EncryptHub linked to MMC zero-day attacks on Windows systems

A threat actor known as EncryptHub has been linked to Windows zero-day attacks exploiting a Microsoft Management Console vulnerability patched this month.
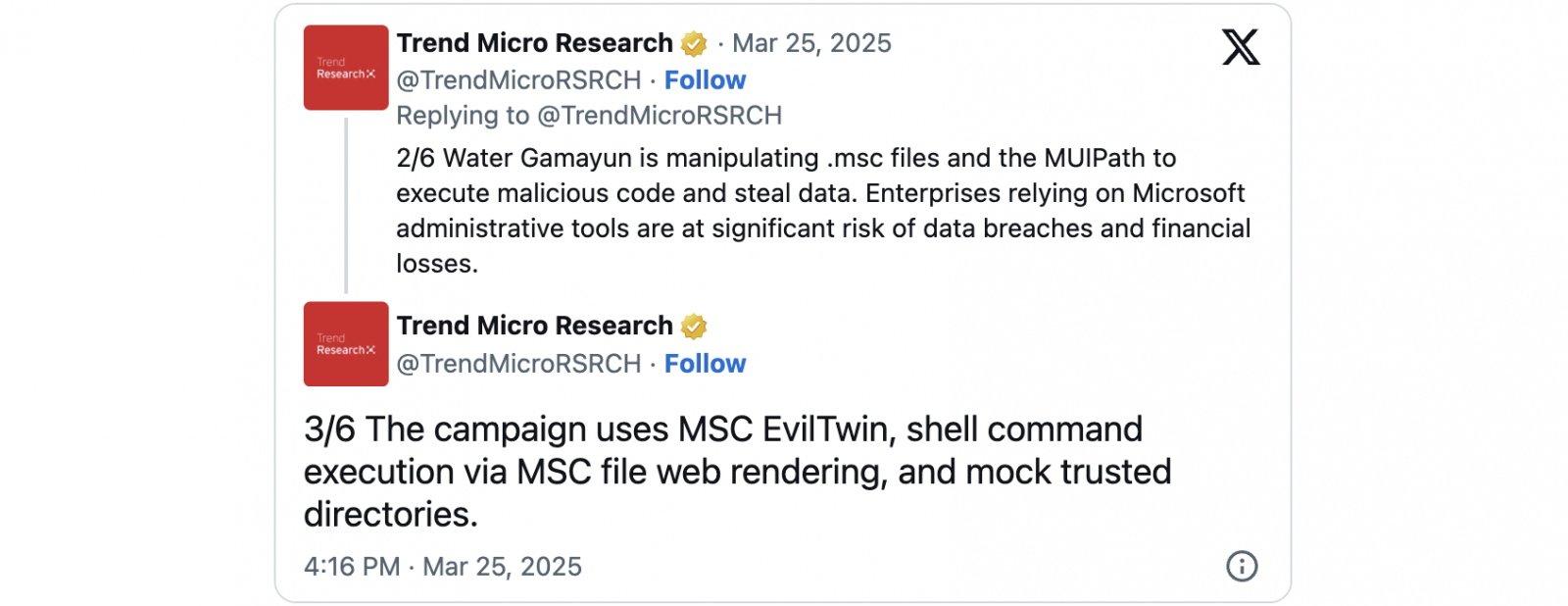
Uncovered by Trend Micro staff researcher Aliakbar Zahravi, this security feature bypass (dubbed ‘MSC EvilTwin’ and now tracked as CVE-2025-26633) resides in how MSC files are handled on vulnerable devices.
Attackers can leverage the vulnerability to evade Windows file reputation protections and execute code because the user is not warned before loading unexpected MSC files on unpatched devices.
“In an email attack scenario, an attacker could exploit the vulnerability by sending the specially crafted file to the user and convincing the user to open the file,” Microsoft explains in an advisory issued during this month’s Patch Tuesday. “In a web-based attack scenario, an attacker could host a website (or leverage a compromised website that accepts or hosts user-provided content) containing a specially crafted file designed to exploit the vulnerability.”
In attacks spotted by Trend Micro’s researchers before reporting the flaw to Microsoft, EncryptHub (also known as Water Gamayun or Larva-208) used CVE-2025-26633 zero-day exploits to execute malicious code and exfiltrate data from compromised systems.
Throughout this campaign, the threat actor has deployed multiple malicious payloads linked to previous EncryptHub attacks, including the EncryptHub stealer, DarkWisp backdoor, SilentPrism backdoor, Stealc, Rhadamanthys stealer, and the PowerShell-based MSC EvilTwin trojan loader.
“In this attack, the threat actor manipulates .msc files and the Multilingual User Interface Path (MUIPath) to download and execute malicious payload, maintain persistence and steal sensitive data from infected systems,” Zahravi said in a report published on Tuesday.
“This campaign is under active development; it employs multiple delivery methods and custom payloads designed to maintain persistence and steal sensitive data, then exfiltrate it to the attackers’ command-and-control (C&C) servers.”
While analyzing these attacks, Trend Micro has also found an early version of this technique used in an April 2024 incident.
Cyber threat intelligence company Prodaft has previously linked EncryptHub to breaches of at least 618 organizations worldwide following spear-phishing and social engineering attacks.
EncryptHub also deploys ransomware payloads to encrypt victims’ files after stealing sensitive files as an affiliate of the RansomHub and BlackSuit ransomware operations.
This month, Microsoft also patched a zero-day vulnerability (CVE-2025-24983) in the Windows Win32 Kernel Subsystem, which had been exploited in attacks since March 2023.
Source link