bypasses
-
Blog

WinRAR flaw bypasses Windows Mark of the Web security alerts
A vulnerability in the WinRAR file archiver solution could be exploited to bypass the Mark of the Web (MotW) security warning and execute arbitrary code on a Windows machine. The security issue is tracked as CVE-2025-31334 and affects all WinRAR versions except the most recent release, which is currently 7.11. Mark of the Web is a security function in Windows…
Read More » -
Blog

New Ubuntu Linux security bypasses require manual mitigations
Three security bypasses have been discovered in Ubuntu Linux’s unprivileged user namespace restrictions, which could be enable a local attacker to exploit vulnerabilities in kernel components. The issues allow local unprivileged users to create user namespaces with full administrative capabilities and impact Ubuntu versions 23.10, where unprivileged user namespaces restrictions are enabled, and 24.04 which has them active by default. Linux…
Read More » -
Blog

Qualys discovers three bypasses of Ubuntu’s unprivileged user namespace restrictions
The Qualys Threat Research Unit (TRU) says it has uncovered three flaws in Ubuntu’s unprivileged user namespace restrictions that could allow a local attacker to gain full administrative capabilities. Linux distributions generally allow unprivileged users to create namespaces that help in creating containers and additional sandboxing functionality for programs such as container runtimes, but that also creates a weak spot.…
Read More » -
Blog

Time Bandit ChatGPT jailbreak bypasses safeguards on sensitive topics
A ChatGPT jailbreak flaw, dubbed “Time Bandit,” allows you to bypass OpenAI’s safety guidelines when asking for detailed instructions on sensitive topics, including the creation of weapons, information on nuclear topics, and malware creation. The vulnerability was discovered by cybersecurity and AI researcher David Kuszmar, who found that ChatGPT suffered from “temporal confusion,” making it possible to put the LLM…
Read More » -
Blog
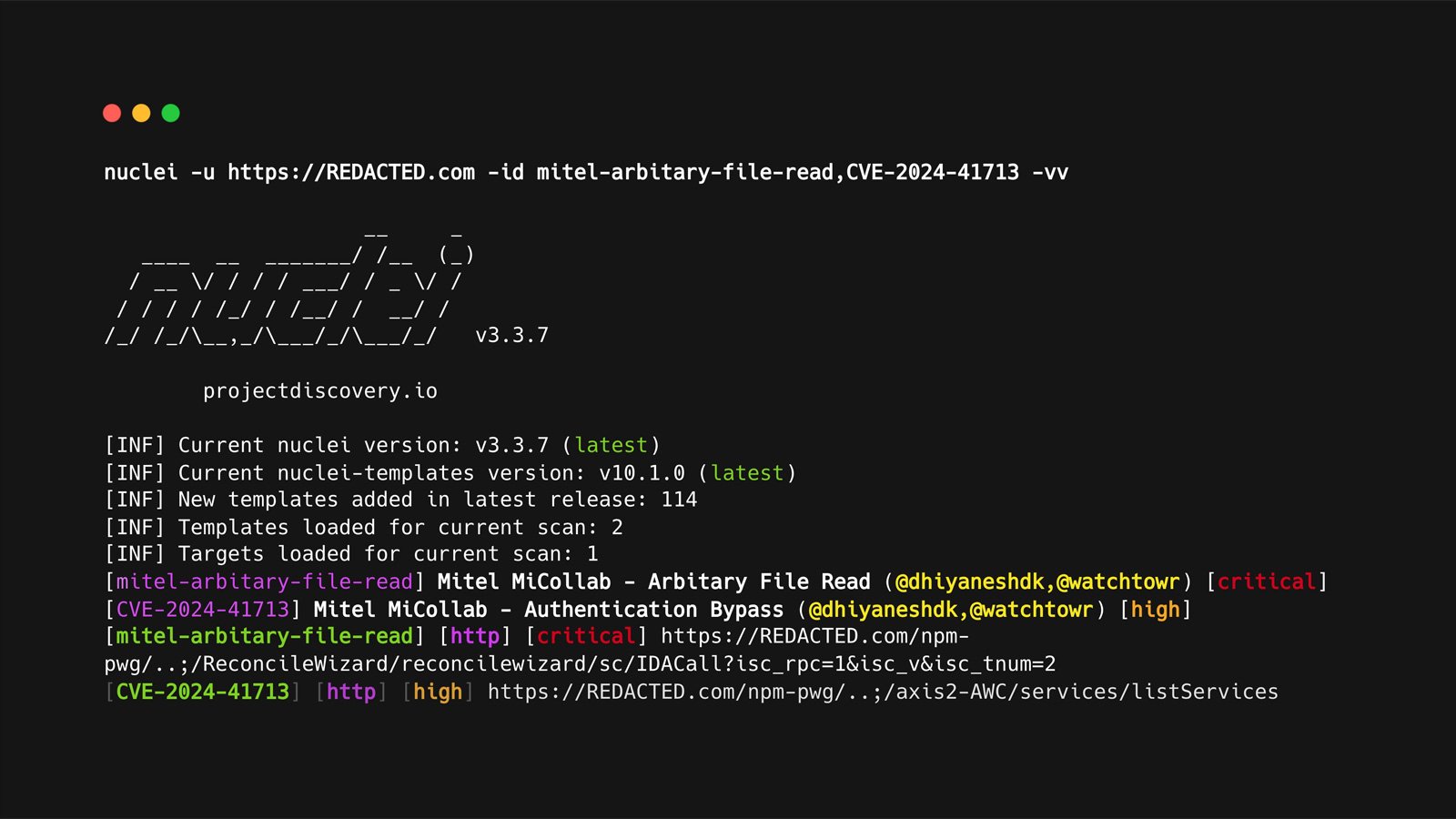
Nuclei flaw bypasses template signature checks to execute commands
A now-fixed vulnerability in the open-source vulnerability scanner Nuclei could potentially allow attackers to bypass signature verification while sneaking malicious code into templates that execute on local systems. Nuclei is a popular open-source vulnerability scanner created by ProjectDiscovery that scans websites for vulnerabilities and other weaknesses. The project utilizes a template-based scanning system of over 10,000 YAML templates that scan websites…
Read More » -
Blog

New tool bypasses Google Chrome’s new cookie encryption system
A researcher has released a tool to bypass Google’s new App-Bound encryption cookie-theft defenses and extract saved credentials from the Chrome web browser. The tool, named ‘Chrome-App-Bound-Encryption-Decryption,’ was released by cybersecurity researcher Alexander Hagenah after he noticed that others were already figuring out similar bypasses. Although the tool achieves what multiple infostealer operations have already added to their malware, its public…
Read More »

