New details reveal how hackers hijacked 35 Google Chrome extensions

New details have emerged about a phishing campaign targeting Chrome browser extension developers that led to the compromise of at least thirty-five extensions to inject data-stealing code, including those from cybersecurity firm Cyberhaven.
Although initial reports focused on Cyberhaven’s security-focused extension, subsequent investigations revealed that the same code had been injected into at least 35 extensions collectively used by roughly 2,600,000 people.
From reports on LinkedIn and Google Groups from targeted developers, the latest campaign started around December 5th, 2024. However, earlier command and control subdomains found by BleepingComputer existed as far back as March 2024.
“I just wanted to alert people to a more sophisticated phishing email than usual that we got that stated a Chrome Extension policy violation of the form: ‘Unnecessary details in the description’,” reads the post to Google Group’s Chromium Extension’s group.
“The link in this email looks like the webstore but goes to a phishing website that will try to take control of your chrome extension and likely update it with malware.”
A deceptive OAuth attack chain
The attack begins with a phishing email sent to Chrome extension developers directly or through a support email associated with their domain name.
From emails seen by BleepingComputer, the following domains were used in this campaign to send the phishing emails:
supportchromestore.com
forextensions.com
chromeforextension.com
The phishing email, which is made to appear as if it comes from Google, claims that the extension is in violation of Chrome Web Store policies and is at risk of being removed.
“We do not allow extensions with misleading, poorly formatted, non-descriptive, irrelevant, excessive, or inappropriate metadata, including but not limited to the extension description, developer name, title, icon, screenshots, and promotional images,” reads the phishing email.
Specifically, the extension’s developer is led to believe their software’s description contains misleading information and must agree to the Chrome Web Store policies.
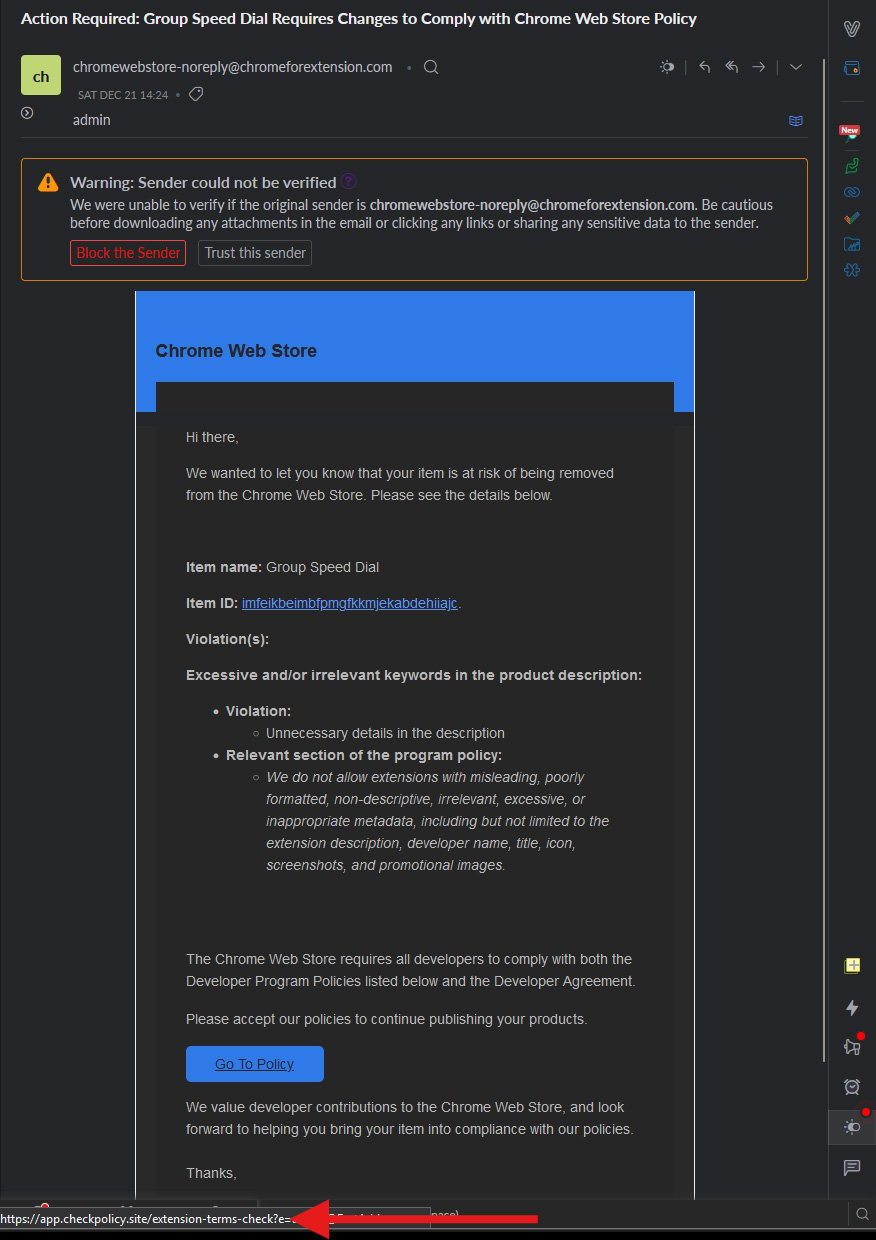
Source: Google Groups
If the developer clicks on the embedded ‘Go To Policy’ button in an effort to understand what rules they have violated, they are taken to a legitimate login page on Google’s domain for a malicious OAuth application.
The page is part of Google’s standard authorization flow, designed for securely granting permissions to third-party apps to access specific Google account resources.
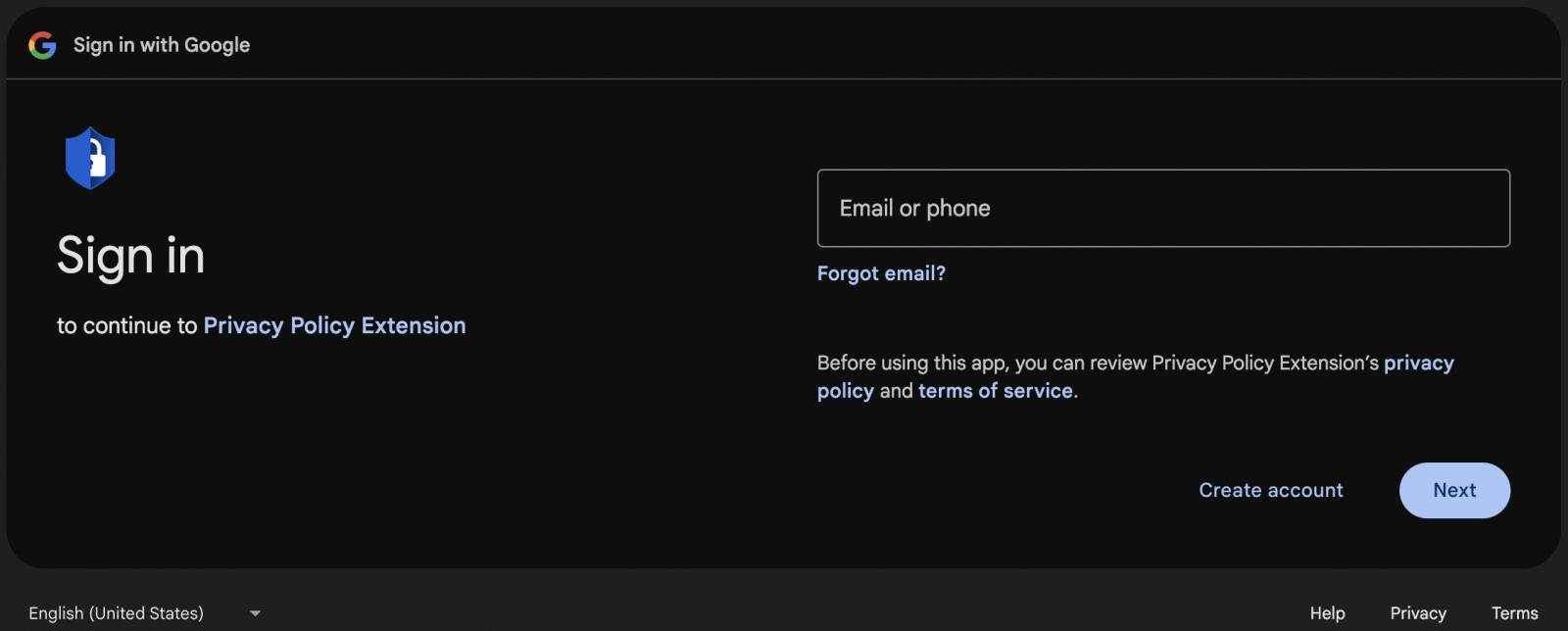
Source: Cyberhaven
On that platform, the attacker hosted a malicious OAuth application named “Privacy Policy Extension” that asked the victim to grant permission to manage Chrome Web Store extensions through their account.
“When you allow this access, Privacy Policy Extension will be able to: See, edit, update, or publish your Chrome Web Store extensions, themes, apps, and licenses you have access to,” reads the OAuth authorization page.
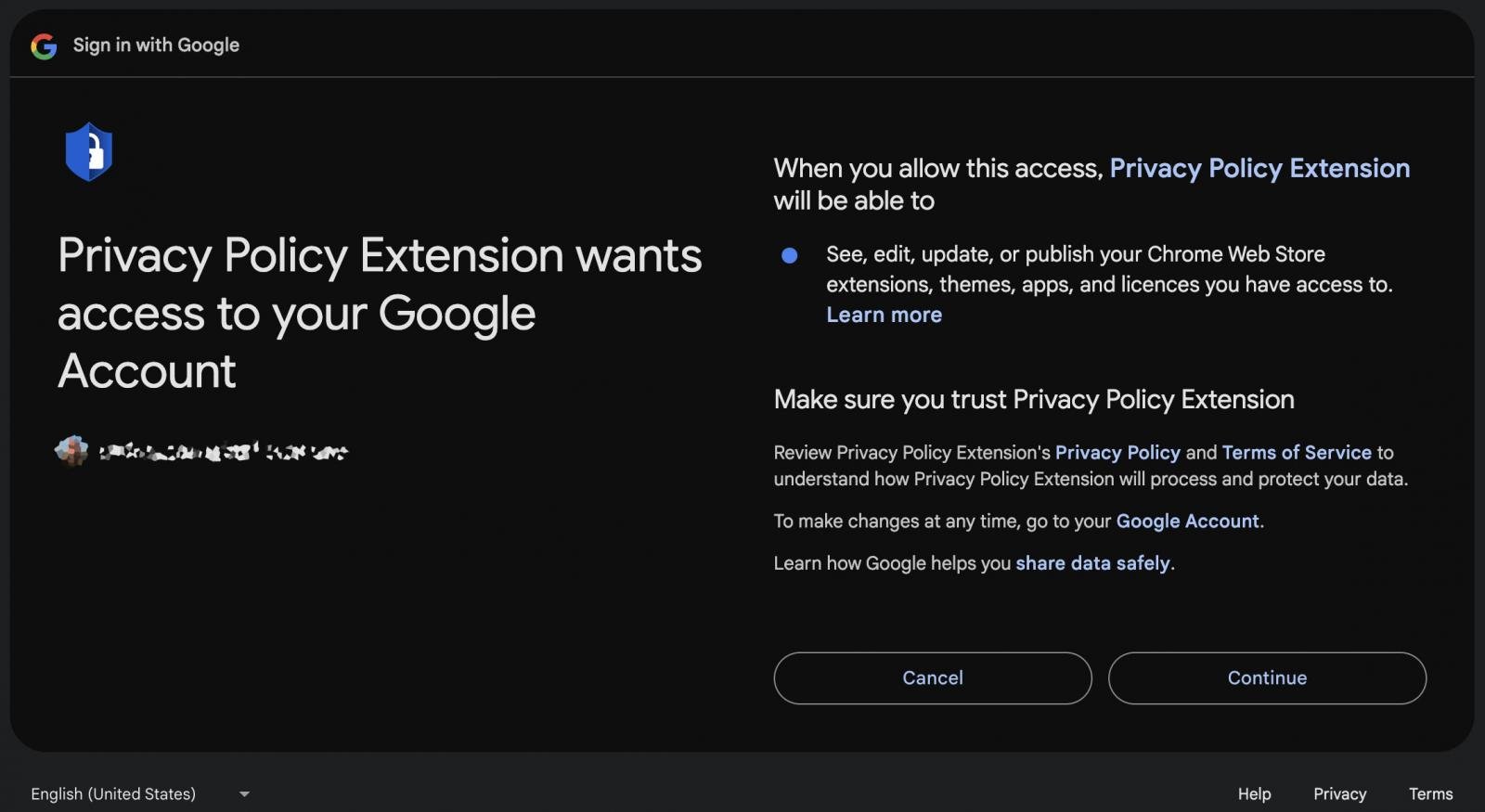
Source: Cyberhaven
Multi-factor authentication didn’t help protect the account as direct approvals in OAuth authorization flows aren’t required, and the process assumes the user fully understands the scope of permissions they’re granting.
“The employee followed the standard flow and inadvertently authorized this malicious third-party application,” explains Cyberhaven in a post-mortem writeup.
“The employee had Google Advanced Protection enabled and had MFA covering his account. The employee did not receive an MFA prompt. The employee’s Google credentials were not compromised.”
Once the threat actors gained access to the extension developer’s account, they modified the extension to include two malicious files, namely ‘worker.js’ and ‘content.js,’ which contained code to steal data from Facebook accounts.
The hijacked extension was then published as a “new” version on the Chrome Web Store.
While Extension Total is tracking thirty-five extensions impacted by this phishing campaign, IOCs from the attack indicate that a far greater number were targeted.
According to VirusTotal, the threat actors pre-registered domains for targeted extensions, even if they did not fall for the attack.
While most domains were created in November and December, BleepingComputer found that the threat actors were testing this attack in March 2024.
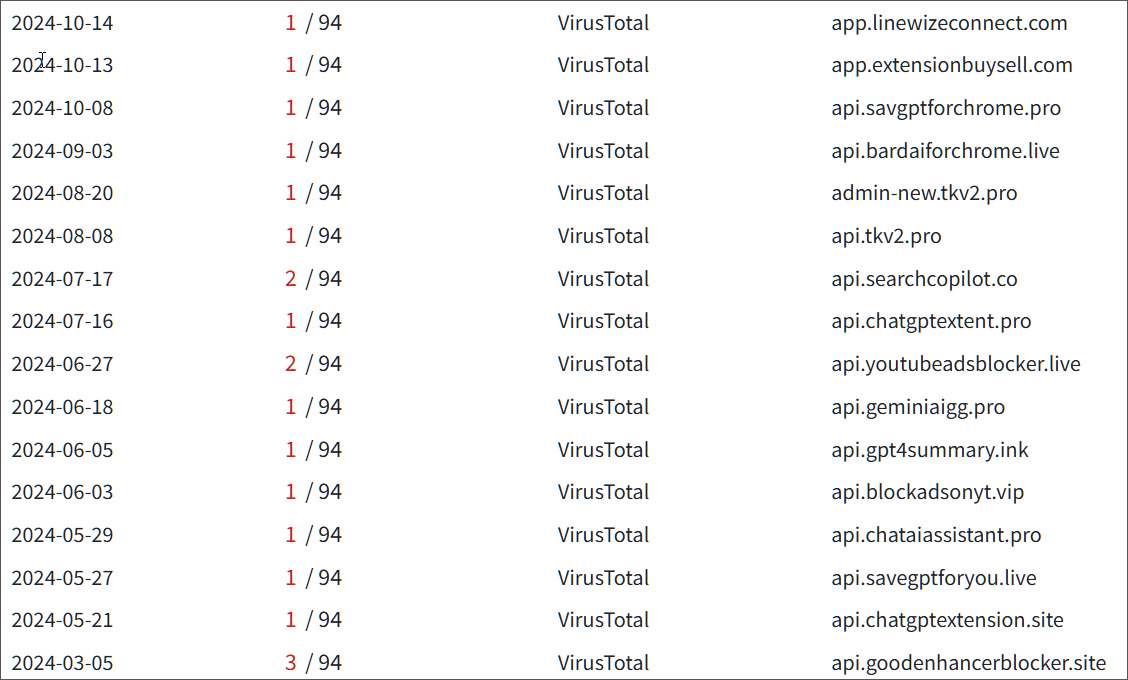
Source: BleepingComputer
Targeting Facebook business accounts
Analysis of compromised machines showed that the attackers were after the Facebook accounts of users of the poisoned extensions.
Specifically, the data-stealing code attempted to grab the user’s Facebook ID, access token, account info, ad account information, and business accounts.
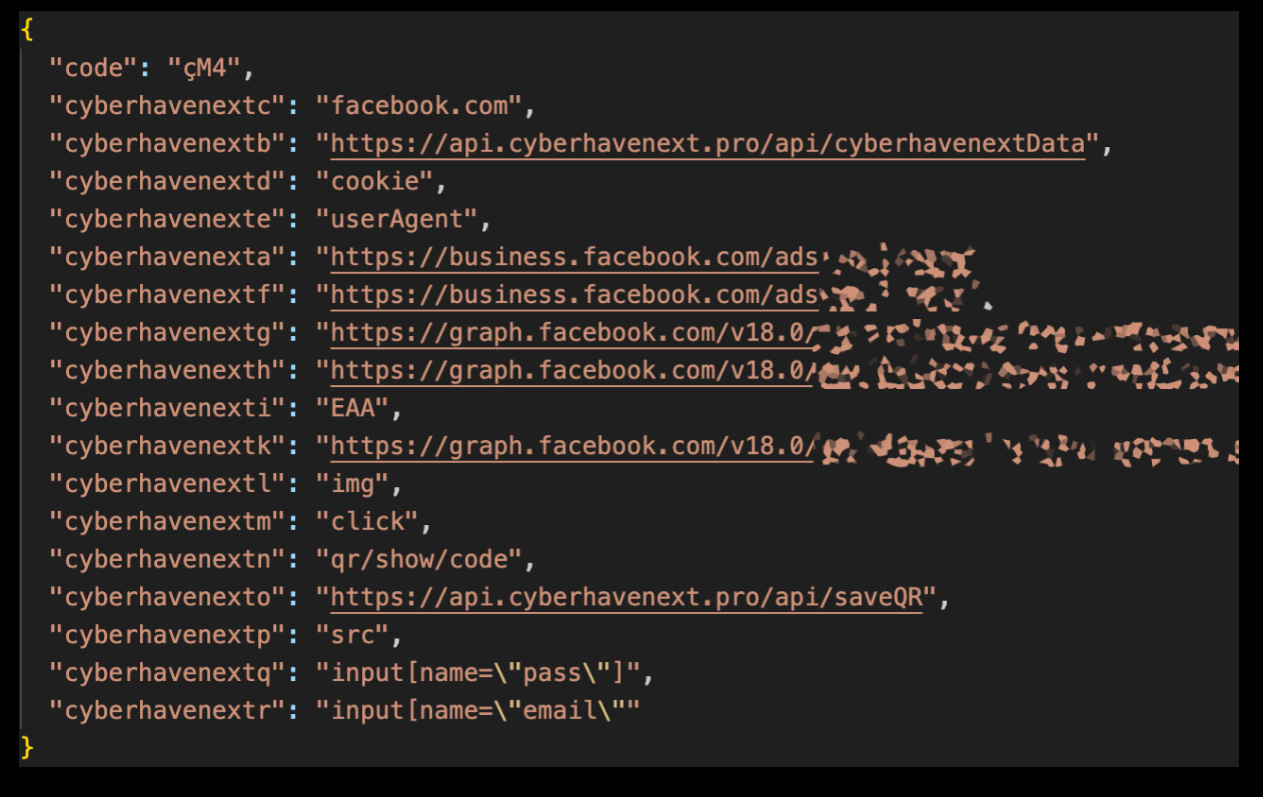
Source: Cyberhaven
Additionally, the malicious code added a mouse click event listener specifically for the victim’s interactions on Facebook.com, looking for QR code images related to the platform’s two-factor authentication or CAPTCHA mechanisms.
This aimed to bypass 2FA protections on the Facebook account and allow the threat actors to hijack it.
The stolen information would be packaged together with Facebook cookies, the user agent string, Facebook ID, and the mouse click events and exfiltrated to the attacker’s command and control (C2) server.
Threat actors have been targeting Facebook business accounts via various attack pathways to make direct payments from the victim’s credit to their account, run disinformation or phishing campaigns on the social media platform, or monetize their access by selling it to others.
Source link