Top
-
Blog
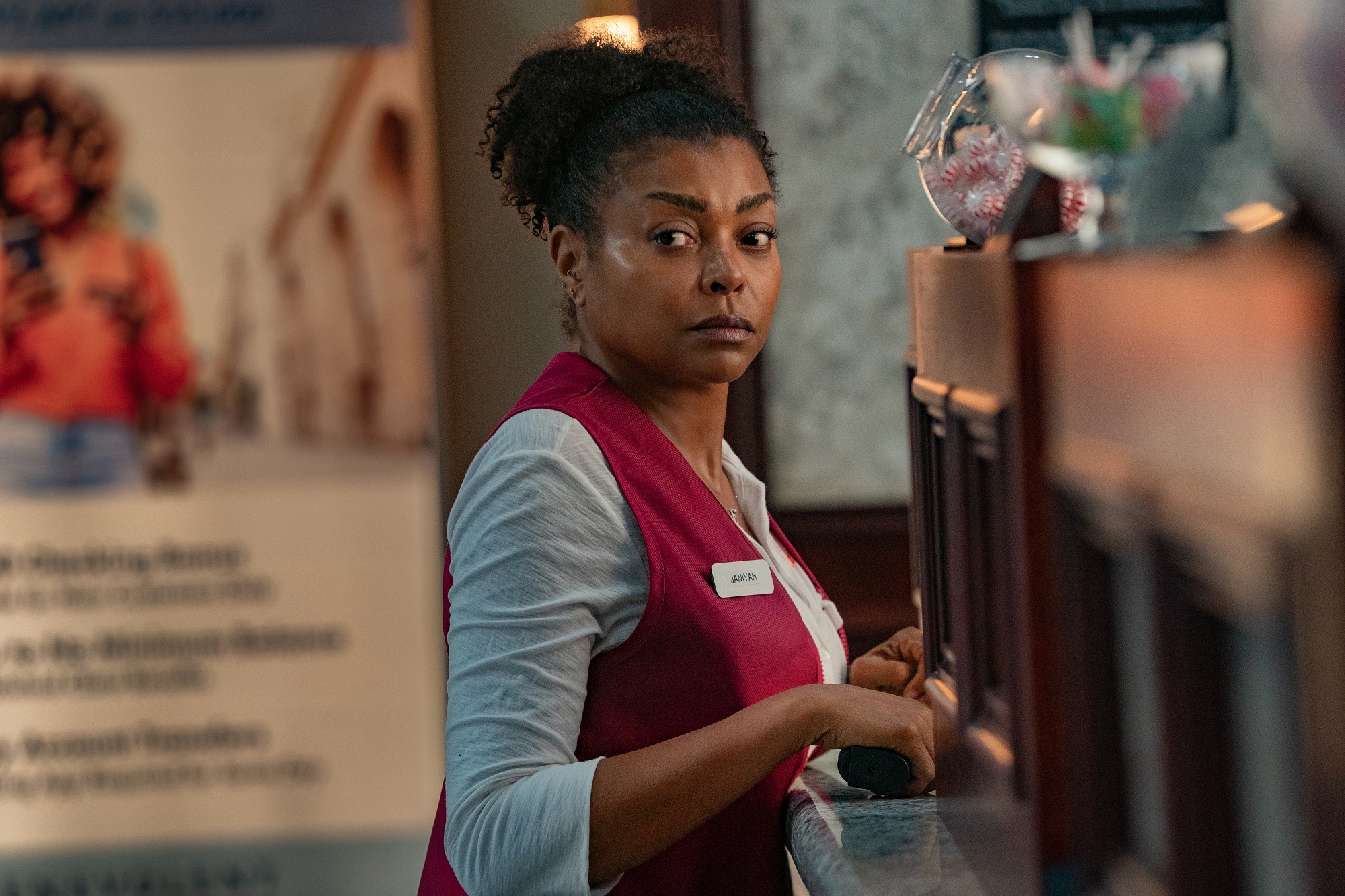
Netflix top 10 movies — here’s the 3 worth watching right now
Another weekend is here, which means the question of what to watch is fresh on our minds. The Netflix top 10 list of most-watched movies is as good a tool as any for cutting through the noise quickly, but figuring out which ones are actually worth the hype is a tall order. That’s why we track the Netflix top 10…
Read More » -
Blog

Just in time for winter, De’Longhi’s serving up hot EOFY deals on its top coffee machines — save up to AU$559.90!
If you’re in the market for a new coffee machine this Australian EOFY, there’s some tasty discounts on De’Longhi’s excellent range of fully automatic coffee machines up for grabs. Beyond the long-term cost-effectiveness of having a machine at home, the De’Longhi EOFY sale lets you save up to 30% on its most popular models, and you can even shave an…
Read More » -
Blog

Bose Father’s Day sale is live — my top picks from $149
When it comes to headphones and earbuds, Bose makes some of the best headphones we’ve tested. With Father’s Day less than two weeks out, Bose is offering some killer deals on our favorite gear. For instance, right now you can get the Bose QuietComfort Earbuds for just $149. That’s $30 off an excellent pair of earbuds. Alternatively, you can get…
Read More » -
Blog

Top Antivirus With Best Customer Support in 2025
When it comes to choosing an antivirus with the best customer support, security remains the top priority. However, many antivirus solutions offer robust protection, so other factors like performance, advanced features, and customer support become crucial differentiators. Customer support is vital for those new to antivirus software or seeking hassle-free setup and security. While most paid antivirus solutions offer some…
Read More » -
Blog

Netflix top 10 movies — here’s the 3 worth watching right now
Summer is just around the corner, and already Netflix is heating up with tons of great new movies. But a few titles definitely rise above the rest, and the streamer’s top 10 list is a great tool for cutting through the noise when you’re figuring out what to watch. Granted, some duds are inevitably going to crop up among the…
Read More » -
Blog

I’m a sleep tech writer — my 5 top picks from the final Memorial Day sales
As a sleep tech writer, I’ve tried my fair share of sleep gadgets over the last nine months — from sleep headbands to the best sunrise alarm clocks and sleep trackers, each of which can elevate your nighttime routine in its own way. One of this year’s best mattresses for your sleep style and body type should be your first…
Read More » -
Blog
CR’s 3 Top Picks for High Chairs
Starting around 6 months or so, your baby’s high chair will become a regular go-to for snack and meal times. Depending on the model, it can even be used through their toddler years. This means that whichever high chair you choose, it will most likely get a lot of (heavy, messy) use during your child’s first years. When choosing the…
Read More » -
Blog
CR’s 3 Top Picks for Strollers
Consumer Reports tested over 100 strollers and double strollers, from Bugaboo to UPPAbaby, to find the best ones. We test strollers for ease of use (going through each and every feature a parent will have to use) maneuverability (pushing each stroller over our CR-designed indoor maneuverability course, which includes smooth and rough terrain, hills, curbs, and a series of cones),…
Read More » -
Blog
Top Picks for Double Strollers in 2025
“There are good strollers at many prices,” says Joan Muratore, who oversees testing of products for Babies and Healthy Living at Consumer Reports. “If you don’t want to spend $1,000, there’s no need to. If you care about having the chicest or most popular model on TikTok or Instagram, you do you! But if you just want a good, safe stroller…
Read More » -
Blog
CR’s 3 Top Picks for Travel Systems
Consumer Reports tested 17 travel systems, from Bob Gear to UppaBaby, assessing the strollers for ease of use, safety, and maneuverability, and the car seats for crash protection, ease of use, and vehicle fit. The three travel systems that impress our testers the most are our Top Picks for Travel Systems for 2025. CR’s Top Pick for Travel Systems, below,…
Read More »





