Ivanti fixes three critical flaws in Connect Secure & Policy Secure

Ivanti has released security updates for Ivanti Connect Secure (ICS), Ivanti Policy Secure (IPS), and Ivanti Secure Access Client (ISAC) to address multiple vulnerabilities, including three critical severity problems.
The company learned about the flaws through its responsible disclosure program from security researchers at CISA and Akamai, and through the HackerOne bug bounty platform.
Ivanti notes in the security bulletin that it received no reports about any of the issues being actively exploited in the wild. However, it it recommends that users install the security updates as soon as possible.
The three critical security vulnerabilities Ivanti patched are the following:
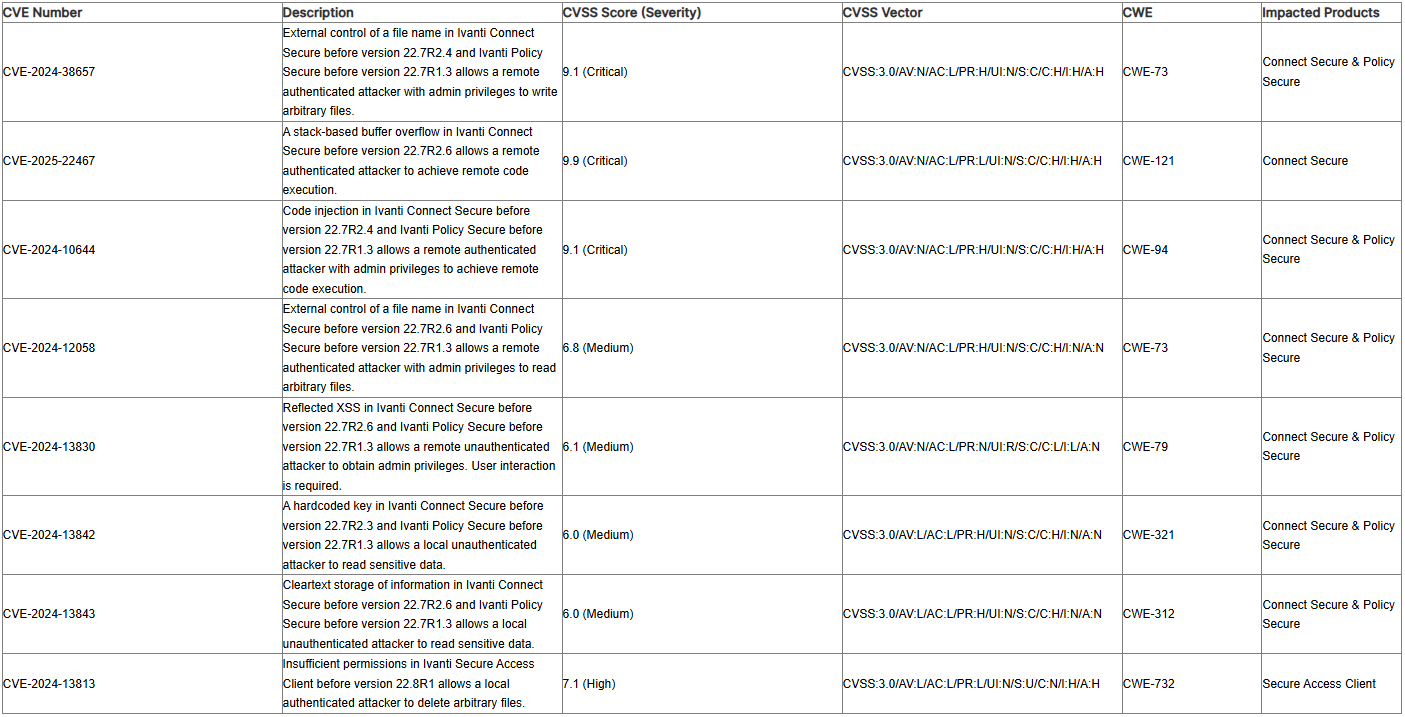
- CVE-2025-22467: Stack-based buffer overflow in ICS allows remote authenticated attackers with low privileges to execute code. (critical severity score of 9.9)
- CVE-2024-38657: External control of a filename enables remote authenticated attackers to perform arbitrary file writing in ICS and IPS. (critical severity score of 9.1)
- CVE-2024-10644: Code injection vulnerability enables remote authenticated attackers remote code execution in ICS and IPS. (critical severity score of 9.1)
Exploiting any of the three issues is possible from a remote location but an attacker needs to be authenticated. Furthermore, for two of them admin privileges are necessary to achieve remote code execution or to write arbitrary files.
Despite this, the risk is still considerable as insider threats or attackers who have stolen credentials via phishing, previous breaches, or via brute forcing passwords, can still leverage the flaws for malicious operations.
There are also five more flaws included in the bulletin, ranging from medium to high severity. Issues include cross-site scripting (XSS) issues, hardcoded keys, cleartext storage of sensitive data, and insufficient permissions.
The vulnerabilities impact ICS 22.7R2.5 and older, IPS 22.7R1.2 and older, and ISAC 22.7R4 and below. Details about which products are impacted by each flaw can be seen in the table below.
The issues were addressed in ICS version 22.7R2.6, IPS version 22.7R1.3, and ISAC 22.8R1, which are the recommended upgrade targets for system administrators.
Ivanti has also acknowledged that the issue also impacts Pulse Connect Secure 9.x, but stated it does not plan to offer fixes for these products as their support period has ended,
“The Pulse Connect Secure 9.x version of the product reached End of Engineering June 2024 and has reached End-of-Support as of December 31, 2024,” Ivanti explains.
“Because of this, the 9.x version of Connect Secure no longer receives backported fixes,” the company added, encouraging customers to upgrade to version 22.7 of Ivanti Connect Secure.
Ivanti has not provided any mitigations for the patched flaws and applying the latest update is the recommended solution.
Source link