SSH
-
Blog

New PumaBot botnet brute forces SSH credentials to breach devices
A newly discovered Go-based Linux botnet malware named PumaBot is brute-forcing SSH credentials on embedded IoT devices to deploy malicious payloads. The targeted nature of PumaBot is also evident by the fact it targets specific IPs based on lists pulled from a command-and-control (C2) server instead of broader scanning of the internet. Targeting surveillance cams Darktrace documented PumaBot in a report…
Read More » -
Blog

Critical Erlang/OTP SSH RCE bug now has public exploits, patch now
Public exploits are now available for a critical Erlang/OTP SSH vulnerability tracked as CVE-2025-32433, allowing unauthenticated attackers to remotely execute code on impacted devices. Researchers at the Ruhr University Bochum in Germany disclosed the flaw on Wednesday, warning that all devices running the daemon were vulnerable. “The issue is caused by a flaw in the SSH protocol message handling which allows an…
Read More » -
Blog

Critical Erlang/OTP SSH pre-auth RCE is ‘Surprisingly Easy’ to exploit, patch now
A critical vulnerability in the Erlang/OTP SSH, tracked as CVE-2025-32433, has been disclosed that allows for unauthenticated remote code execution on vulnerable devices. The flaw was discovered by Fabian Bäumer, Marcus Brinkmann, Marcel Maehren, and Jörg Schwenk of the Ruhr University Bochum in Germany and given a maximum severity score of 10.0. All devices running the Erlang/OTP SSH daemon are impacted by the…
Read More » -
Blog

Windows 10 KB5053606 update fixes broken SSH connections
Microsoft has released the KB5053606 cumulative update for Windows 10 22H2 and Windows 10 21H2, which fixes numerous bugs, including one preventing SSH connections. The Windows 10 KB5053606 update is mandatory as it contains Microsoft’s March 2025 Patch Tuesday security updates, which fix six actively exploited zero-day vulnerabilities. Windows users can install this update by going into Settings, clicking on Windows Update, and…
Read More » -
Blog

Chinese cyberspies use new SSH backdoor in network device hacks
A Chinese hacking group is hijacking the SSH daemon on network appliances by injecting malware into the process for persistent access and covert operations. The newly identified attack suite has been used in attacks since mid-November 2024, attributed to the Chinese Evasive Panda, aka DaggerFly, cyber-espionage group. As per the findings of Fortinet’s Fortiguard researchers, the attack suite is named “ELF/Sshdinjector.A!tr” and…
Read More » -
Blog

Ransomware gang uses SSH tunnels for stealthy VMware ESXi access
Ransomware actors targeting ESXi bare metal hypervisors are leveraging SSH tunneling to persist on the system while remaining undetected. VMware ESXi appliances have a critical role in virtualized environments as they can run on a single physical server multiple virtual machines of an organization. They are largely unmonitored and have been a target for hackers looking to access corporate networks…
Read More » -
Blog

How to Run a Command That Requires sudo via SSH
Secure Shell includes a lot of tricks, many of which can make your admin’s life exponentially easier. One such trick is the ability to run commands on remote servers, without logging in. Sure, you can take the time to log into the server, run the command, and log out, but why not just do it all in one fell swoop?…
Read More » -
Blog
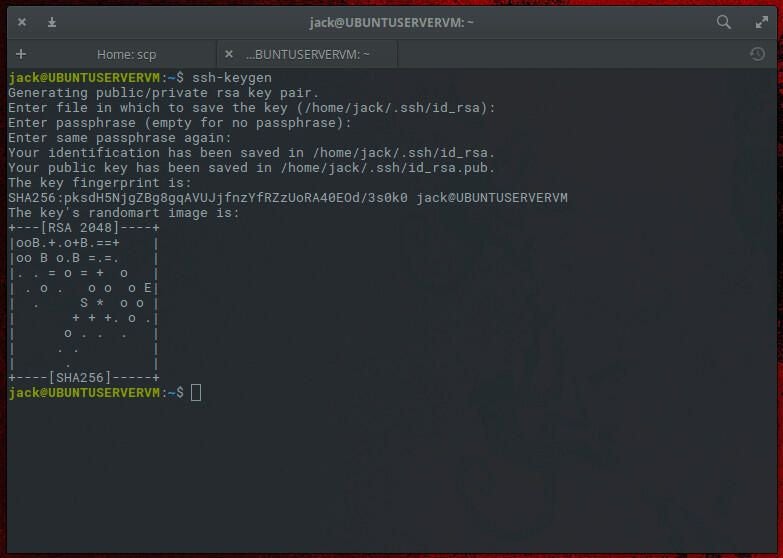
How To Use SCP (Secure Copy) With SSH Key Authentication
Anyone who administers Linux machines likely knows secure shell. Without this tool, administering those servers remotely would be quite challenging. It would also become harder to move files back and forth, at least with a modicum of security. That’s where secure copy comes into play. With the SCP command, you can copy files to and from a remote Linux server…
Read More » -
Blog

How to Add an SSH Fingerprint to Your known_hosts File in Linux
Let’s say you’ve written a bash script that scans all of your Linux servers in your data center for uptime. Such a file could contain the following contents: ssh $1 "uptime" When you run your script, it may get foiled by an issue where it is stopped by a server that has yet to have its SSH key fingerprint added…
Read More » -
Blog

Microsoft says recent Windows 11 updates break SSH connections
Microsoft has confirmed that last month’s Windows security updates are breaking SSH connections on some Windows 11 22H2 and 23H2 systems. This newly acknowledged issue affects enterprise, IOT, and education customers, but the company says that only a “limited number” of devices are impacted. Microsoft is also investigating whether consumer customers using Windows 11 Home or Pro editions are affected.…
Read More »

