New DoubleClickjacking attack exploits double-clicks to hijack accounts

A new variation of clickjacking attacks called “DoubleClickjacking” lets attackers trick users into authorizing sensitive actions using double-clicks while bypassing existing protections against these types of attacks.
Clickjacking, also known as UI redressing, is when threat actors create malicious web pages that trick visitors into clicking on hidden or disguised webpage elements.
The attacks work by overlaying a legitimate webpage in a hidden iframe over a web page created by the attackers. This attacker-created webpage is designed to align its buttons and links with links and buttons on the hidden iframe.
The attackers then use their web page to entice a user to click on a link or button, such as to win a reward or view a cute picture.
However, when they click on the page, they are actually clicking on links and buttons on the hidden iframe (the legitimate site), which could potentially perform malicious actions, such as authorizing an OAuth application to connect to their account or accepting an MFA request.
Over the years, web browser developers introduced new features that prevent most of these attacks, such as not allowing cookies to be sent cross-site or introducing security restrictions (X-Frame-Options or frame-ancestors) on whether sites can be iframed.
New DoubleClickjacking attack
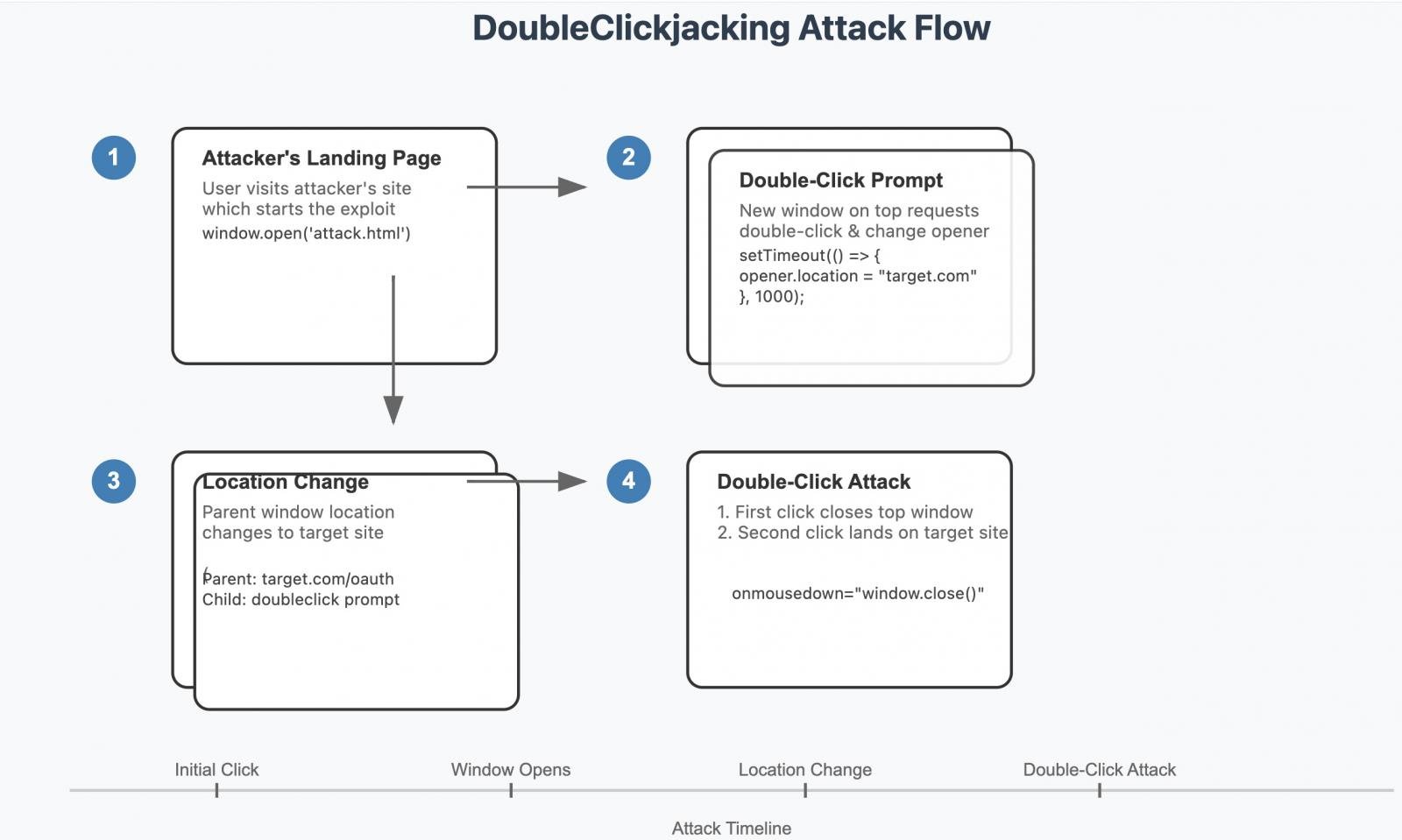
Cybersecurity expert Paulos Yibelo has introduced a new web attack called DoubleClickjacking that exploits the timing of mouse double-clicks to trick users into performing sensitive actions on websites.
In this attack scenario, a threat actor will create a website that displays a seemingly innocuous button with a lure, like “click here” to view your reward or watch a movie.
When the visitor clicks the button, a new window will be created that covers the original page and includes another lure, like having to solve a captcha to proceed. In the background, JavaScript on the original page will change that page to a legitimate site that the attackers want to trick a user into performing an action.
The captcha on the new, overlaid window prompts the visitor to double-click something on the page to solve the captcha. However, this page listens for the mousedown event, and when detected, quickly closes the captcha overlay, causing the second click to land on the now-displayed authorization button or link on the previously hidden legitimate page.
This causes the user to mistakenly click on the exposed button, potentially authorizing a plugin to be installed, an OAuth application to connect to their account, or a multi-factor authentication prompt to be acknowledged.
Source: Yibelo
What makes this so dangerous is that it bypasses all current clickjacking defenses as it is not using an iframe, it is not trying to pass cookies to another domain. Instead, the actions occur directly on legitimate sites that are not protected.
Yibelo says that this attack impacts almost every site, sharing demonstration videos utilizing DoubleClickjacking to take over Shopify, Slack, and Salesforce accounts.
The researcher also warns that the attack is not limited to web pages as it can be used for browser extensions as well.
“For example, I have made proof of concepts to top browser crypto wallets that uses this technique to authorize web3 transactions & dApps or disabling VPN to expose IP etc,” explains Yibelo.
“This can also be done in mobile phones by asking target to ‘DoubleTap’.”
To protect against this type of attack, Yibello shared JavaScript, which could be added to webpages to disable sensitive buttons until a gesture is made. This will prevent the double-click from automatically clicking on the authorization button when removing the attacker’s overlay.
The researcher also suggests a potential HTTP header that limits or blocks rapid context-switching between windows during a double-click sequence.
Source link