EC2
-
Blog

whoAMI attacks give hackers code execution on Amazon EC2 instances
Security researchers discovered a name confusion attack that allows access to an Amazon Web Services account to anyone that publishes an Amazon Machine Image (AMI) with a specific name. Dubbed “whoAMI,” the attack was crafted by DataDog researchers in August 2024, who demonstrated that it’s possible for attackers to gain code execution within AWS accounts by exploiting how software projects retrieve…
Read More » -
Blog
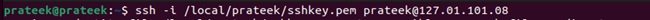
How to SSH Into EC2 Instance
EC2 is a service provided by Amazon Web Services (AWS) that lets you rent virtual servers (known as instances). In these instances, you can leverage virtual machines to develop, test, deploy, and manage computer applications. SSH is an incredible utility for accessing and managing Amazon Elastic Compute Cloud (EC2) instances. With SSH, you can operate a remote device, access data, execute…
Read More »

