admin
-
Blog

ASUS Armoury Crate bug lets attackers get Windows admin privileges
A high-severity vulnerability in ASUS Armoury Crate software could allow threat actors to escalate their privileges to SYSTEM level on Windows machines. The security issue is tracked as CVE-2025-3464 and received a severity score of 8.8 out of 10. It could be exploited to bypass authorization and affects the AsIO3.sys of the Armoury Crate system management software. Armoury Crate is the official system…
Read More » -
Blog

Civil servants started using Microsoft Copilot to speed up admin tasks – here’s what they found
A pilot scheme testing the use of Microsoft Copilot in the public sector has saved civil servants nearly half an hour’s work per day, according to new figures. More than 20,000 people took part in the three-month trial, using Microsoft 365 Copilot to summarize long emails, update records, and prepare reports. Findings from the trial scheme showed users saved an…
Read More » -
Blog

Premium WordPress ‘Motors’ theme vulnerable to admin takeover attacks
A critical privilege escalation vulnerability has been discovered in the premium WordPress theme Motors, which allows unauthenticated attackers to hijack administrator accounts and take complete control of websites. Developed by StylemixThemes, Motors is one of the top-selling automotive themes for the WordPress platform. It is very popular among automotive businesses such as car dealerships, rental services, and used vehicle listing…
Read More » -
Blog

ASUS DriverHub flaw let malicious sites run commands with admin rights
The ASUS DriverHub driver management utility was vulnerable to a critical remote code execution flaw that allowed malicious sites to execute commands on devices with the software installed. The flaw was discovered by an independent cybersecurity researcher from New Zealand named Paul (aka “MrBruh“), who found that the software had poor validation of commands sent to the DriverHub background service.…
Read More » -
Blog

US indicts Black Kingdom ransomware admin for Microsoft Exchange attacks
A 36-year-old Yemeni national, who is believed to be the developer and primary operator of ‘Black Kingdom’ ransomware, has been indicted by the United States for conducting 1,500 attacks on Microsoft Exchange servers. The suspect, Rami Khaled Ahmed, is accused of deploying the Black Kingdom malware on roughly 1,500 computers in the United States and abroad, demanding ransom payments of $10,000…
Read More » -
Blog
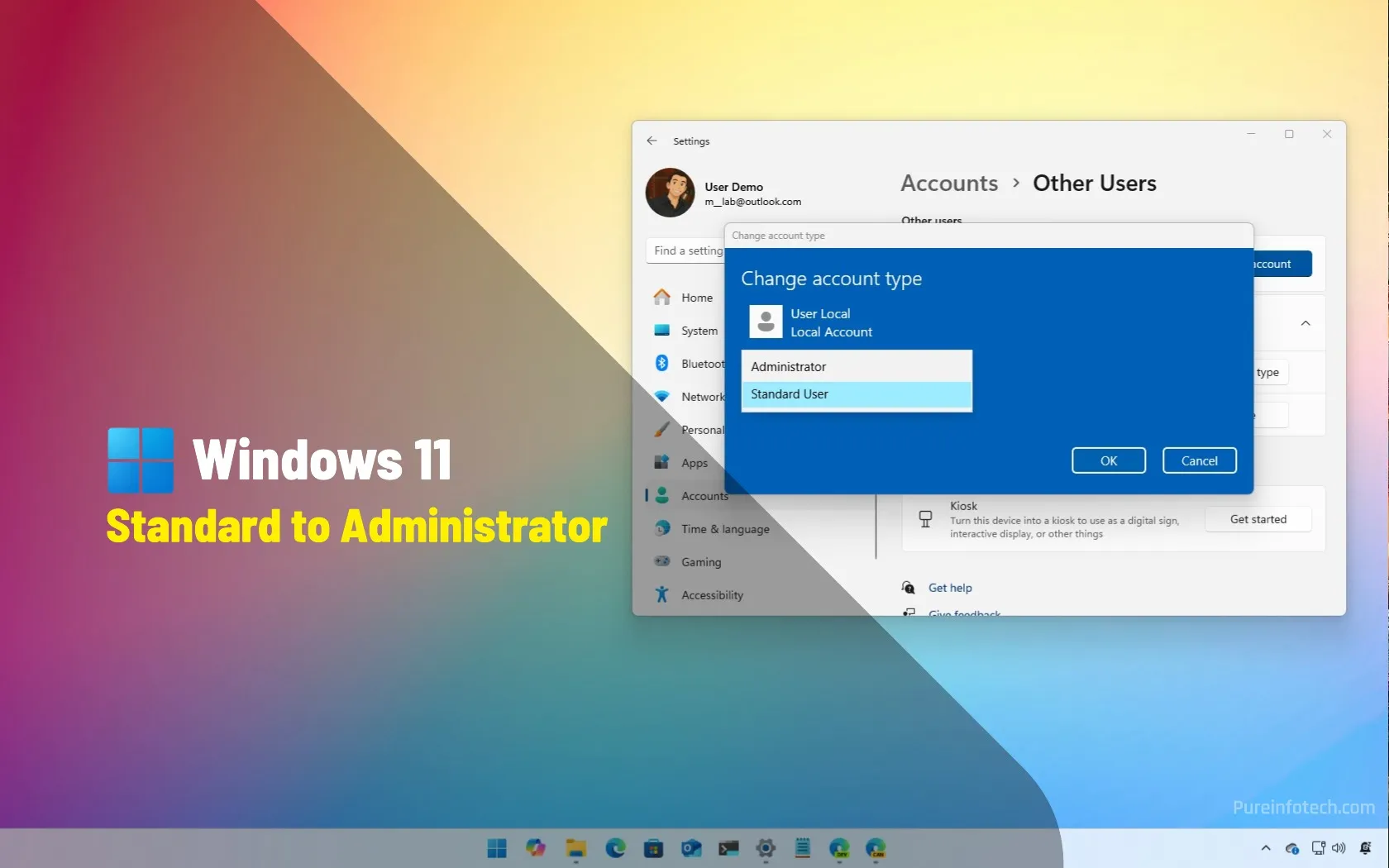
How to regain admin access from standard account on Windows 11
On Windows 11, if you lose access to your administrator account, you can still regain elevated access, and in this guide, I’ll show you how to complete this task. If you have a computer and accidentally deleted your administrator account, and now you only have a standard user account, you won’t be able to perform elevated tasks, such as making…
Read More » -
Blog

Landmark Admin data breach impact now reaches 1.6 million people
Landmark Admin has issued an update to its investigation of a cyberattack it suffered in May 2024, increasing the number of impacted individuals to 1.6 million. Landmark is a Texas-based third-party administrator (TPA) handling policy accounting, regulatory reporting, reinsurance support, and IT systems for major insurers nationwide like Liberty Bankers Life and American Benefit Life. In October 2024, the company…
Read More » -
Blog

Critical FortiSwitch flaw lets hackers change admin passwords remotely
Fortinet has released security patches for a critical vulnerability in its FortiSwitch devices that can be exploited to change administrator passwords remotely. The company says Daniel Rozeboom of the FortiSwitch web UI development team discovered the vulnerability (CVE-2024-48887) internally. Unauthenticated attackers can exploit this unverified FortiSwitch GUI password change security flaw (rated with a 9.8/10 severity score) in low-complexity attacks…
Read More » -
Blog

Garantex crypto exchange admin arrested while on vacation
Indian authorities arrested Aleksej Besciokov, the co-founder and one of the administrators of the Russian Garantex crypto-exchange while vacationing with his family in Varkala, India. As infosec journalist Brian Krebs first reported on Tuesday, the 46-year-old Lithuanian national and Russian resident was apprehended on Tuesday afternoon by Kerala state police officers under the country’s extradition law. Besciokov (aka “proforg” and…
Read More » -
Blog

DPRK hackers dupe targets into typing PowerShell commands as admin
North Korean state actor ‘Kimsuky’ (aka ‘Emerald Sleet’ or ‘Velvet Chollima’) has been observed using a new tactic inspired from the now widespread ClickFix campaigns. ClickFix is a social engineering tactic that has gained traction in the cybercrime community, especially for distributing infostealer malware. It involves deceptive error messages or prompts that direct victims to execute malicious code themselves, often…
Read More »

