Environment
-
Blog

Elgato’s Wave Link 2.0 promises clear vocals in any environment
Elgato is releasing a new version of its audio stream control software Wave Link that includes new AI-powered voice enhancements for your mic. It also has a new OS-level management system to redirect audio streams to certain apps, split audio to yourself and your audience, add audio effects, and quickly mute channels. The latest version 2.0 update is available to…
Read More » -
Blog

Server Hardening Checklist: Fortify your server environment
Server hardening involves ensuring the security of a server by reducing its vulnerabilities and attack surface A well-executed hardening process protects sensitive data, maintains operational integrity, and ensures compliance with regulatory standards. This comprehensive server hardening checklist will guide you through the necessary steps to fortify your server environment. Server Hardening Checklist 1. Operating System Hardening Operating system hardening is…
Read More » -
Blog

Cisco confirms attackers stole data, shuts down access to compromised DevHub environment
Cisco has closed public access to one of its third-party developer environments after threat actors successfully stole data from a public-facing DevHub environment. On 14 October, the prominent threat actor IntelBroker posted on BreachForums that they compromised data including source code, hard-coded credentials, certificates, API tokens, private and public keys, AWS private buckets, Docker builds, and Azure storage buckets as…
Read More » -
Blog

Managing security in a diverse cloud environment
There are clear benefits to having a diverse cloud environment in business. Whether it’s to meet the scalability requirements of a growing organization, to take advantage of the much lower costs of a proper multi-cloud approach, or to keep data secure through a hybrid cloud solution, there’s every reason for leaders to double down on the cloud However, embracing and…
Read More » -
Blog
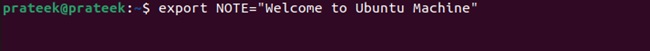
How to Set and Use Environment Variables In Bash Script
In bash scripting, environment variables are used to save and manage the data to modify the processes in the system. Using the bash scripts, you can use the environment variables to configure the system process. Environment variables also offer security and transmit the information from one script to another. Hence, there are multiple uses of environment variables that you can…
Read More »

