malicious
-
Blog

PyPI adds project archiving system to stop malicious updates
The Python Package Index (PyPI) has announced the introduction of ‘Project Archival,’ a new system that allows publishers to archive their projects, indicating to the users that no updates are to be expected. The projects will still be hosted on PyPI, and users will still be able to download them but they will see a warning about the maintenance status, to…
Read More » -
Blog

Malicious GitHub repositories target users with malware
McAfee has uncovered new malware that’s being used to target GitHub users with infostealing malware. The security firm said it found several GitHub repositories offering video game hacks, cracked software, and free crypto tools that were not what they seemed. They included game hacks for top-selling video games such as Apex Legends, Minecraft, Counter Strike 2.0, Roblox, Valorant, Fortnite, Call…
Read More » -
Blog
Hackers are using a new AI chatbot to wage attacks: GhostGPT lets users write malicious code, create malware, and curate phishing emails – and it costs just $50 to use
Hackers are using an uncensored chatbot dubbed GhostGPT to help write malware, highlighting how AI can be twisted to “illegal activities”. That’s according to Abnormal Security, which laid out details of GhostGPT in a blog post, saying the chatbot lacks the guardrails of standard AI tools such as ChatGPT, making it a helpful tool for cyber criminals. It’s not the…
Read More » -
Blog

Telegram captcha tricks you into running malicious PowerShell scripts
Threat actors on X are exploiting the news around Ross Ulbricht to direct unsuspecting users to a Telegram channel that tricks them into run PowerShell code that infects them with malware. The attack, spotted by vx-underground, is a new variant of the “Click-Fix” tactic that has become very popular among threat actors to distribute malware over the past year. However,…
Read More » -
Blog

Malicious PyPi package steals Discord auth tokens from devs
A malicious package named ‘pycord-self’ on the Python package index (PyPI) targets Discord developers to steal authentication tokens and plant a backdoor for remote control over the system. The package mimics the highly popular ‘discord.py-self,’ which has nearly 28 million downloads, and even offers the functionality of the legitimate project. The official package is a Python library that allows communication with Discord’s…
Read More » -
Blog

macOS bug lets hackers install malicious kernel drivers
Apple recently addressed a macOS vulnerability that allows attackers to bypass System Integrity Protection (SIP) and install malicious kernel drivers by loading third-party kernel extensions. System Integrity Protection (SIP), or ‘rootless,’ is a macOS security feature that prevents malicious software from altering specific folders and files by limiting the root user account’s powers in protected areas. SIP allows only Apple-signed…
Read More » -
Blog
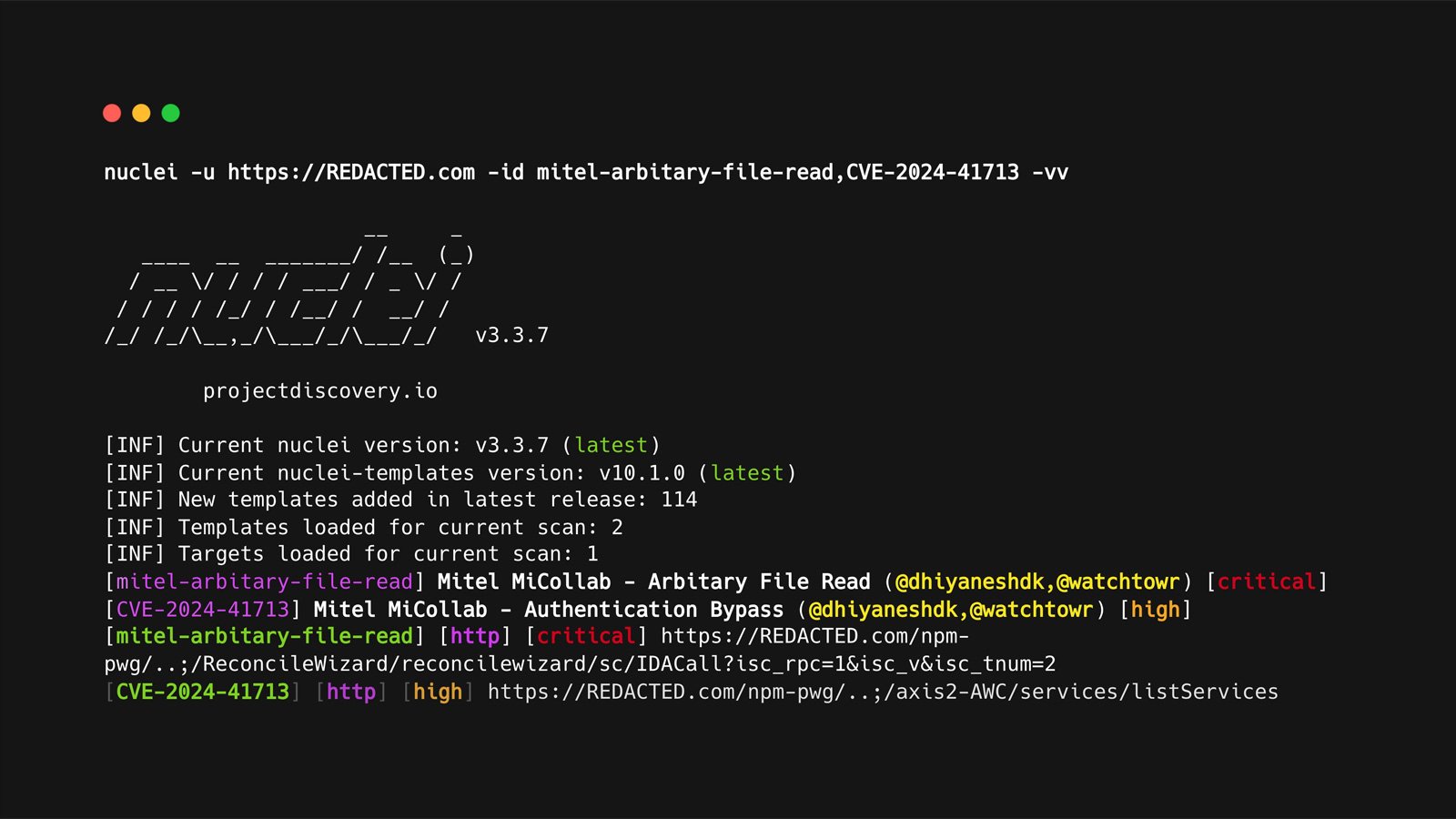
Nuclei flaw lets malicious templates bypass signature verification
A now-fixed vulnerability in the open-source vulnerability scanner Nuclei could potentially allow attackers to bypass signature verification while sneaking malicious code into templates that execute on local systems. Nuclei is a popular open-source vulnerability scanner created by ProjectDiscovery that scans websites for vulnerabilities and other weaknesses. The project utilizes a template-based scanning system of over 10,000 YAML templates that scan websites…
Read More » -
Blog

Malicious npm packages target Ethereum developers’ private keys
Twenty malicious packages impersonating the Hardhat development environment used by Ethereum developers are targeting private keys and other sensitive data. Collectively, the malicious packages have recorded more than one thousand downloads, researchers say. Narrow targeting campaign Hardhat is a widely used Ethereum development environment maintained by the Nomic Foundation. It is used for developing, testing, and deploying smart contracts and decentralized…
Read More » -
Blog

Malicious Rspack, Vant packages published using stolen NPM tokens
Three popular npm packages, @rspack/core, @rspack/cli, and Vant, were compromised through stolen npm account tokens, allowing threat actors to publish malicious versions that installed cryptominers. The supply chain attack, spotted by both Sonatype and Socket researchers, deployed the XMRig cryptocurrency miner on compromised systems for mining the hard-to-trace Monero privacy cryptocurrency. Additionally, Sonatype discovered that all three npm packages fell…
Read More » -
Blog

Malicious ads push Lumma infostealer via fake CAPTCHA pages
A large-scale malvertising campaign distributed the Lumma Stealer info-stealing malware through fake CAPTCHA verification pages that prompt users to run PowerShell commands to verify they are not a bot. The campaign leveraged the Monetag ad network to propagate over one million ad impressions daily across three thousand websites. The malicious operation, dubbed “DeceptionAds” by Guardio Labs and Infoblox researchers, is believed…
Read More »

