Hackers retain access to patched FortiGate VPNs using symlinks

Fortinet warns that threat actors use a post-exploitation technique that helps them maintain read-only access to previously compromised FortiGate VPN devices even after the original attack vector was patched.
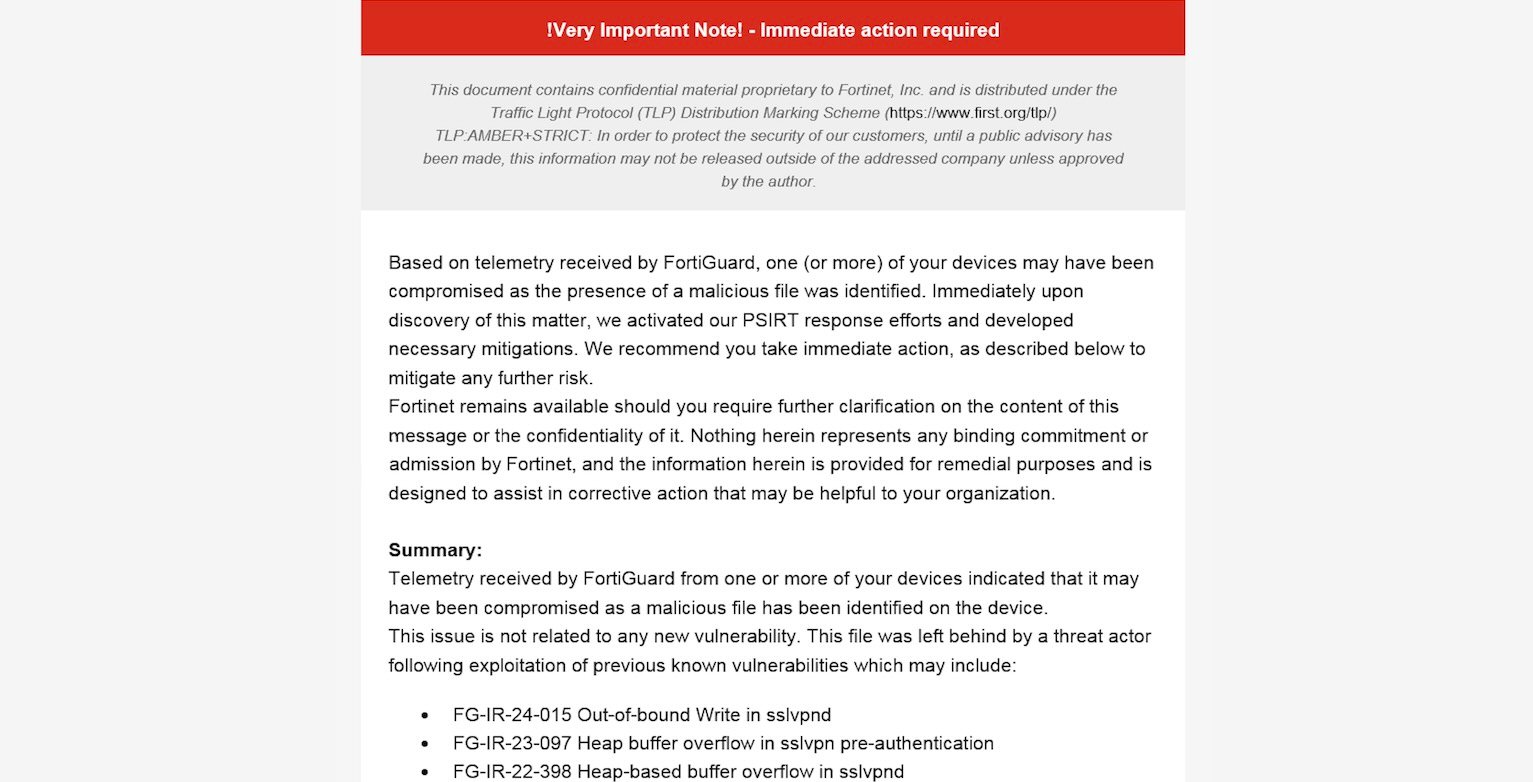
Earlier this week, Fortinet began sending emails to customers warning that their FortiGate/FortiOS devices were compromised based on telemetry received from FortiGuard devices.
These emails were titled “Notification of device compromise – FortiGate / FortiOS – ** Urgent action required **,” given a TLP:AMBER+STRICT designation.
“This issue is not related to any new vulnerability. This file was left behind by a threat actor following exploitation of previous known vulnerabilities,” the emails said, including but not limited to CVE-2022-42475, CVE-2023-27997, and CVE-2024-21762.
After BleepingComputer contacted Fortinet with questions about these emails, the company released an advisory on Thursday warning about this new exploitation technique. The advisory says that when the threat actors previously breached servers using older vulnerabilities, they created symbolic links in the language files folder to the root file system on devices with SSL-VPN enabled.
This allows them to maintain read-only access to the root filesystem through the publicly accessible SSL-VPN web panel even after they’re discovered and evicted.
“A threat actor used a known vulnerability to implement read-only access to vulnerable FortiGate devices. This was achieved via creating a symbolic link connecting the user filesystem and the root filesystem in a folder used to serve language files for the SSL-VPN. This modification took place in the user filesystem and avoided detection,” Fortinet says.
“Therefore, even if the customer device was updated with FortiOS versions that addressed the original vulnerabilities, this symbolic link may have been left behind, allowing the threat actor to maintain read-only access to files on the device’s file system, which may include configurations.”
Attacks go back to early 2023
While Fortinet didn’t reveal the exact timeframe of these attacks, the Computer Emergency Response Team of France (CERT-FR), part of the country’s National Agency for the Security of Information Systems (ANSSI), revealed on Thursday that this technique has been used in a massive wave of attacks going back to early 2023.
“CERT-FR is aware of a massive campaign involving numerous compromised devices in France. During incident response operations, CERT-FR has learned of compromises occurring since early 2023,” CERT-FR said.
Today, CISA also advised network defenders to report any incidents and anomalous activity related to Fortinet’s report to its 24/7 Operations Center at Report@cisa.gov or (888) 282-0870.
In the emails sent earlier this week, Fortinet advised customers to immediately upgrade their FortiGuard firewalls to the latest version of FortiOS (7.6.2, 7.4.7, 7.2.11, 7.0.17, 6.4.16) to remove the malicious files used for persistence.
Admins were also urged to review device configurations immediately and focus on finding any unexpected changes. This support document provides further guidance on resetting potentially exposed credentials on compromised devices.
CERT-FR also recommended isolating compromised VPN devices from the network, resetting all secrets (credentials, certificates, identity tokens, cryptographic keys, etc), and searching for evidence of lateral network movement.
Source link












