent access.
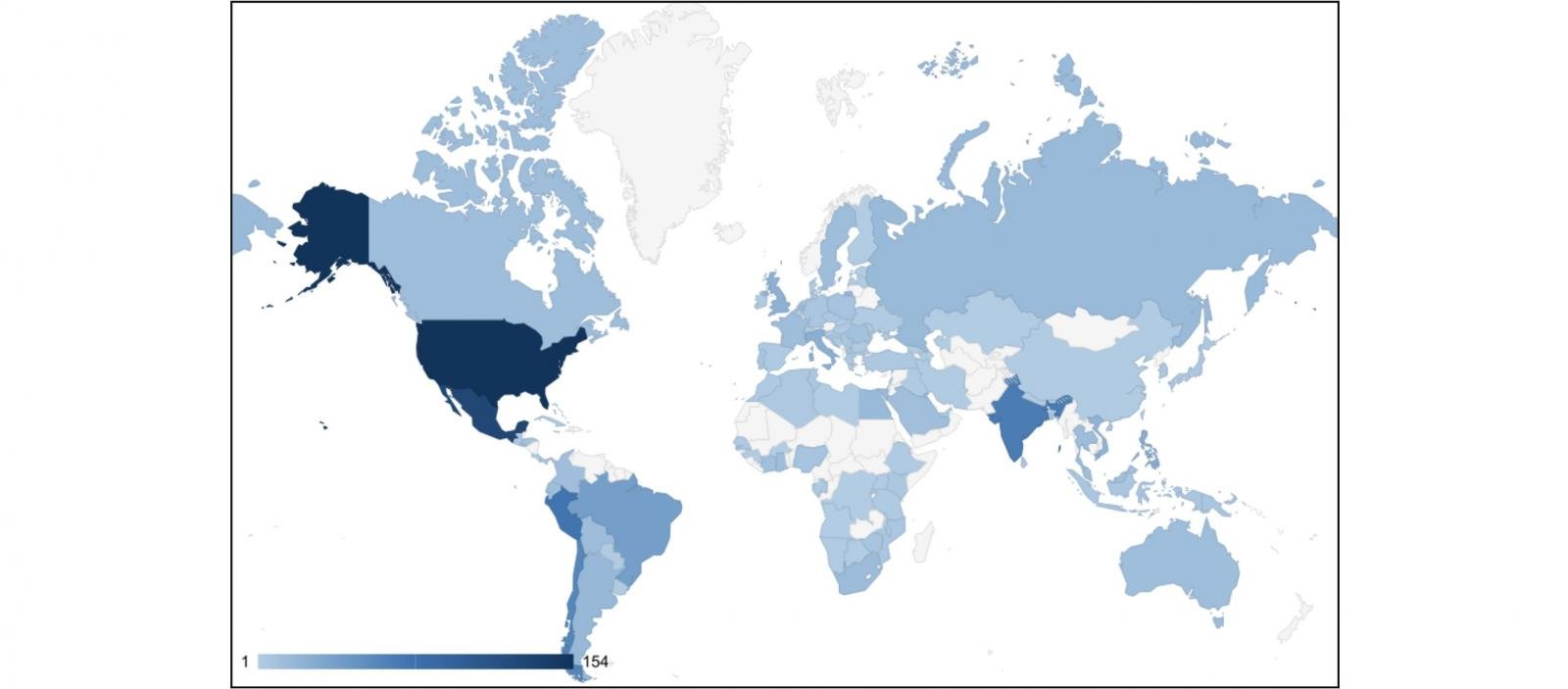
Between December 2024 and January 2025, Salt Typhoon targeted over 1,000 Cisco network devices, more than half from the U.S., South America, and India.
“Using internet scanning data, Insikt Group identified more than 12,000 Cisco network devices with their web UIs exposed to the internet,” Insikt Group said.
“Although over 1,000 Cisco devices were targeted, Insikt Group assesses that this activity was likely focussed, given that this number only represents 8% of the exposed devices and that RedMike engaged in periodic reconnaissance activity, selecting devices linked to telecommunications providers.”
Two years ago, the two vulnerabilities were exploited in zero-day attacks that compromised over 50,000 Cisco IOS XE devices, allowing the deployment of backdoor malware via rogue privileged accounts. According to a November advisory from Five Eyes, these security flaws were among the top four most frequently exploited in 2023.
Iniskt Group advises network admins operating Internet-exposed Cisco IOS XE network devices to apply available security patches as soon as possible and avoid exposing administration interfaces or non-essential services directly to the Internet.
“To date, we have not been able to validate these claims but continue to review available data. In 2023, we issued a security advisory disclosing these vulnerabilities along with guidance for customers to urgently apply the available software fix,” a Cisco spokesperson told BleepingComputer after publishing time.
“We strongly advise customers to patch known vulnerabilities that have been disclosed and follow industry best practices for securing management protocols.”
These breaches are part of a broader campaign confirmed by the FBI and CISA in October. In these attacks, the Chinese state hackers breached multiple U.S. telecom carriers (including AT&T, Verizon, Lumen, Charter Communications, Consolidated Communications, and Windstream) and telecom companies in dozens of other countries.
While they had access to the U.S. telecoms’ networks, they compromised the “private communications” of a “limited number” of U.S. government officials and accessed the U.S. law enforcement’s wiretapping platform.
The Salt Typhoon Chinese cyber-espionage group (also tracked as FamousSparrow, Ghost Emperor, Earth Estries, and UNC2286) has been breaching telecom companies and government entities since at least 2019.
Update February 14, 11:31 EST: Added Cisco statement.
Source link