Vendor Spotlight: CoSoSys

Have you heard of a company called CoSoSys? Do you know what the name stands for? You’ll be amazed to discover that it doesn’t mean anything. The company just made up something that sounds IT-ish – that’s why the “Sys” has to be in there.
CoSoSys is the producer of the very successful Endpoint Protector system. The tool is a data loss prevention (DLP) package and it covers all other operating systems that you are likely to have in your office: Windows, macOS, and Linux. The tool has recently been taken over, but we are going to look at the business’s history.
We are going to identify who started CoSoSys, how they built the business up and what conglomerate bought the company. We will also look at the likely future of the brand and who its competitors are.
Founding and Background
CoSoSys was founded in 2004 by Roman Foeckl in Cluj-Napoca, Romania. He was advised by business consultant, Michael Bauner, who invested in the company and took a part-time management role. As he was based in Germany and ran other businesses there alongside his commitment to CoSoSys, Baumer was never as involved with CoSoSys and Foeckl.
The company started with the goal of creating software solutions that would help organizations secure and control sensitive data on portable storage devices such as USB drives. Over time, the focus expanded to cover broader data protection needs, leading to the development of its flagship product, Endpoint Protector.
2011 was a choppy year for CoSoSys. In January, Foeckl agreed to sell the company in its entirety to Astaro, a German IT cybersecurity company. Almost immediately, however, Astaro entered negotiations with Sophos, a British cybersecurity firm, which acquired Astaro in July 2011. CoSoSys wasn’t intended to play a part in the future of Sophos, however. Roman Foeckl, together with Senior VP, Michael Bauner implemented a management buyout of CoSoSys, splitting it off from Astaro at the point that it was absorbed into Sophos.
CoSoSys received a strategic investment from Turn/River Capital in 2020 to accelerate its growth. Michael Bauner cashed out and left the company in April 2020. Roman Foeckl transitioned from CEO to Chief Strategy Officer in August 2022 when Kevin Gallagher took the CEO role.
Netwrix, a cybersecurity vendor, acquired CoSoSys in February 2024. Roman Foeckl left the company once the takeover was completed in March 2024. This acquisition aimed to enhance Netwrix’s endpoint security offerings by integrating CoSoSys’ data loss prevention (DLP) solutions, particularly their flagship product, Endpoint Protector. The financial terms of the deal were not disclosed.
This move allows Netwrix to expand its capabilities in protecting sensitive data on workstations and laptops, addressing the growing challenges of data security in hybrid and remote work environments.
Timeline and Evolution
CoSoSys has a long and busy history. Here is a timeline of the major events at the business:
- 2004: CoSoSys was founded by Roman Foeckl in Cluj-Napoca, Romania, with an initial focus on securing data on portable devices like USB drives.
- 2005-2009: CoSoSys launched its first USB and device control software solutions, helping enterprises secure data on removable devices. The company expanded its focus to endpoint security, addressing broader data loss prevention (DLP) needs.
- 2010: Launch of Endpoint Protector.
- January 2011: Astaro acquires all shares in CoSoSys.
- July 2011: Sophos acquires Astaro.
- July 2011: Management buyout by Roman Foeckl and Michael Bauner restores CoSoSys’ independence.
- 2011-2014: The company increased market penetration, with Endpoint Protector becoming known for its flexibility and cross-platform compatibility.
- 2018: GDPR drives demand for CoSoSys’ DLP solutions. CoSoSys introduced more advanced data classification and content inspection features to help companies adhere to strict regulatory frameworks.
- March 2020: Turn/River Capital invests in CoSoSys to accelerate growth.
- 2021-2023: CoSoSys integrated AI-based features into Endpoint Protector, improving its ability to detect and prevent insider threats. The company developed data privacy regulations compliance.
- February 2024: Netwrix acquires CoSoSys, expanding its DLP offerings and global reach.
Today, under the leadership of Netwrix, CoSoSys is anticipated to further develop its DLP solutions, focusing on advanced threat detection, cloud security, and broader compliance features for global markets. Nettwrix’s acquisition will enable CoSoSys to leverage a larger platform and customer base, bringing its products to new regions and industries.
Company Ownership
CoSoSys has been a private business for its entire existence, as are all the companies that bought it over the years. The most consistent owner of the company was Roman Foeckl. He owned the business from its creation in 2004 until the beginning of 2011, then, by mid-2011, he bought back the business. He retained a stake in the business, while a large investment by Turn/River capital made them the majority owner. Furthermore, he finally sold up completely in 2024, alongside Turn/River Capital when they sold CoSoSys to Netwrix.
The company is now entirely owned by Netwrix, which is a private company. That business was founded by two entrepreneurs in 2006 and the company went through two funding rounds. These occurred in February 2017 and May 2023. The result of these investments is that the company is now entirely owned by three private equity firms. The largest shareholder is TA Associates; Updata Partners and Centerbridge Partners are the other two owners.
Key People
- Roman Foeckl, Founder and Chief Strategy Officer: Roman is the Founder and Chief Strategy Officer of CoSoSys. Before founding the company in 2004, Roman worked for Goldman Sachs in Frankfurt, Germany, and Paris, France. He remained CEO of the company for most of its history, even through the tumult of 2011 when Foeckl sold the company in January and then bought it back in July. He stood down as CEO and became Chief Technology Officer for CoSoSys in August 2022. His relationship with the company ended in March 2024, when he sold his shares in the company to Netwrix and stood down as CSO.
- Michael Bauner, Founder and Senior VP: Bauner runs his own management consultancy, and that business brings him in contact with a number of businesses in which he can invest as well as advise. He was a founding investor in CoSoSys and helped the business get set up. However, he has also run other businesses of his own as well as consulting with other clients for the entirety of his involvement with CoSoSys. He is still running his own companies and starting up new enterprises today. He sold his shares to TA Associates in April 2020 and his involvement with the company ended.
- Kevin Gallagher, Chief Executive Officer: Gallagher took over as the leader of CoSoSys in August 2020. Before moving to CoSoSys, Gallagher had been Chief Revenue Officer for Netsparker, Acunetix, and Invicti, three highly respected vulnerability management brands that have grown very quickly as application security testing tools providers. He saw CoSoSys through its adoption of AI processes and guided the company through the takeover by Netwrix. It seems that Netwrix decided that they wanted someone else in charge of CoSoSys because Gallagher left in April 2024.
- Steve Dickson, Chief Executive Officer, Netwrix: Dickson has been the CEO at Netwrix since April 2018. He seems to have decided to take that role at CoSoSys, which suggests that CoSoSys will be fully absorbed by Netwrix. However, the parent company operates from its offices in Frisco, Texas, while CoSoSys is still based in Cluj-Napoca, Romania. So, Dickson can only be a titular head or a remote CEO.
Locations
CoSoSys is a Romanian company, based in the town in which it was founded: Cluj-Napoca. There is a little confusion about the nationality of the company because, like many Indian tech enterprises, the company has taken steps to appear to be American – this works better when trying to sell products in the USA.
The company has its US HQ and a development center in Raleigh, North Carolina. CoSoSys also operates an office in Seoul, Korea. In Germany and India, the company is officially called Endpoint Protector. It has an office in Friedrichshafen in Germany. The company doesn’t have offices in India but operates a phone number there to give it a virtual presence.
CoSoSys Target Market and Customer Base
Target Market
CoSoSys focuses on providing Data Loss Prevention (DLP) solutions, targeting businesses and organizations across a variety of sectors. Its primary market includes:
- Small and medium-sized enterprises (SMEs): CoSoSys has tailored its solutions to meet the needs of mid-size organizations that require robust data security but may not have extensive IT resources. Endpoint Protector’s ease of use and affordable deployment options (on-premises, cloud-based, or virtual appliances) make it attractive to SMEs seeking scalable DLP solutions.
- Large enterprises: While CoSoSys started with a focus on smaller businesses, its cross-platform capabilities and advanced compliance features have attracted large enterprises across multiple industries. The ability to deploy Endpoint Protector in complex environments—spanning Windows, macOS, Linux, and mobile devices—makes it ideal for organizations with global operations and multi-layered IT ecosystems.
- Highly Regulated Industries: CoSoSys serves industries that are heavily regulated and require stringent data protection and compliance solutions. These industries include:
- Healthcare: Meeting regulatory requirements like HIPAA by preventing data breaches and protecting patient records.
- Finance and banking: Compliance with GDPR, PCI-DSS, and other financial regulations, ensuring sensitive financial data is secured.
- Education: Protecting student information and complying with regulations such as FERPA in academic institutions.
- Legal services: Law firms managing sensitive client data and legal documentation need to ensure that confidential information is not leaked or accessed improperly.
- Geographically Diverse Organizations: CoSoSys’ multi-language support and ability to operate seamlessly across different regions make it attractive to companies with international operations that need to comply with regional data protection regulations such as GDPR, CCPA, and others.
Customer Base
CoSoSys serves a wide range of customers across different sectors and geographies. Its customer base includes:
- Small to medium-sized businesses (SMBs)
- Global enterprises
- Healthcare providers
- Financial institutions
- Educational institutions
- Legal firms and services
Geographical Reach
- Europe: As a European company, CoSoSys has a strong presence in the European market, particularly in countries subject to GDPR and other EU data protection laws.
- North America: With the investment from Turn/River Capital and subsequent growth in the US market, CoSoSys has significantly expanded its customer base in North America, especially among SMEs and regulated industries.
- Asia-Pacific: The company has extended its reach into the Asia-Pacific region, especially in tech-forward markets like Japan and Australia, where data protection is a growing concern.
CoSoSys Product Suite
CoSoSys specializes in Data Loss Prevention (DLP) and endpoint security solutions, with its flagship product being Endpoint Protector. The company’s product suite is designed to prevent data breaches, secure sensitive information, and ensure regulatory compliance across different operating systems and platforms.
1. Endpoint Protector
Endpoint Protector is CoSoSys’ all-in-one Data Loss Prevention (DLP) solution. It helps organizations prevent data breaches by controlling the flow of sensitive information across various endpoints. The solution offers a modular approach, allowing companies to select the features they need based on their security requirements.
Key Features:
- Device control: Prevent unauthorized use of USB devices and removable media by controlling access and blocking unapproved devices.
- Content-aware protection: Scans and monitors data transferred via removable devices, email, or applications based on predefined content policies.
- Compliance management: Implements regulations like GDPR, HIPAA, and PCI DSS by detecting and blocking sensitive information.
- Enforced encryption: Automatically encrypts sensitive data transferred to removable storage devices, protecting data even if the device is lost or stolen.
- eDiscovery: Searches for sensitive data stored locally on endpoints to identify non-compliant files and take corrective actions (e.g., encrypt, delete, or relocate).
- Cross-platform compatibility: Supports Windows, macOS, Linux, and thin-client environments, making it one of the most versatile DLP solutions on the market.
2. Device Control
CoSoSys offers Device Control features as part of its product suite, helping organizations manage and secure peripheral devices, such as USB memory sticks. The core of this function is the control of the USB ports on each computer run by the company.
Key Features:
- Granular Control: All USB ports are blocked by default but they are not turned off – the central controller can still get information for them and selectively allow them to function.
- Cross-platform support: Supports Windows, macOS, and Linux, so will manage device control policies across different operating systems from a single interface.
- Remote access management: You can grant or revoke USB access remotely, even when devices are offline. This feature ensures continuous protection and compliance.
- Auto-detection: The software automatically scans and classifies new devices, identifying each by serial number, making it easy to manage and secure them.
- Enhanced security: By controlling USB and peripheral ports, it helps protect against USB malware, BadUSB attacks, and other threats.
2. Content eDiscovery
CoSoSys’ eDiscovery tool helps businesses locate sensitive data stored across endpoints to ensure compliance with data protection regulations. This product creates a foundation in Endpoint Protector to provide comprehensive data-at-rest protection.
Key Features:
- Sensitive data search: Scans endpoints for sensitive information such as PII, financial records, and intellectual property stored locally.
- Security policy awareness: Identifies non-compliant files and generates detailed reports for review.
- File filtering: Supports filtering by file type, location, and content type to efficiently identify specific sensitive information.
- Compliance auditing: Ensures that regulations like GDPR, HIPAA, and CCPA are complied with by allowing companies to audit where data is stored.
3. Content Aware Protection
CoSoSys’ Content Aware Protection system works on information provided by the eDiscovery process and access rights register. So, each piece of sensitive data has already been identified and you have a list of who is allowed to read, update, or move that type of data. This unit enforces the rules laid out in the access rights manager.
Key Features:
- Contextual scanning: Prevents sensitive data from being inappropriately shared
- Multiple operating systems: Accesses computers running Windows, macOS, and Linux.
- Data compliance: Compatible with GDPR, HIPAA, CCPA, and other regulations.
- Continuous protection: The protection system continues to operate even when the host is offline.
4. USB Enforced Encryption (EasyLock)
CoSoSys’ USB encryption software was originally a separate product called EasyLock. It has since been integrated into the Endpoint Protector system and developed further. It is designed to securely encrypt data transferred to removable storage devices like USB flash drives, external hard drives, and memory cards.
Key Features:
- Strong encryption: Uses AES 256-bit encryption, a government-grade standard, to protect sensitive data stored on USB devices.
- Cross-platform support: Encrypted USB devices can be accessed on both Windows and macOS systems without requiring additional software.
- Centralized management: Integrated with Endpoint Protector to enforce encryption policies and ensure compliance with company-wide security protocols.
- Portable and secure: Ensures that data remains secure even if the USB device is used outside the organization, thanks to portable encryption.
CoSoSys’ product suite is, in fact, one product – Endpoint Protector – with multiple modules. It isn’t possible to pay for just one module, you sign up for the entire platform.
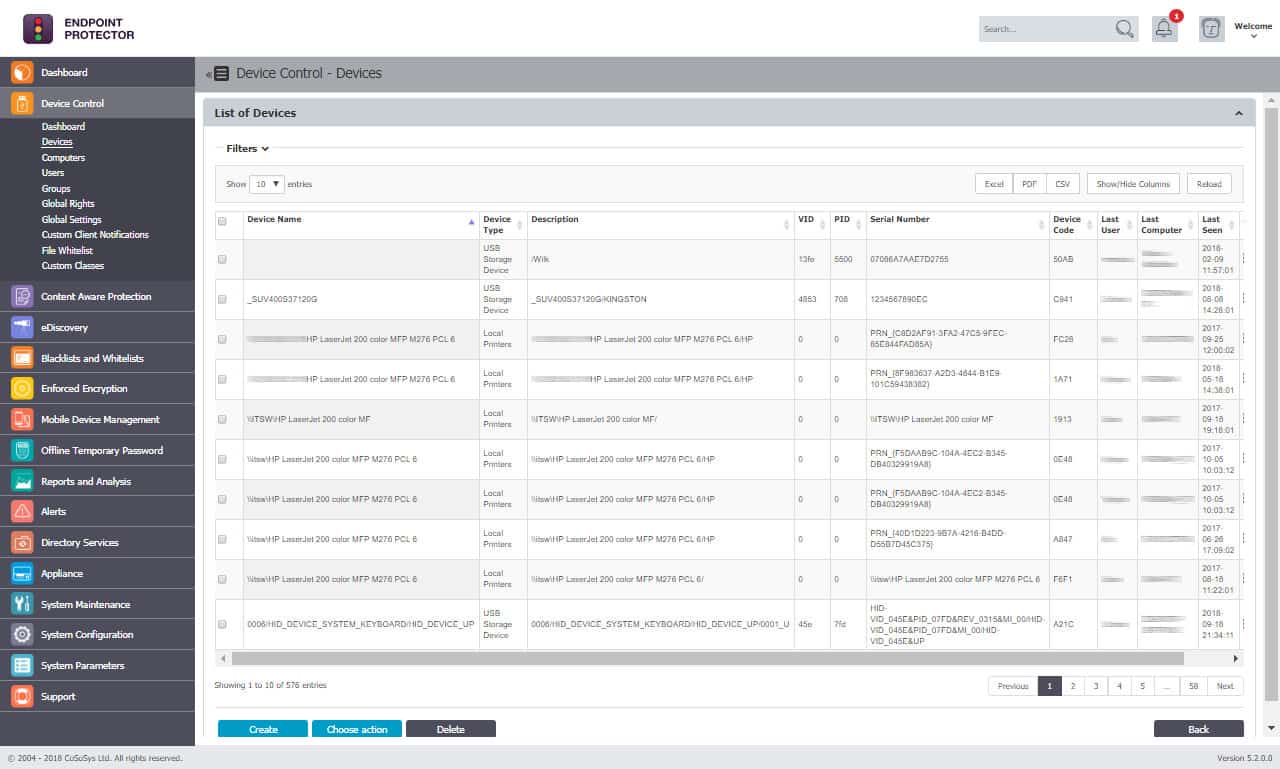
Endpoint Protector is the core product of the CoSoSys platform. It is a data loss prevention (DLP) solution designed to protect sensitive data and ensure compliance with data protection regulations.
Key Features:
- Granular permissions: Control access to USB and peripheral ports, preventing unauthorized devices from connecting.
- Cross-platform compatibility: The solution works across Windows, macOS, and Linux, providing a unified management experience.
- Remote management: You can manage device access remotely, ensuring continuous protection even when devices are offline.
- Data scanning: Monitors and controls data transfers based on predefined content policies, ensuring sensitive information is protected.
- File type filtering: Blocks or allows transfers based on file types, helping to prevent data leaks.
- Network monitoring: Looks for sensitive data in motion across the network, providing an additional layer of security.
The Endpoint Protector system combines a permissions system with controls over files and devices. This means that it doesn’t completely block access to data, so those employees who are authorized to access data are still able to perform their duties.
Pros:
- Email protection: Scans and controls email content to prevent unauthorized data sharing.
- Compliance reporting: Logs and reports to help ensure compliance with regulations like GDPR, HIPAA, and PCI DSS.
- Policy enforcement: The solution enforces data protection policies across the organization, helping to maintain a secure environment.
Cons:
- No price list: CoSoSys doesn’t publish a price list.
Endpoint Protector is a software package, not a SaaS platform, which means that you need to install the system and maintain the software. The central server runs as a virtual appliance on VMware, Citrix, Microsoft Hyper-V, Oracle VirtualBox, among others. It is also possible to install it on your cloud account at Amazon Web Services (AWS), Azure, or Google Cloud Platform (GCP). Each endpoint needs a client program installed on it and this is available for Windows, macOS, and Linux.
Other Notable Products
CoSoSys only has one product, which is Endpoint Protector. However, that purchase gets a buyer a series of tools. These include:
1. Device Control
Endpoint Protector’s Device Control secures the USB and peripheral ports on your endpoints. It blocks device access by default, and then the administrator can choose to allow devices to connect on a case-by-case basis. Devices can be permitted to connect to one computer, many, or all. It is also possible to specify that a device can only be attached to a company endpoint by a specific user. The system includes automatic device detection and classification, simplifying the management of new devices.
The solution supports multiple operating systems, including Windows, macOS, and Linux, ensuring comprehensive coverage across diverse IT environments. Additionally, its remote management capabilities allow administrators to grant or revoke device access even when endpoints are offline, maintaining continuous protection. Endpoint Protector’s Device Control is particularly valuable for organizations looking to enforce strict data security policies and comply with regulations such as GDPR, HIPAA, and PCI DSS.
2. Enforced Encryption
Endpoint Protector’s Enforced Encryption is a critical feature designed to ensure that sensitive data transferred to USB storage devices is always encrypted. This feature automatically encrypts data copied to USB drives, making it accessible only to authorized users. By enforcing encryption, it helps prevent data breaches and unauthorized access, even if the USB device is lost or stolen. The encryption process is seamless and transparent to users, ensuring that it does not disrupt their workflow.
This tool supports various encryption standards. A central console allows administrators to manage encryption keys and simplifies the process of key distribution and recovery, ensuring that encrypted data remains accessible to authorized personnel while maintaining high security standards. The feature also includes detailed logging and reporting capabilities, enabling organizations to track and audit encrypted data transfers for compliance purposes.
Major Competitors
Here are six major competitors to Endpoint Protector:
- Forcepoint DLP Known for its robust data loss prevention capabilities, Forcepoint DLP offers comprehensive protection against data breaches. It provides advanced analytics and real-time monitoring to safeguard sensitive information across endpoints, networks, and cloud environments.
- Symantec Data Loss Prevention Βy Broadcom delivers extensive data protection through content discovery, monitoring, and blocking. It supports a wide range of data types and integrates seamlessly with other security tools to ensure compliance and prevent data leaks.
- Trellix Offers a flexible and scalable DLP solution that protects sensitive data across endpoints, networks, and cloud services. It features advanced threat detection and response capabilities, making it suitable for large enterprises.
- Proofpoint DLP Focuses on protecting data in motion, at rest, and in use. It provides detailed visibility and control over data flows, helping organizations prevent data breaches and comply with regulations.
- GTB Technologies Offers a highly customizable DLP solution that protects sensitive data across various channels. It features real-time data classification, monitoring, and blocking to prevent unauthorized data transfers.
- Digital Guardian Provides comprehensive data protection through endpoint and network DLP. It offers detailed visibility into data usage and movement, helping organizations enforce data security policies and prevent data breaches.
Spotlight Wrap Up
CoSoSys has had a very interesting history and the company has been a little hard to track at times. However, the business is now mature and no longer a startup trying to force its way into the market. The business is part of Netwrix, which has also followed its own journey from newcomer to industry veteran.
The takeover by Netwrix is very recent and it is not clear yet whether the company will treat its new division as an independent operation or fully integrate the Endpoint Protector into its brand. However, the takeover will give Endpoint Protector a larger development budget, so expect some big changes with this tool over the next few years.
Source link