Russian hackers evolve malware pushed in “I am not a robot” captchas

The Russian state-backed Star Blizzard hacker group has ramped up operations with new, constantly evolving malware families (NoRobot, MaybeRobot) deployed in complex delivery chains that start with ClickFix social engineering attacks.
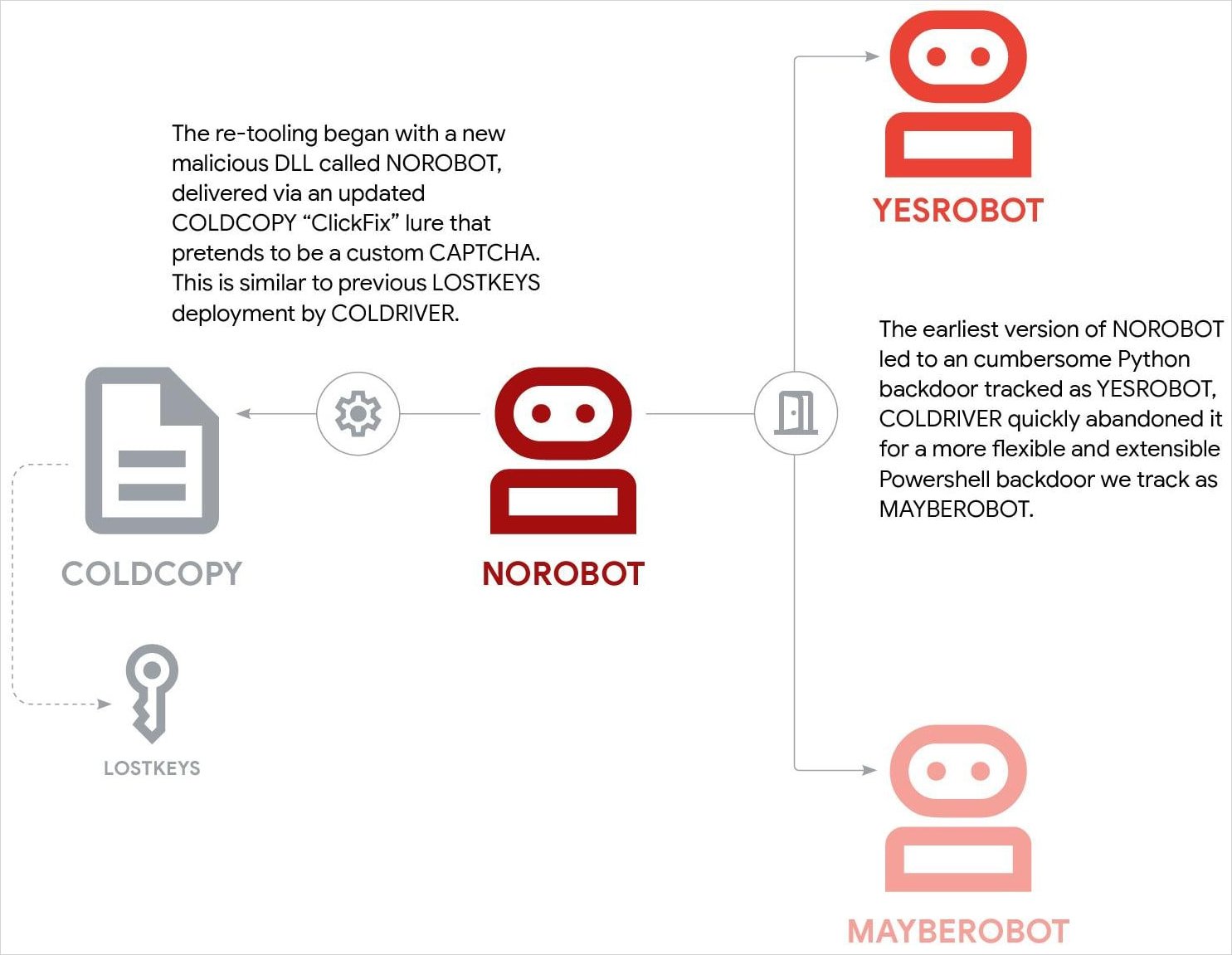
Also known as ColdRiver, UNC4057, and Callisto, the Star Blizzard threat group abandoned the LostKeys malware less than a week after researchers published their analysis and leveraged the *Robot malicious tools “more aggressively” than in any of its previous campaigns.
In a report in May, the Google Threat Intelligence Group (GTIG) said that it observed the LostKeys malware being leveraged in attacks on Western governments, journalists, think tanks, and non-governmental organizations.
The malware was used for espionage purposes, its capabilities including data exfiltration based on a hardcoded list of extensions and directories.
After publicly disclosing the LostKeys malware, GTIG researchers say that ColdRiver completely abandoned it and started to deploy new malicious tools, tracked as NOROBOT, YESROBOT, and MAYBEROBOT, in operations just five days later.
According to GTIG, the retooling started with NOROBOT, a malicious DLL delivered through “ClickFix” attacks involving fake CAPTCHA pages that tricked the target into executing it via rundll32 under the guise of a verification process.
The hackers try to trick the target into performing an “I am not a robot” a captcha challenge to prove they are human by executing a command that launches the NOROBOt malware.
.jpg)
Source: Google
Researchers at cloud security company Zscaler analyzed NOROBOT in September and named it BAITSWITCH, along with its payload, a backdoor they called SIMPLEFIX.
Google says that NOROBOT has been under constant development from May through September.
NOROBOT gains persistence through registry modifications and scheduled tasks, and initially retrieved a full Python 3.8 installation for Windows in preparation for the YESROBOT Python-based backdoor.
However, GTIG notes that YESROBOT’s use was short-lived, likely because the Python installation was an obvious artifact that would draw attention, as ColdRiver abandoned it for another backdoor, a PowerShell script called MAYBEROBOT (identified as SIMPLEFIX by Zscaler).
Since early June, a “drastically simplified” version of NOROBOT started to deliver MAYBEROBOT, which supports three commands:
- download and execute payloads from a specified URL
- execute commands through the command prompt
- execute arbitrary PowerShell blocks
After execution, MAYBEROBOT returns the results to distinct command-and-control (C2) paths, giving Coldriver feedback on operational success.
Source: Google
Google’s analysts comment that MAYBEROBOT’s development appears to have stabilized, with the threat actors now focusing more on refining NOROBOT to be stealthier and more effective.
The researchers noticed a shift from complex to simpler and then again to a complex delivery chain that splits cryptographic keys across multiple components. Decrypting the final payload depended on combining the pieces correctly, the researchers say.
“This was likely done to make it more difficult to reconstruct the infection chain because if one of the downloaded components was missing the final payload would not decrypt properly,” GTIG notes in the report.
ColdRiver attacks delivering NOROBOT and the subsequent payloads to targets of interest have been observed in attacks between June and September.
ColdRiver operations have been attributed to the Russian intelligence service (FSB). The group has been engaged in cyber-espionage activities since at least 2017. Despite efforts to obstruct its operations through infrastructure disruptions [1, 2], sanctions, and exposing its tactics, ColdRiver remains an active and evolving threat.
Typically, the threat group deploys malware in phishing attacks, and researchers have yet to find the reason for the hackers’ moving to ClickFix attacks.
One explanation could be that ColdRiver now uses the NOROBOT and MAYBEROBOT malware families on targets previously compromised through phishing and have already stolen emails and contacts. Re-targeting them may be ” to acquire additional intelligence value from information on their devices directly,” the researchers surmise
Google’s report lists indicators of compromise (IoCs) and YARA rules to help defenders detect Robot malware attacks.
Source link


