Eagerbee backdoor deployed against Middle Eastern govt orgs, ISPs

New variants of the Eagerbee malware framework are being deployed against government organizations and internet service providers (ISPs) in the Middle East.
Previously, the malware was seen in attacks conducted by Chinese state-backed threat actors who Sophos tracked as ‘Crimson Palace.’
According to a new report by Kaspersky researchers, there’s a potential connection to a threat group they call ‘CoughingDown,’ based on code similarities and IP address overlaps.
“Because of the consistent creation of services on the same day via the same webshell to execute the EAGERBEE backdoor and the CoughingDown Core Module, and the C2 domain overlap between the EAGERBEE backdoor and the CoughingDown Core Module, we assess with medium confidence that the EAGERBEE backdoor is related to the CoughingDown threat group” explains Kaspersky
The Eagerbee malware framework
Kaspersky couldn’t determine the initial access vector in the Middle East attacks but reports that, in previous cases, two East Asian organizations were breached via the exploitation of the Microsoft Exchange ProxyLogon flaw (CVE-2021-26855).
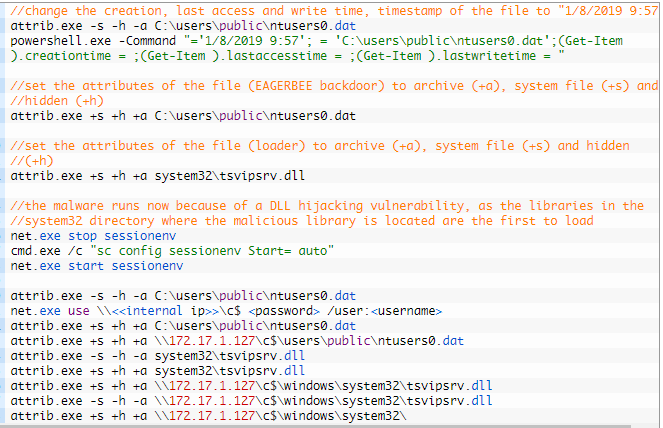
The attack involves the deployment of an injector (tsvipsrv.dll) dropped in the system32 directory to load the payload file (ntusers0.dat).
Upon system start, Windows executes the injector, which then abuses the ‘Themes’ service, as well as SessionEnv, IKEEXT, and MSDTC, to write the backdoor payload in memory using DLL hijacking.
Source: Kaspersky
The backdoor can be configured to execute at specific times, but Kaspersky says it was set to run 24/7 in the observed attacks.
Eagerbee appears on the infected system as ‘dllloader1x64.dll’ and immediately begins collecting basic information like OS details and network addresses.
Upon initialization, it establishes a TCP/SSL channel with the command-and-control (C2) server from where it can receive additional plugins that extend its functionality.
The plugins are injected into memory by a plugin orchestrator (ssss.dll), which manages their execution.
The five plugins documented by Kaspersky are the following:
- File Manager Plugin: Handles file system operations, including listing, renaming, moving, copying, and deleting files or directories. It can adjust file permissions, inject additional payloads into memory, and execute command lines. It also retrieves detailed file and folder structures and manages volume labels and timestamps.
- Process Manager Plugin: Manages system processes by listing running processes, launching new ones, and terminating existing ones. It can execute command lines or modules in the security context of specific user accounts.
- Remote Access Manager Plugin: Facilitates remote access by enabling RDP sessions, maintaining concurrent RDP connections, and providing command shell access. It also downloads files from specified URLs and injects command shells into legitimate processes for stealth.
- Service Manager Plugin: Controls system services by creating, starting, stopping, deleting, or enumerating them. It can manage both standalone and shared service processes while collecting service status details.
- Network Manager Plugin: Monitors and lists active network connections, gathering details like state, local/remote addresses and ports, and associated process IDs for both IPv4 and IPv6 protocols.
Overall, Eagerbee is a stealthy and persistent threat that has extensive capabilities on compromised systems.
The same backdoor-loading chain was also discovered in Japan, so the attacks are global.
Organizations should patch ProxyLogon on all Exchange servers and use the indicators of compromise listed in Kaspersky’s report to catch the threat early.
Source link