devices
-
Blog
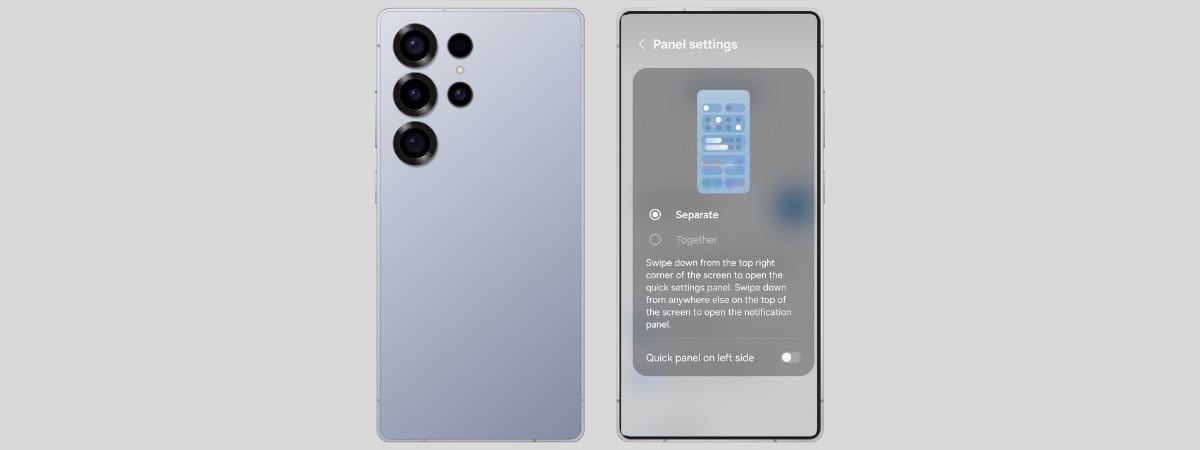
Get your Quick Settings and notifications back together on Samsung Galaxy devices
In its latest One UI 7.0 software update for Galaxy devices, Samsung decided to copy an iPhone feature that nobody asked for, separating Quick Settings from notifications. If you bought a Samsung Galaxy device with One UI 7.0 or newer, or you have an older smartphone or tablet that was updated to One UI 7.0, when you swipe down from…
Read More » -
Blog

KB5060533 update triggers boot errors on Surface Hub v1 devices
Microsoft is investigating a known issue that triggers Secure Boot errors and prevents Surface Hub v1 devices from starting up. These boot problems only impact Surface Hub v1 systems running Windows 10, version 22H2, after installing the KB5060533 June 2025 Windows security update. Microsoft says that “Surface Hub v1 devices might fail to start with the following error: ‘Secure Boot…
Read More » -
Blog

Score up to 20% off refurbished iPads, iPhones and Samsung Galaxy devices in Green Gadgets’ mega EOFY sale
Green Gadgets has a well-earned reputation as one of Australia’s top retailers of refurbished electronics, providing budget-conscious shoppers with a wide array of smartphones, tablets, laptops and desktop computers at prices that are far more affordable than buying new. If you’re under the impression that refurbished means old, think again — Green Gadgets carries all the latest tech, including current-gen…
Read More » -
Blog

New Mirai botnet infect TBK DVR devices via command injection flaw
A new variant of the Mirai malware botnet is exploiting a command injection vulnerability in TBK DVR-4104 and DVR-4216 digital video recording devices to hijack them. The flaw, tracked under CVE-2024-3721, is a command injection vulnerability disclosed by security researcher “netsecfish” in April 2024. The proof-of-concept (PoC) the researcher published at the time came in the form of a specially…
Read More » -
Blog

BADBOX 2.0 Android malware infects millions of consumer devices
The FBI is warning that the BADBOX 2.0 malware campaign has infected over 1 million home Internet-connected devices, converting consumer electronics into residential proxies that are used for malicious activity. The BADBOX botnet is commonly found on Chinese Android-based smart TVs, streaming boxes, projectors, tablets, and other Internet of Things (IoT) devices. “The BADBOX 2.0 botnet consists of millions of infected devices…
Read More » -
Blog
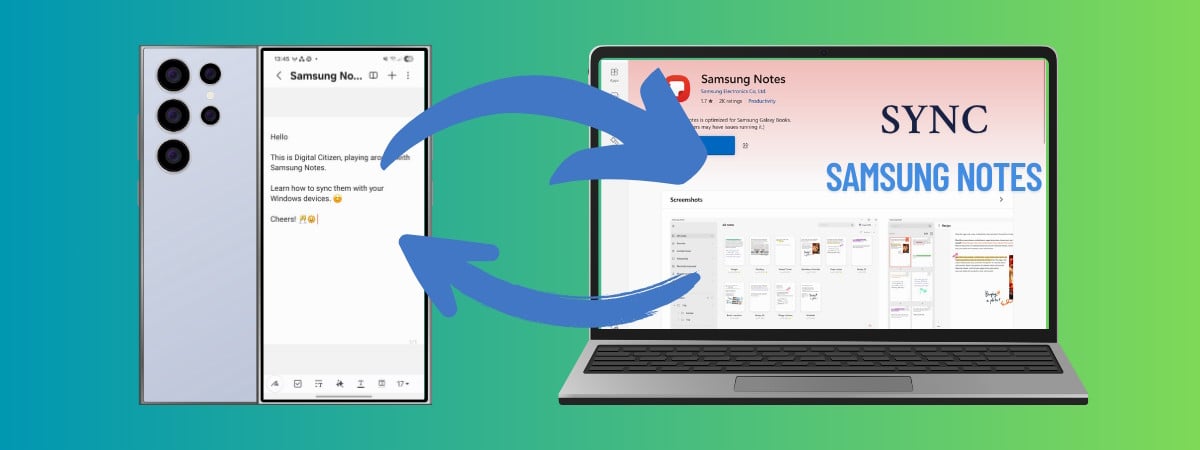
How to sync Samsung Notes with your Windows devices
Samsung Notes has quietly become one of the best apps for typed and handwritten notes, sketches, and quick to-do lists, especially if you’re using a Galaxy smartphone or tablet. Until recently, however, the answer to the question “Can I view Samsung Notes on my PC?” was usually no. Well, unless you had a Samsung Galaxy Book laptop. That’s finally changing,…
Read More » -
Blog
I test streaming devices for a living and I can’t wait to see a new Apple TV 4K — here’s why
It’s been three long years since Apple launched a new set-top box. Although ripe with features and tons of value — in spite of its hefty $129 starting price — the Apple TV 4K still proves that it’s one of the best streaming devices. There’s still room for improvement, however, especially now that Apple has better processors on the latest…
Read More » -
Blog

New PumaBot botnet brute forces SSH credentials to breach devices
A newly discovered Go-based Linux botnet malware named PumaBot is brute-forcing SSH credentials on embedded IoT devices to deploy malicious payloads. The targeted nature of PumaBot is also evident by the fact it targets specific IPs based on lists pulled from a command-and-control (C2) server instead of broader scanning of the internet. Targeting surveillance cams Darktrace documented PumaBot in a report…
Read More » -
Blog

The edge devices security risk: What leaders can do
In today’s complex IT environment, an abundance of legacy infrastructure combined with a lack of visibility and patching make network edge devices a major security risk. It’s therefore no surprise that compromised network edge devices have rapidly emerged as one of the biggest attack points for small and medium sized businesses. That’s according to statistics from Sophos’ Annual Threat Report,…
Read More » -
Blog

The oldest Fire TV devices are losing Netflix support soon
It’s finally time to upgrade for many owners of the earliest Amazon Fire TV devices, as Netflix is ending support for them next month, reports German outlet Heise. The cutoff for US users is June 3rd, according to ZDNet, which writes that the company has been emailing those who would be affected by the change. Netflix is specifically ending support…
Read More »

