GlassWorm malware returns on OpenVSX with 3 new VSCode extensions

The GlassWorm malware campaign, which impacted the OpenVSX and Visual Studio Code marketplaces last month, has returned with three new VSCode extensions that have already been downloaded over 10,000 times.
GlassWorm is a campaign and malware that leverages Solana transactions to fetch a payload targeting GitHub, NPM, and OpenVSX account credentials, as well as cryptocurrency wallet data from 49 extensions.
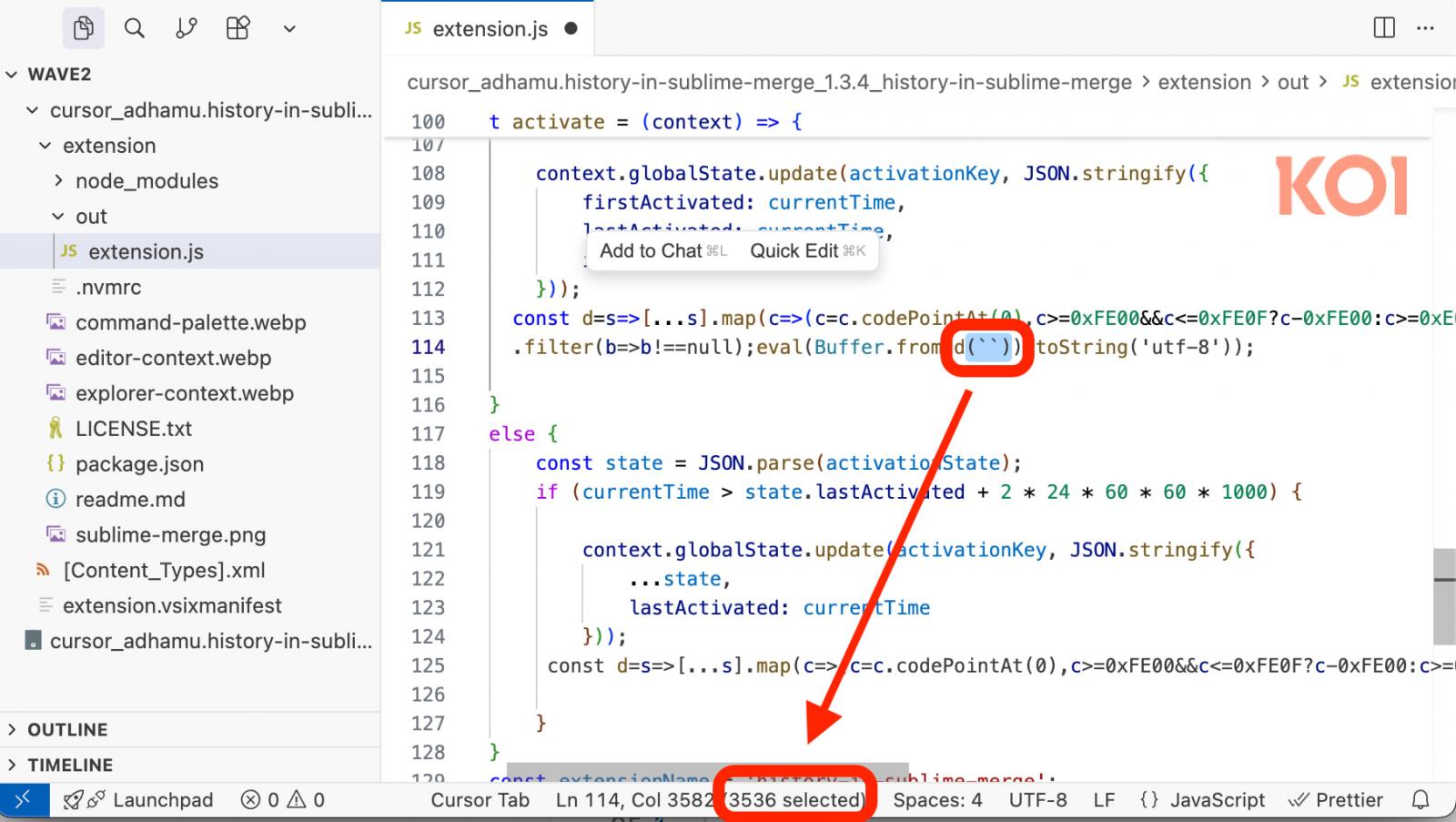
The malware uses invisible Unicode characters that render as blanks, but execute as JavaScript to facilitate malicious actions.
It first appeared via 12 extensions on Microsoft’s VS Code and OpenVSX marketplaces, which were downloaded 35,800 times. However, it is believed that the number of downloads was inflated by the threat actor, making the full impact of the campaign unknown.
In response to this compromise, Open VSX rotated access tokens for an undisclosed number of accounts breached by GlassWorm, implemented security enhancements, and marked the incident as closed.
GlassWorm returns
According to Koi Security, which has been tracking the campaign, the attacker has now returned to OpenVSX, using the same infrastructure but with updated command-and-control (C2) endpoints and Solana transactions.
The three OpenVSX extensions carrying the GlassWorm payload are:
- ai-driven-dev.ai-driven-dev — 3,400 downloads
- adhamu.history-in-sublime-merge — 4,000 downloads
- yasuyuky.transient-emacs — 2,400 downloads
Koi Security says all three extensions use the same invisible Unicode character obfuscation trick as the original files. Evidently, this remains effective at bypassing OpenVSX’s newly introduced defenses.
Source: Koi Security
As Aikido reported earlier, GlassWorm operators weren’t deterred by last month’s exposure and had already pivoted to GitHub, but the return to OpenVSX via new extensions shows an intention to resume operations across multiple platforms.
Attack infrastructure exposed
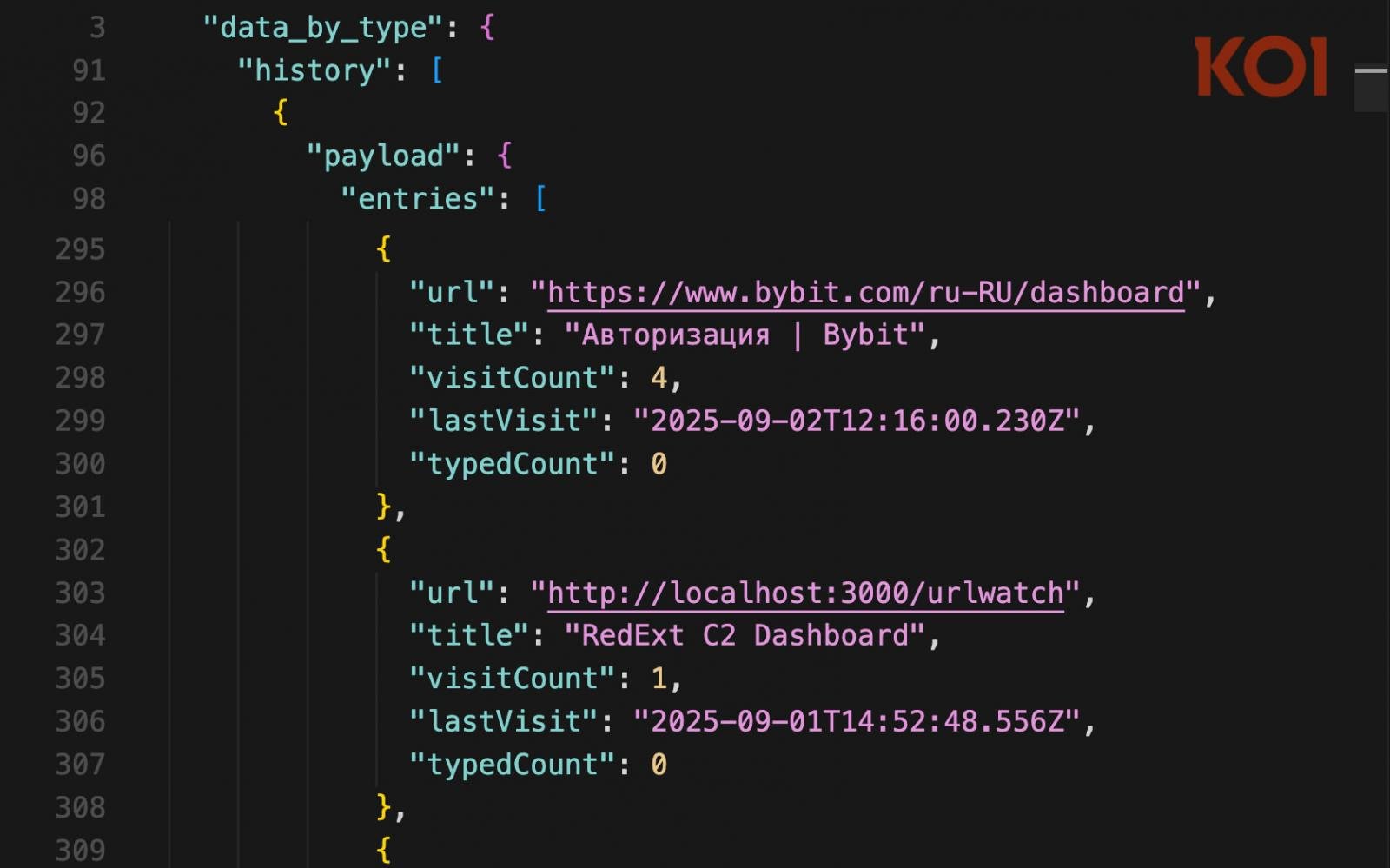
Through an anonymous tip, Koi Security was able to access the attackers’ server and obtain key data on the victims impacted by this campaign.
The retrieved data indicates global reach, with GlassWorm found on systems across the United States, South America, Europe, Asia, and a government entity in the Middle East.
Regarding the operators themselves, Koi reports they are Russian-speaking and use the RedExt open-source C2 browser extension framework.
Source: Koi Security
The researchers shared all data with law enforcment, including user IDs for multiple cryptocurrency exchanges and messaging platforms, and a plan to inform impacted organizations is being coordinated.
Koi Security told BleepingComputer that they have identified 60 distinct victims so far, noting that they retrieved only a partial list from a single exposed endpoint.
As of writing, the three extensions with the GlassWorm payload remain available for download on OpenVSX.
It’s budget season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
Source link



