Service
-
Blog

Sick of cable? This is the one live TV streaming service I’d use to cut the cord
I cut the cord years ago. But this year, I finally tested all of the best live TV streaming services for Tom’s Guide, so I could definitively say which one was the best, and possibly even ditch my current service: YouTube TV. I’ve been a loyal YouTube TV customer for close to five years now. It’s been far superior to…
Read More » -
Blog

Klarna CEO Sebastian Siemiatkowski might be calming his tone on AI replacement – but the future of customer service could be a two-tier nightmare
We can all let out a big sigh of relief at the prospect of AI replacing our jobs, for Klarna CEO Sebastian Siemiatkowski is backtracking on his dreams of a fully automated workforce. Siemiatkowski has made no secret of its automation efforts over the last year or so. In September, he sparked the ire of Salesforce CEO Marc Benioff after…
Read More » -
Blog

AVCheck cyber crime service snared in police takedown
An international law enforcement operation has disrupted an online software crypting syndicate which helps cyber criminals protect their malware from detection. Four domains and their associated server offering counter-antivirus (CAV) tools have been seized by the FBI Houston Field Office, working with law enforcement partners in the Netherlands and Finland and the US Secret Service. When used with crypting services…
Read More » -
Blog

OmniRide bus service notifies victims of data breach claimed by ransomware gang
OmniRide this week confirmed it notified victims of a December 2024 data breach that compromised their personal information. Potomac & Rappahannock Transportation Commission, which provides the OmniRide public bus service in the Washington, D.C. suburban area, has not disclosed what data or how many people were compromised yet. Ransomware gang Fog took credit for the breach in January 2025, saying…
Read More » -
Blog

Agentic AI is coming for customer service jobs
Agentic AI is set to be handling more than two-thirds of customer service and support interactions by 2028, with almost all business and technical decision-makers thinking it will do a better job than human beings. In a survey conducted by Cisco, 93% of global respondents said they believed that agentic AI will enable B2B technology vendors to deliver more personalized,…
Read More » -
Blog

MATLAB dev confirms ransomware attack behind service outage
MathWorks, a leading developer of mathematical computing and simulation software, has revealed that a recent ransomware attack is behind an ongoing service outage. Headquartered in Natick, Massachusetts, and founded in 1984, MathWorks now has over 6,500 employees in 34 offices worldwide. MathWorks develops the MATLAB numeric computing platform and the Simulink simulation, which are used by over 100,000 organizations and…
Read More » -
Blog

SoundCloud Just Updated Their Terms of Service After AI Policy Backlash
You might be having a bad week, but AI is having a worse one. First there was the “racism glitch” that beset Grok, and now music platform SoundCloud is facing some serious criticism for a clause buried in its terms of service. The imbroglio began in February 2024, when SoundCloud quietly changed its TOS to include: In the absence of…
Read More » -
Blog
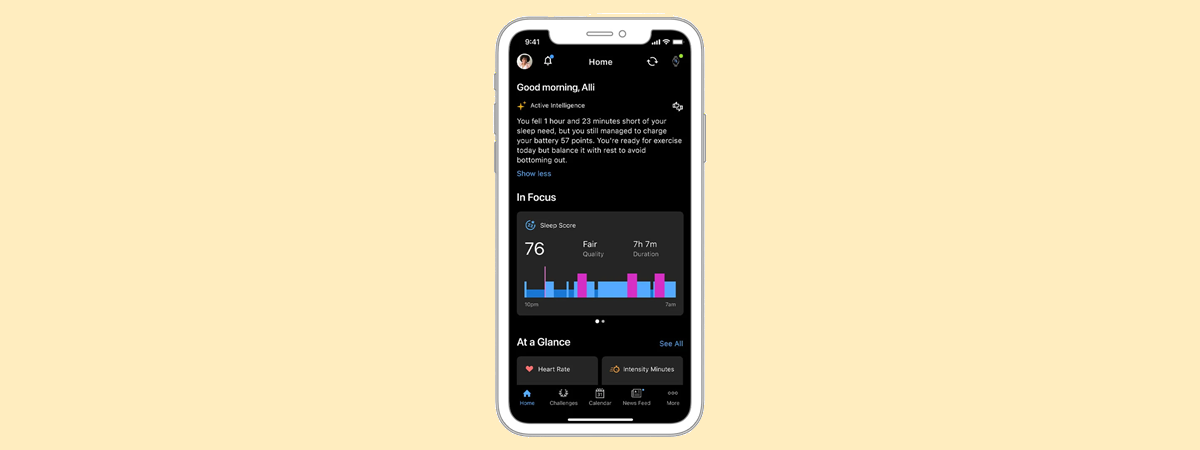
An excellent service or an optional expense?
While I was testing the Garmin vivoactive 6 – a smartwatch that impressed me despite minimal hardware upgrades – the company launched its first-ever premium subscription service, Garmin Connect+. Priced at $6.99 per month, which is less than Apple Fitness+, this new offer sparked considerable debate among Garmin’s users who worry about useful features moving behind a paywall. As always,…
Read More » -
Blog

The Tech Feud That Could Shape the Next Frontier of Mobile Service
Image: John Gress Media Inc, Shutterstock / John Gress Media Inc Apple is seeking to eliminate cell phone dead spots though expanded satellites, but Elon Musk’s Starlink won’t let that happen without a fight, according to an exclusive report from The Wall Street Journal. Sources who spoke to WSJ say SpaceX is now putting pressure on U.S. federal regulators to…
Read More » -
Blog

Is the IT service desk dying out?
When something goes wrong with IT at work, chances are you’ll be asked to submit a service ticket. This is a tale as old as time – see a problem, submit a ticket, wait for the service desk to come to your help. But all this could be set for change. Advances in technology have opened the door to software…
Read More »

