iCloud Calendar abused to send phishing emails from Apple’s servers

iCloud Calendar invites are being abused to send callback phishing emails disguised as purchase notifications directly from Apple’s email servers, making them more likely to bypass spam filters to land in targets’ inboxes.
Earlier this month, a reader shared an email with BleepingComputer that claimed to be a payment receipt for $599 charged against the recipient’s PayPal account. This email included a phone number if the recipient wanted to discuss the payment or make changes to it.
“Hello Customer, Your PayPal account has been billed $599.00. We’re confirming receipt of your recent payment,” read the email.
“If you wish to discuss or make changes to this payment, please contact our support team at +1 +1 (786) 902-8579. Contact us to cancel +1 (786) 902-8579,” continued the email.
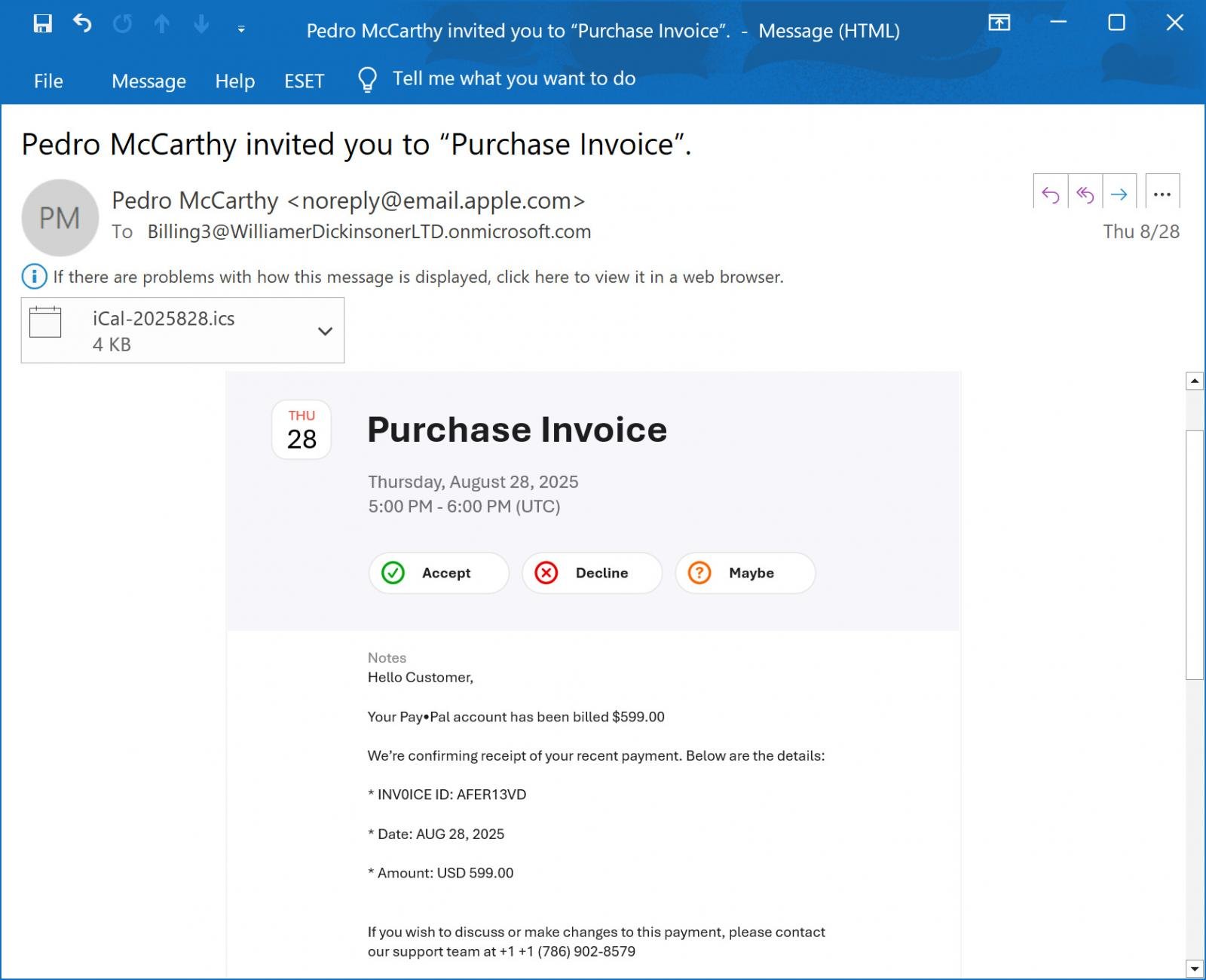
Source: BleepingComputer
The goal of these emails is to trick recipients into thinking their PayPal account was fraudulently charged to make a purchase and scare the email recipient into calling the scammer’s “support” phone number.
When calling the number, a scammer will try to scare you into thinking your account was hacked or that they need to connect to your computer to initiate a refund, asking you to download and run software.
However, in previous scams like this, this remote access was used to steal money from bank accounts, deploy malware, or steal data from the computer.
Abusing iCloud Calendar invites to send emails
The lure in this email is a typical callback phishing scam, but what was strange was that it was sent from noreply@email.apple.com, passing the SPF, DMARC, and DKIM email security checks, signifying that it legitimately came from Apple’s mail server.
Authentication-Results: spf=pass (sender IP is 17.23.6.69)
smtp.mailfrom=email.apple.com; dkim=pass (signature was verified)
header.d=email.apple.com;dmarc=pass action=none header.from=email.apple.com;
As you can see from the above phishing email, this email is actually an iCloud Calendar invite, where the threat actor included the phishing text within the Notes field and then invited a Microsoft 365 email address that they controlled.
When the iCloud Calendar event is created and external people are invited, an email invitation is sent from Apple’s servers at email.apple.com from the iCloud Calendar owner’s name with the email address “noreply@email.apple.com”
In the email seen by BleepingComputer, the invitation is addressed to a Microsoft 365 account, “Billing3@WilliamerDickinsonerLTD.onmicrosoft.com”.
Similar to a previous phishing campaign that utilized PayPal’s “New Address” feature, it is believed that the Microsoft 365 email address to which the invite is sent is actually a mailing list that automatically forwards any email it receives to all other group members.
In this case, the mailing list members are the targets of the phishing scam.
As the email was initially initiated from Apple’s email servers, if it is forwarded by Microsoft 365, it would usually fail SPF email checks.
To prevent this, Microsoft 365 uses the Sender Rewriting Scheme (SRS) to rewrite the Return path to an address associated with Microsoft, allowing it to pass SPF checks.
Original Return-Path: noreply@email.apple.com
Rewritten Return-Path: bounces+SRS=8a6ka=3I@williamerdickinsonerltd.onmicrosoft.com
While there is nothing particularly special about the phishing lure itself, the abuse of the legitimate iCloud Calendar invite feature, Apple’s email servers, and an Apple email address adds a sense of legitimacy to the email and also allows it to potentially bypass spam filters as it comes from a trusted source.
As a general rule, if you receive an unexpected Calendar invite with a strange message within it, it should be treated with caution.
BleepingComputer contacted Apple about this scam, but did not receive a response to our email.
46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.
Source link


