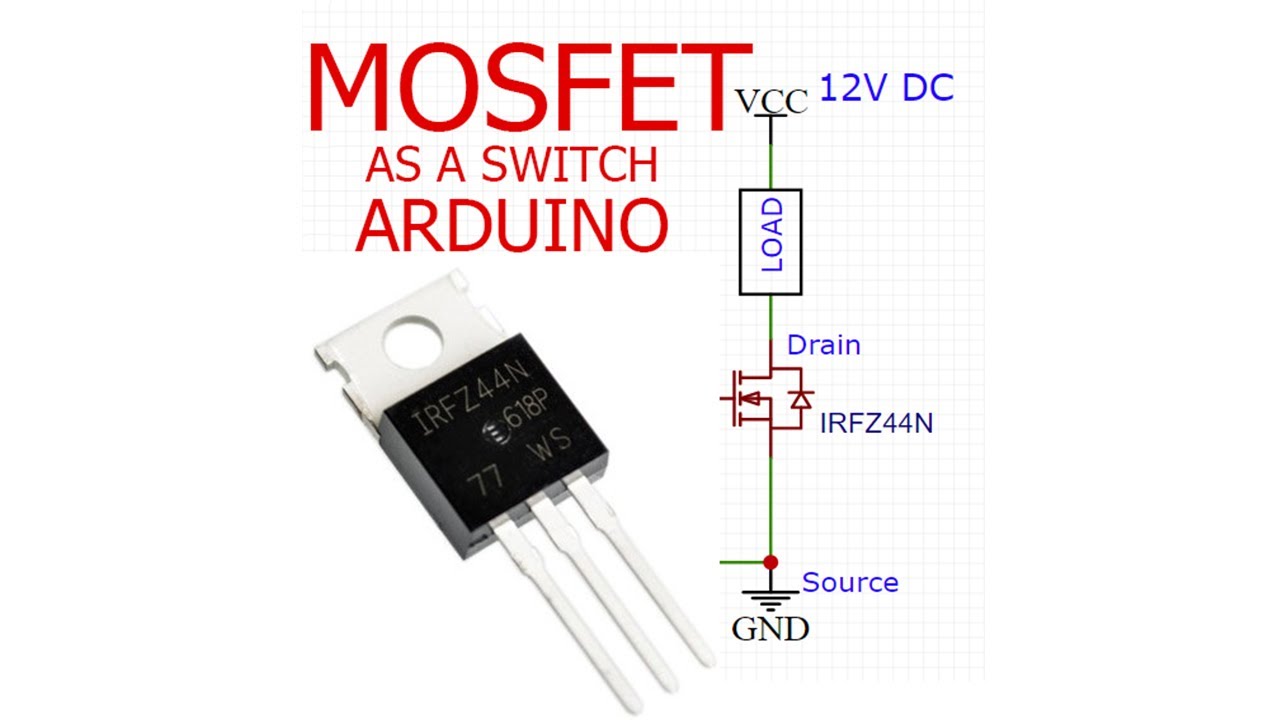
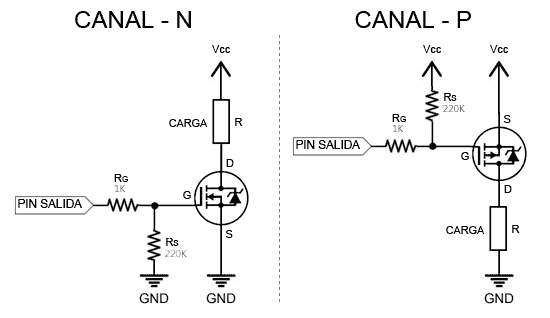
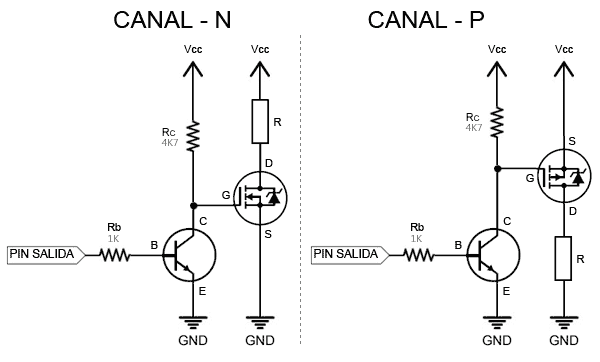
Interruptor de bajo voltaje para Arduino, módulo Mosfet de 3V, 5V, 12V, 24V, 36V, para conectar, IO, MCU, PWM, Control de velocidad del Motor, 22A|Circuitos integrados| - AliExpress
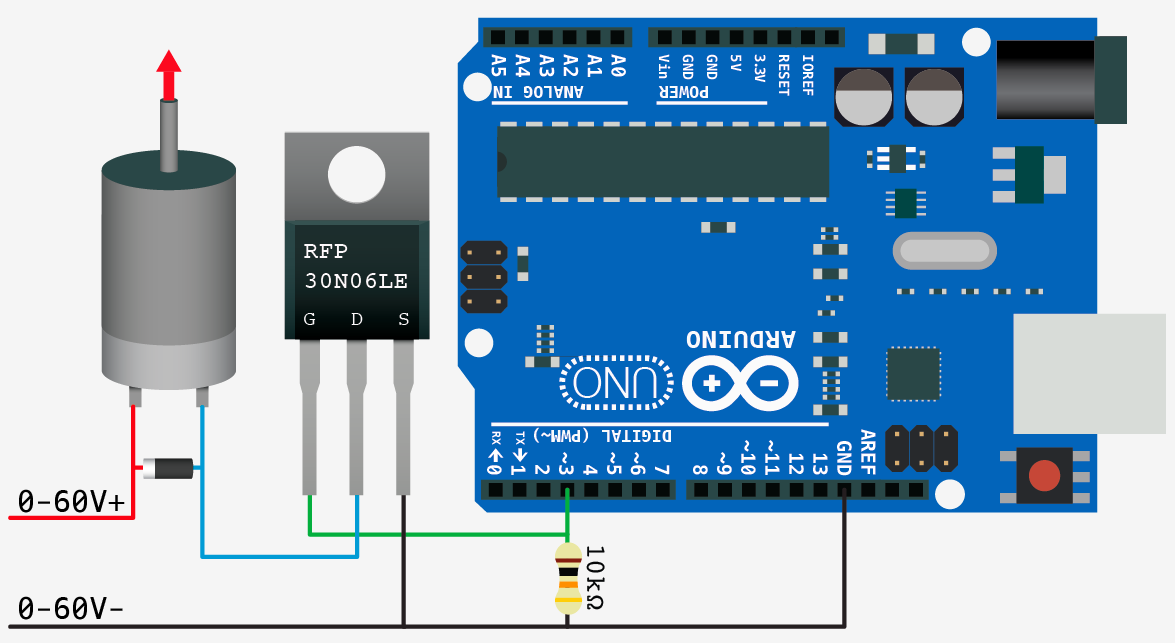
How to convert the PWM signal of Arduino to 12V using N-Channel MOSFET and then use a voltage divider on the drain - Quora

Interruptor Mosfet de bajo voltaje para Arduino, 3V, 5V, 12V, 24V, 36V, módulo para conectar IO, MCU, PWM, Control de velocidad del Motor, 22A - AliExpress Productos electrónicos

Interruptor Mosfet de bajo voltaje para Arduino, 3V, 5V, 12V, 24V, 36V, módulo para conectar IO, MCU, PWM, Control de velocidad del Motor, 22A|high voltage|mosfet modulehigh voltage module - AliExpress

Bajo control De alto voltaje 12V 24V 36V interruptor Módulo Mosfet para Arduino Connect IO MCU PWM Control comprar a buen precio — entrega gratuita, reseñas reales con fotos — Joom