YouTubers extorted via copyright strikes to spread malware

Cybercriminals are sending bogus copyright claims to YouTubers to coerce them into promoting malware and cryptocurrency miners on their videos.
The threat actors take advantage of the popularity of Windows Packet Divert (WPD) tools that are increasingly used in Russia as they help users bypass internet censorship and government-imposed restrictions on websites and online services.
YouTube creators catering to this audience publish tutorials on how to use various WPD-based tools to bypass censorship and are being targeted by threat actors posing as the copyright holders of these tools.
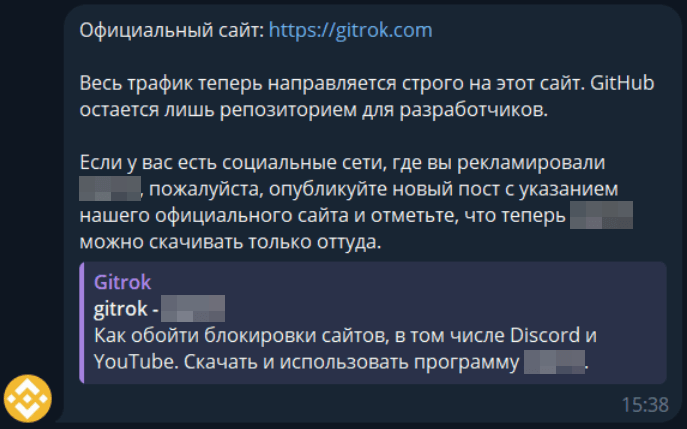
In most cases seen by Kaspersky, the threat actors claim to be the original developers of the presented restriction bypass tool, filing a copyright claim with YouTube and then contacting the creator to offer a resolution in the form of including a download link they provide.
At the same time, they threaten that non-compliance will result in two more “strikes” on YouTube, which could lead to a channel ban based on the platform’s “three strikes” policy.
In other cases, the attackers contact the creator directly, impersonating the tool’s developers and claiming that the original tool has a new version or new download link, asking the creator to change it on their video.
Source: Kaspersky
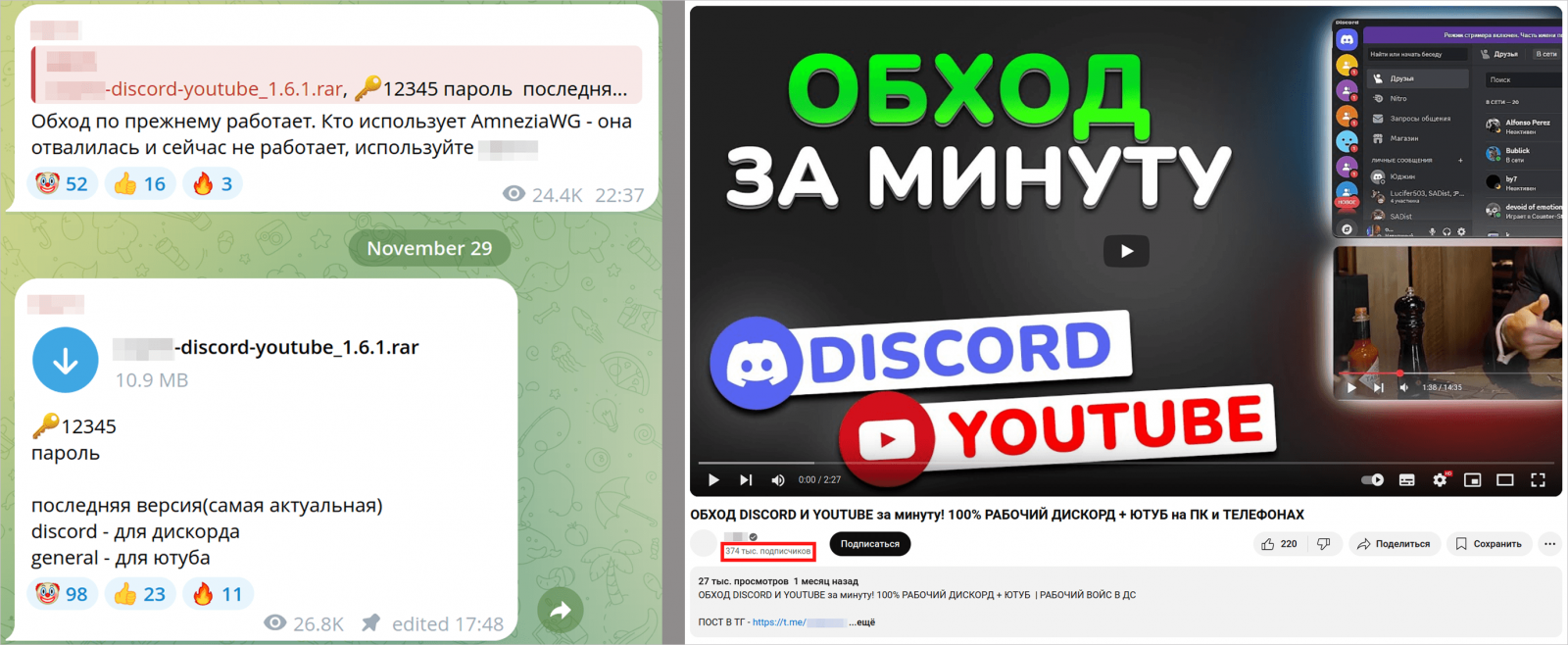
The creators, fearing they will lose their channels, give in to the threat actors’ demands, and agree to add links in their videos to GitHub repositories that host the said Windows Packet Divert (WPD) tools. However, these are trojanized versions that include a cryptominer downloader instead.
Kaspersky has seen this promotion of laced WPD tools take place on a YouTube video that generated over 400,000 views, with the malicious link reaching 40,000 downloads before it got removed.
A Telegram channel with 340,000 subscribers has also promoted the malware under the same disguise.
“According to our telemetry, the malware campaign has affected more than 2,000 victims in Russia, but the overall figure could be much higher,” warns Kaspersky.
Source: Kaspersky
SilentCryptoMiner deployment
The malicious archive downloaded from the GitHub repositories contains a Python-based malware loader that is launched using PowerShell via a modified start script (‘general.bat’).
If the victim’s antivirus disrupts this process, the start script delivers a ‘file not found’ error message suggesting that the user disables their antivirus and re-download the file.
The executable fetches the second-stage loader only for Russian IP addresses and executes it on the device.
The second stage payload is another executable whose size was bloated to 690 MB to evade antivirus analysis, while it also features anti-sandbox and virtual machine checks.
The malware loader turns off Microsoft Defender protections by adding an exclusion and creates a Windows service named ‘DrvSvc’ for persistence between reboots.
Eventually, it downloads the final payload, SilentCryptoMiner, a modified version of XMRig capable of mining multiple cryptocurrencies, including ETH, ETC, XMR, and RTM.
The coin miner fetches remote configurations from Pastebin every 100 minutes so it can be updated dynamically.
For evasion, it is loaded into a system process like ‘dwm.exe’ using process hollowing and pauses mining activity when the user launches monitoring tools like Process Explorer and the Task Manager.
Although the campaign discovered by Kaspersky primarily targets Russian users, the same tactics may be adopted for broader-scoped operations that also deliver higher-risk malware like info-stealers or ransomware.
Users should avoid downloading software from URLs in YouTube videos or descriptions, especially from smaller to medium-sized channels that are more susceptible to scams and blackmail.
Source link