Docker
-
Blog
10 Docker Containers Every Homelabber Should Run
There are thousands of Docker containers that you could potentially run on your server. While I haven’t run anywhere near all of them, here are 10 containers that I simply can’t live without in my homelab, and why I think you should run them too. Related Docker for Beginners: Everything You Need to Know Learn to use this incredibly popular…
Read More » -
Blog

Docker vs. Virtual Machines What’s Best for Your Homelab?
Summary Docker containers are lightweight, self-contained packages capable of efficiently running various services. Virtual machines are more robust, emulate full computers, and require more resources, but are more versatile in some aspects. Docker is excellent for deploying multiple services easily; virtual machines are best for specific, more robust deployments. When it comes to your homelab, there are two main technologies…
Read More » -
Blog

Docker Desktop blocked on Macs due to false malware alert
Docker is warning that Docker Desktop is not starting on macOS due to malware warnings after some files were signed with an incorrect code-signing certificate. The first reports of the malware alerts surfaced on January 7, 2025, when macOS users received an unexpected ‘Malware Blocked’ message preventing them from opening the Docker containers management app. “Malware Blocked. “com.docker.vmnetd” was not…
Read More » -
Blog

Exploitation of Docker remote API servers has reached a “critical level”
Hackers are exploiting unprotected Docker remote API servers to deploy malware, with researchers stating the threat has reached a “critical level” and warning organizations to act now. A report from Trend Micro published on 21 October details how researchers observed an unknown threat actor abusing exposed docker remote API servers to deploy the ‘perfctl’ malware. The attack sequence begins with…
Read More » -
Blog
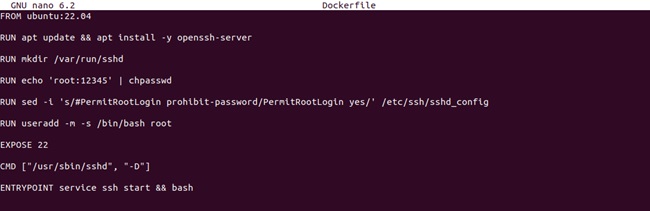
How to SSH Into Docker Container
Administrators commonly use SSH to access and operate remote servers and devices, including a Docker container. When you connect to any device using SSH, you can run commands, access its files, and perform multiple other tasks. You can also use the Docker container as a hypervisor image that can run applications. For example, a software developer can create a Docker…
Read More »

