DrayTek routers worldwide go into reboot loops over weekend

Many Internet service providers (ISPs) worldwide are alerting customers of an outage that started Saturday night and triggered DrayTek router connectivity problems.
Those affected by this incident reported seeing routers across multiple series models intermittently losing connectivity and entering boot loops.
Impacted ISPs (including Gamma, Zen Internet, ICUK, and A&A in the United Kingdom and elsewhere) confirmed these reports and linked the Internet connection issues to attacks targeting unspecified vulnerabilities, knocking the routers offline, or a buggy software update pushed by DrayTek that caused impacted devices to enter a boot loop.
As first reported by ISPreview, affected customers (including those in Australia and outside the UK) were told to upgrade their devices to the latest firmware, disable SSLVPN/Remote Access, or even switch to routers from other vendors if the issues weren’t fixed.
“The cause has been narrowed down to vulnerable firmware versions on Draytek routers. If you are seeing broadband circuits exhibiting repeat short sessions, please upgrade the firmware to the latest version,” ICUK added.
“We urge customers to upgrade the DrayTek router to the latest firmware, or switch out the router entirely, to restore connectivity. We have had confirmation from other end users that the latest firmware from DrayTek resolves the fault,” Zen Internet said.
DrayTek: Upgrade and disable SSL VPN
While DrayTek has yet to reply to BleepingComputer’s request for comment, it published a support document on Monday regarding this incident, providing guidance on addressing the router reboot issues.
“The solution is to disconnect the WAN and then try to upgrade to the latest firmware (not applicable if the latest firmware is older than 2024. e.g 2760 does not have this patch). Try the TFTP firmware upgrade if the normal upgrade using the WEB UI does not work,” DrayTek says.
“If remote access is enabled, disable it unless absolutely necessary. Use an access control list (ACL) and enable 2FA if possible. For unpatched routers, disable both remote access (admin) and SSL VPN. Note: ACL doesn’t apply to SSL VPN (Port 443), so temporarily disable SSL VPN until upgraded.”
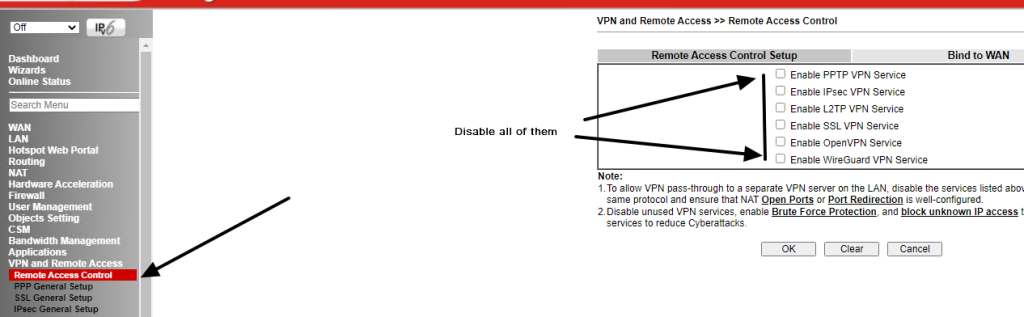
DrayTek also recommended switching off all VPN features on the Remote Access Control page, as shown in the screenshot below.
The company also provided affected ISPs with the following list of recommended measures to restore connectivity (although they didn’t explain what was causing the routers to lose connection randomly):
- Disconnect the WAN cable.
- Log into the router’s Web UI and check the system uptime. If the uptime is lower than the last known reboot, this indicates the router recently restarted.
- Disable Remote Management by going to [System Maintenance] > [Remote Management].
- Disable SSL VPN Service by going to [VPN and Remote Access] > [Remote Access Control].
- Reboot the router and reconnect the WAN cable.
- Monitor the connection to see if the WAN remains stable.
In October, DrayTek also fixed critical security flaws that affected 24 router models and over 700,000 devices whose web user interface was exposed on the Internet.
BleepingComputer has contacted DrayTek to ask if the reboot loops were caused by vulnerability exploitation or buggy firmware and will update if we hear back.
Source link