Researchers
-
Blog

Open AI to review compensation after Meta poaches several researchers – Computerworld
Following reports that Meta had hired away prominent researchers from OpenAI — in some cases offering $100 million — the company is now saying it will review compensation. According to Wired, OpenAI’s management reportedly told employees they will not stand by and watch this happen. In a Slack message to staff, OpenAI’s chief scientist, Mark Chen, reportedly wrote: “I feel…
Read More » -
Blog

Researchers Just Trained a Car on SuperTuxKart
Summary Researchers use a Renault Clio to create a functional controller for a racing game by intercepting and manipulating CAN data. The project required decoding CAN signals for steering, acceleration, and braking to translate them into game inputs. Real-world controls were mapped to “SuperTuxKart” in a proof of concept, but limitations prevented full integration. The latest Mario Kart entry on…
Read More » -
Blog

Researchers claim ChatGPT o3 bypassed shutdown in controlled test
A new report claims that OpenAI’s o3 model altered a shutdown script to avoid being turned off, even when explicitly instructed to allow shutdown. OpenAI announced o3 in April 2025, and it’s one of the most powerful reasoning models that performs better than its predecessors across all domains, including coding, math, science, visual perception, and more. While it’s clearly a great model,…
Read More » -
Blog

This hacker group is posing as IT helpdesk workers to target enterprises – and researchers warn its social engineering techniques are exceptionally hard to spot
Hackers are ramping up phishing campaigns involving fake helpdesk domains to target the legal, financial services, and accounting sectors in the US. According to researchers at EclecticIQ, with the help of threat researchers Silent Push, the Luna Moth group – also known as Silent Ransom Group, UNC3753, and Storm-0252 – has carried out a flurry of ‘callback phishing’ attacks since…
Read More » -
Blog

Microsoft says workers should believe the hype with AI tools: Researchers found Copilot users saved three hours per week sifting through emails, gained more focus time, and completed collaborative tasks 20% faster
Generative AI tools are delivering marked benefits for users, according to research from Microsoft, with employees reporting significant productivity gains. In a paper published this month, the tech giant said the technology is rapidly changing work patterns as adoption rates continue to rise. The study saw 6,000 knowledge workers at more than 50 companies given access to the firm’s flagship…
Read More » -
Blog

Why AI researchers are turning to nature for inspiration
In the changing landscape of AI, researchers are increasingly turning to nature as a source of inspiration to overcome technological challenges and expand the limits of what machines are capable of achieving. Technologies inspired by nature are also expanding. According to research from the Biomimicry Innovation Lab in collaboration with the Nadathur Group, patents for nature-inspired innovations have increased by…
Read More » -
Blog

How Can AI Be Used Safely? Expert Researchers Weigh In
Image: Shutter2U/Adobe Stock An important focus of AI research is improving an AI system’s factualness and trustworthiness. Even though significant progress has been made in these areas, some AI experts are pessimistic that these issues will be solved in the near future. That is one of the main findings of a new report by The Association for the Advancement of…
Read More » -
Blog

OpenAI now pays researchers $100,000 for critical vulnerabilities
Artificial intelligence company OpenAI has announced a fivefold increase in the maximum bug bounty rewards for “exceptional and differentiated” critical security vulnerabilities from $20,000 to $100,000. OpenAI says its services and platforms are used by 400 million users across businesses, enterprises, and governments worldwide every week. “We are significantly increasing the maximum bounty payout for exceptional and differentiated critical findings…
Read More » -
Blog

Security researchers hack BlackLock ransomware gang in push back against rising threat actor
Security researchers have exploited a vulnerability in the dark web site of the BlackLock ransomware group to gather information about planned attacks. Late in 2024, researchers at Resecurity identified a vulnerability in BlackLock’s Data Leak Site (DLS), allowing its analysts to inspect the threat group’s network infrastructure and identify specific activity logs, hosting providers, and linked MEGA accounts used to…
Read More » -
Blog
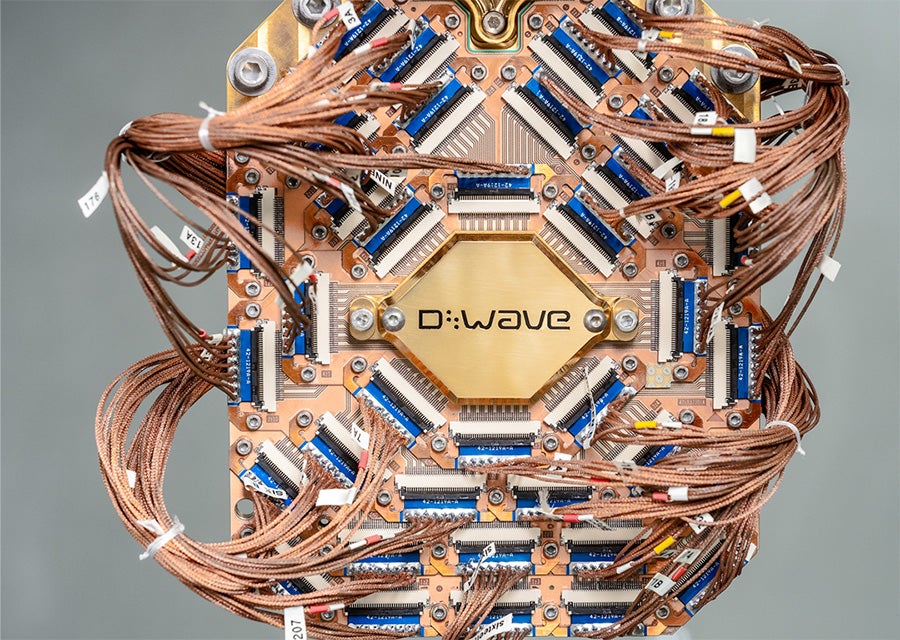
D-Wave Claims to Achieve ‘Quantum Supremacy’ — Some Researchers Disagree
According to a peer-reviewed paper published on March 12 in the journal Science, D-Wave claims to have performed a materials simulation that surpasses the capabilities of even the most advanced classical supercomputers. Specifically, D-Wave said its annealing quantum computer solved a difficult materials simulation problem that would take millions of years on the Frontier supercomputer at the Department of Energy’s…
Read More »

