Latrodectus malware and how to defend against it with Wazuh

Latrodectus is a versatile malware family that employs advanced tactics to infiltrate systems, steal sensitive data, and evade detection. Named after the black widow spider genus “Latrodectus”, this malware behaves with similar stealth and aggression.
It targets various systems, including corporate networks, financial institutions, and individual users. Its ability to morph and adapt is a concern for cybersecurity professionals worldwide.
Latrodectus has been observed in multiple malicious campaigns since late 2023, often linked to threat actors TA577 and TA578, who previously distributed IcedID malware.
Initially spotted in phishing campaigns, Latrodectus has emerged as a successor to IcedID, sharing similar tactics for initial access and data theft. The malware has been deployed in various campaigns targeting corporate networks and financial institutions to carry out data exfiltration and ransomware operations.
In this article, we will explore the nature of Latrodectus malware, how it operates, and, most importantly, how organizations can defend against it.
Analysis of Latrodectus malware
An analysis of its structure reveals a modular malware built to maximize disruption and theft while maintaining persistence. Below, we explore the key behaviors of Latrodectus, grounded in actual analyses of its tactics and techniques.
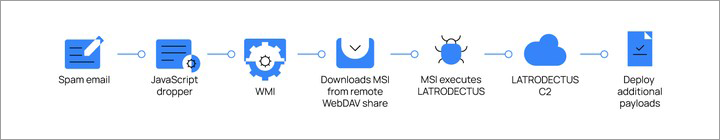
- Initial access via fileless techniques: Latrodectus often arrives through phishing emails with malicious attachments or links. Upon execution, the malware injects malicious scripts directly into memory, bypassing traditional file-based security solutions.
- Dynamic API resolution: The malware dynamically resolves Windows API functions by hashing function names like kernel32.dll and ntdll.dll, a technique that complicates reverse engineering and static detection. Latrodectus obfuscates these imports and then uses CRC32 checksums at runtime to resolve them from the Process Environment Block (PEB). This includes core modules like kernel32.dll and ntdll.dll and expands to other modules like user32.dll and wininet.dll, which are resolved through wildcard searches in the system directory.
- Code obfuscation and packing: Latrodectus employs packing techniques to compress its payload into smaller components. It encrypts strings and hides key functions, reducing the chances that static analysis will reveal its malicious nature. Recent samples use a simplified string decryption routine, shifting from a complex pseudo-random number generator (PRNG) to a more efficient XOR-based routine.
- Persistence mechanisms: After infection, Latrodectus replicates itself to a hidden system location, commonly *%AppData%*, and ensures persistence by creating scheduled tasks like C:\Windows\System32\Tasks\system_update to launch after reboots.
- Environment evasion: Before loading its payload, Latrodectus checks for virtualization environments by examining several system attributes. It assesses the number of active processes on the machine, requiring at least 75 processes on Windows 10 systems to avoid being flagged as running in a sandbox. Additionally, it checks for hardware attributes such as MAC addresses to detect virtual machines. Specifically, it calls GetAdaptersInfo() from iphlpapi.dll to verify the system has a valid MAC address. If no valid MAC address is found or the system falls short of the expected hardware setup, the malware will terminate to avoid detection.
- Mutex usage: The malware creates a mutex named “runnung”, which allows it to check if it is already running on the infected system. If this mutex exists, the malware halts further execution to avoid duplicating the infection.
- Command-and-Control (C2) communication: Latrodectus establishes secure communication with its C2 servers over encrypted HTTPS. It sends an initial POST request containing system details like the operating system, architecture, and a unique Bot ID. The Bot ID is derived from the infected machine’s serial number using a hashing algorithm, ensuring each infected endpoint has a distinct identifier. Latrodectus also periodically updates its C2 infrastructure, rotating domains to avoid detection. These domains are typically encrypted and only decrypted during runtime, making it harder for network-based detection systems to track or block the C2 communication.
- The malware then awaits further instructions, which include downloading additional payloads or exfiltrating data.
Source: Wazuh
The impact of Latrodectus malware
The modular design of the Latrodectus malware allows it to adapt its capabilities depending on the attacker’s objectives and the system it has compromised. These capabilities include selective data theft, where the malware targets specific data types to exfiltrate, alongside system reconnaissance and, occasionally, ransomware functions.
- Selective data theft: The malware scans for specific data types, such as credentials stored in web browsers, sensitive personal identification files, and corporate documents. It minimizes the data transferred to avoid detection and only exfiltrates what it identifies as valuable.
- Modular expansion: The initial Latrodectus payload acts as a downloader, which the C2 server can instruct to pull additional modules. These modules may perform various functions, including keylogging, network scanning, and further data exfiltration. This modular design makes the malware highly flexible, allowing it to evolve based on the attacker’s changing objectives.
How to defend against the Latrodectus malware
Preventing Latrodectus infections requires a multi-layered approach that includes proactive defenses, awareness, and regular updates to security systems. Below are some key defense strategies:
- Phishing awareness and training: Latrodectus often infiltrates through phishing emails, so training employees to spot and avoid these threats is crucial. Regular phishing simulations help maintain vigilance against suspicious emails, reducing risks from social engineering attacks.
- Strengthen endpoint security: Using updated antivirus and anti-malware tools is essential for early detection. Advanced solutions that monitor endpoint behavior for anomalies can identify threats like Latrodectus before they spread.
- Implement network segmentation: Segmenting networks limit malware movement within an organization. Isolating critical systems from broader access reduces the risk of unauthorized access and helps contain potential breaches.
- Maintain regular backup practices: With Latrodectus’s file encryption tactics, secure and regular backups are important. Storing backups in isolated environments ensures data can be restored without paying ransoms.
- Establish a strong patch management strategy: Regularly updating software closes vulnerabilities that malware like Latrodectus may exploit. A disciplined patch management process ensures security gaps are quickly addressed.
How Wazuh can detect and defend against Latrodectus malware
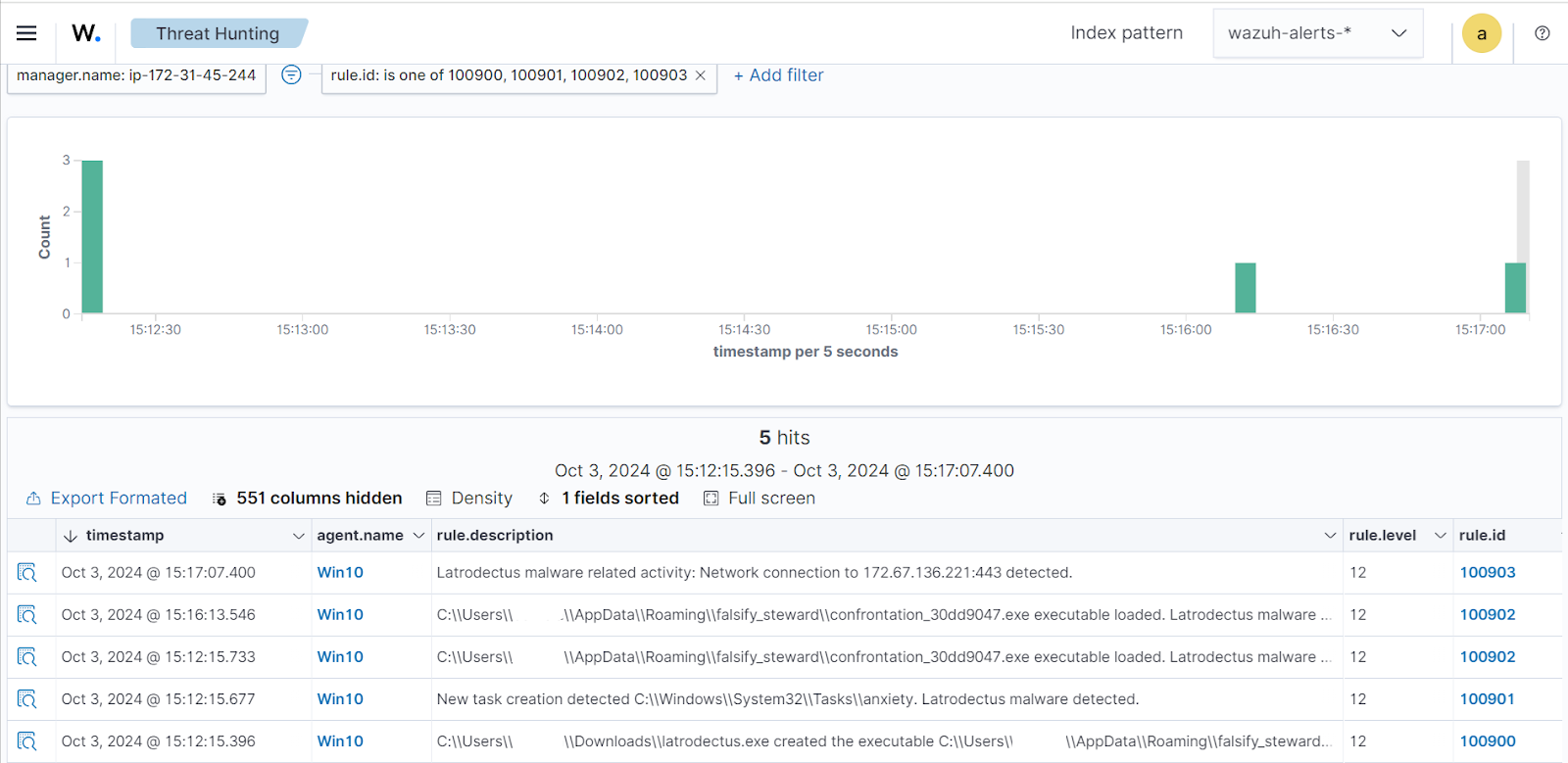
Wazuh provides a solution for detecting and responding to malware like Latrodectus.
With its real-time monitoring, threat detection, and log analysis capabilities, Wazuh can identify suspicious activities that indicate the presence of Latrodectus malware, such as unusual file modifications, encrypted data, or unauthorized access attempts.
Source: Wazuh
Read this detailed blog post on detecting Latrodectus malware for a deeper look into how Wazuh can defend against it.
Sponsored and written by Wazuh.
Source link