Pwn2Own hacking contest pays $1 million for WhatsApp exploit

The Zero Day Initiative is offering a $1 million reward to security researchers who will demonstrate a zero-click WhatsApp exploit at its upcoming Pwn2Own Ireland 2025 hacking contest.
The record bounty targets zero-click security flaws that allow code execution without user interaction on the messaging platform used by more than three billion people worldwide.
Meta, alongside Synology and QNAP, is co-sponsoring the Pwn2Own Ireland 2025 competition, which will take place from October 21 to October 24 in Cork, Ireland.
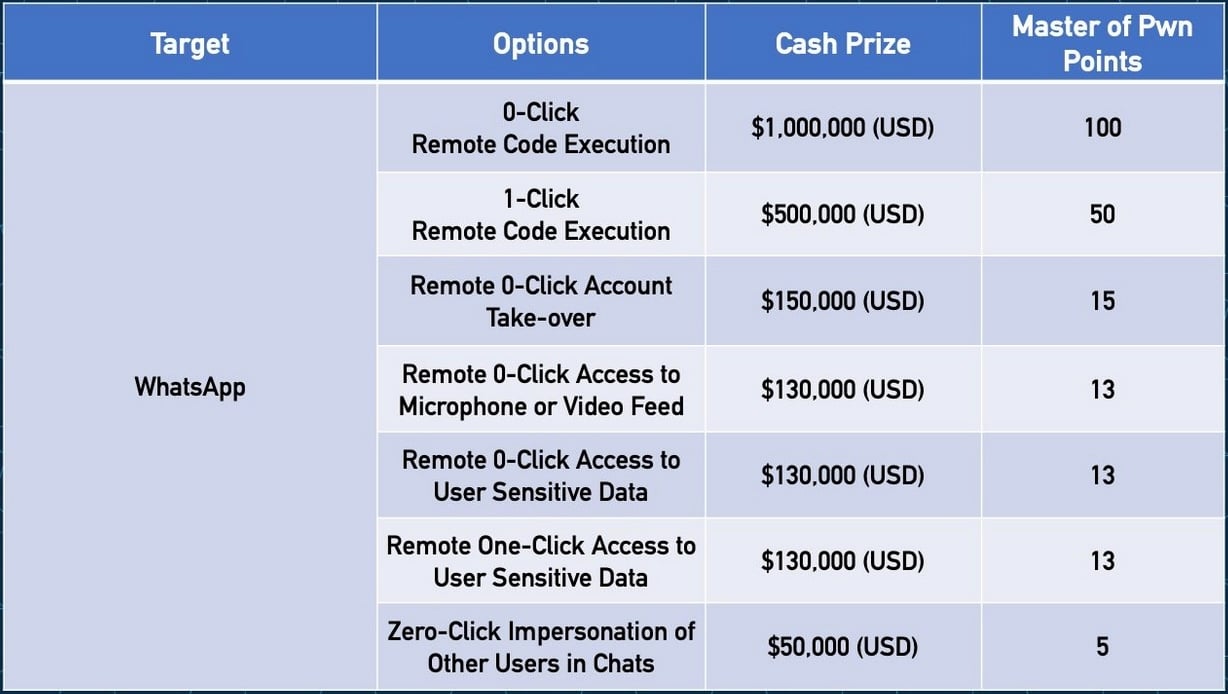
“As you might have guessed from the title, we’re excited to announce that Meta is co-sponsoring this year’s event, and they are hoping to see some great WhatsApp exploits. They are so excited for it, we’re putting up $1,000,000 for a 0-click WhatsApp bug that leads to code execution,” the Zero Day Initiative announced Thursday.
“We also will have lesser cash awards for other WhatsApp exploits, so be sure to check out the Messaging section for full details. We introduced this category last year, but no one attempted it. Perhaps a number with two commas will provide the needed motivation.”
The contest features eight categories targeting mobile phones, messaging apps, home networking equipment, smart home devices, printers, network storage systems, surveillance equipment, and wearable technology, including Meta’s Ray-Ban Smart Glasses and Quest 3/3S headsets, as well as Samsung Galaxy S25, Google Pixel 9, and Apple iPhone 16 flagship smartphones.
The ZDI has also expanded the attack vectors for the mobile category to include USB port exploitation for mobile devices, requiring contestants to compromise locked phones through physical connections. Traditional wireless protocols, such as Wi-Fi, Bluetooth, and near-field communication, remain valid attack methods.
Registration closes on October 16 at 5 p.m. Irish Standard Time, with the contest order determined by a random drawing. The Zero Day Initiative operates the event to identify vulnerabilities before malicious actors can exploit them, coordinating responsible disclosure with affected vendors.
After the flaws are exploited during Pwn2Own events, vendors have 90 days to release security updates before Trend Micro’s Zero Day Initiative publicly discloses them.
Last year’s Pwn2Own Ireland event awarded $1,078,750 for over 70 unique zero-day vulnerabilities, with Viettel Cyber Security collecting $205,000 for flaws demonstrated in QNAP NAS, Sonos speakers, and Lexmark printers.
Source link


