Kernel
-
Blog

CISA orders agencies to patch Linux kernel bug exploited in attacks
CISA has ordered federal agencies to secure their systems within three weeks against a high-severity Linux kernel flaw actively exploited in attacks. Tracked as CVE-2024-53104, the security bug was first introduced in kernel version 2.6.26 and was patched by Google for Android users on Monday. “There are indications that CVE-2024-53104 may be under limited, targeted exploitation,” the Android February 2025…
Read More » -
Blog

Google fixes Android kernel zero-day exploited in attacks
The February 2025 Android security updates patch 48 vulnerabilities, including a zero-day kernel vulnerability that has been exploited in the wild. This high-severity zero-day (tracked as CVE-2024-53104) is a privilege escalation security flaw in the Android Kernel’s USB Video Class driver that allows authenticated local threat actors to elevate privileges in low-complexity attacks. The issue occurs because the driver does…
Read More » -
Blog

Google just fixed a zero-day kernel flaw used by hackers and 47 other vulnerabilities — update your Android phone right now
Keeping your phone up to date and running the latest security patches is the easiest way to stay safe from hackers which is why if you own one of the best Android phones, you’re going to want to install the February 2025 Android security updates right away. As reported by BleepingComptuer, Google has released this month’s Android security updates which…
Read More » -
Blog

macOS bug lets hackers install malicious kernel drivers
Apple recently addressed a macOS vulnerability that allows attackers to bypass System Integrity Protection (SIP) and install malicious kernel drivers by loading third-party kernel extensions. System Integrity Protection (SIP), or ‘rootless,’ is a macOS security feature that prevents malicious software from altering specific folders and files by limiting the root user account’s powers in protected areas. SIP allows only Apple-signed…
Read More » -
Blog

New Windows Driver Signature bypass allows kernel rootkit installs
Attackers can downgrade Windows kernel components to bypass security features such as Driver Signature Enforcement and deploy rootkits on fully patched systems. This is possible by taking control of the Windows Update process to introduce outdated, vulnerable software components on an up-to-date machine without the operating system changing the fully patched status. Downgrading Windows SafeBreach security researcher Alon Leviev reported…
Read More » -
Blog

How to Compile the VMware Workstation Pro Kernel Modules on Ubuntu/Debian
Once the VMware Workstation Pro desktop virtualization software (Type-II hypervisor) is installed on your Ubuntu/Debian system, you must compile the VMware Workstation Pro kernel modules for your Ubuntu/Debian system for it to work. In this article, I will show you how to compile the VMware Workstation Pro kernel modules on Ubuntu/Debian. I will also discuss the problems you may face…
Read More » -
Blog
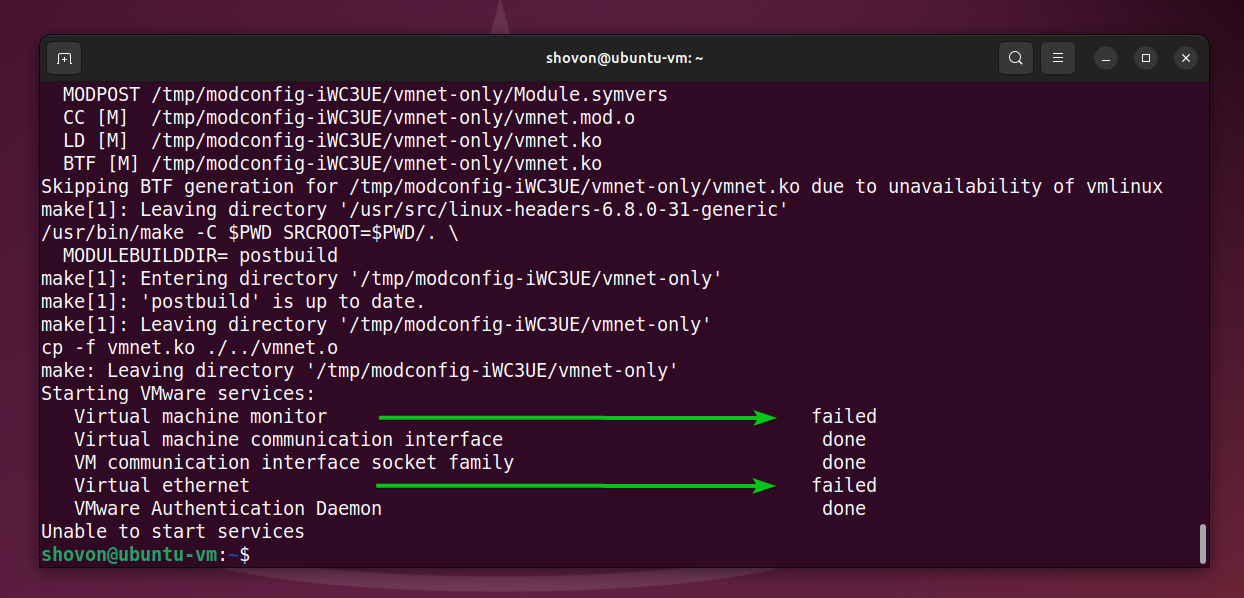
How to Sign VMware Workstation Pro Kernel Modules on UEFI Secure Boot Enabled Linux Systems
For VMware Workstation Pro kernel modules to load on UEFI Secure Boot enabled Linux systems, you must sign them manually. Unsigned VMware Workstation Pro kernel modules won’t load, resulting in VMware Workstation Pro services failing to start. As you can see, VMware Workstation Pro services failed to start after the VMware Workstation Pro kernel modules were compiled successfully. The…
Read More »

