Chinese hackers use custom malware to spy on US telecom networks

The Chinese state-sponsored Salt Typhoon hacking group uses a custom utility called JumbledPath to stealthily monitor network traffic and potentially capture sensitive data in cyberattacks on U.S. telecommunication providers.
Salt Typhoon (aka Earth Estries, GhostEmperor, and UNC2286) is a sophisticated hacking group active since at least 2019, primarily focusing on breaching government entities and telecommunications companies.
Recently, the U.S. authorities have confirmed that Salt Typhoon was behind several successful breaches of telecommunication service providers in the U.S., including Verizon, AT&T, Lumen Technologies, and T-Mobile.
It was later revealed that Salt Typhoon managed to tap into the private communications of some U.S. government officials and stole information related to court-authorized wiretapping requests.
Last week, the Recorded Future’s Insikt Group reported that Salt Typhoon targeted over 1,000 Cisco network devices, more than half from the U.S., South America, and India, between December 2024 and January 2025,
Today, Cisco Talos revealed more details about the threat actor’s activity when they breached major telecommunications companies in the U.S., which in some cases spanned over three years.
Salt Typhoon’s tactics
Cisco says Salt Typhoon hackers infiltrated core networking infrastructure primarily through stolen credentials. Apart from a single case involving exploitation of the Cisco CVE-2018-0171 flaw, the cybersecurity company has seen no other flaws, known or zero-days, being exploited in this campaign.
“No new Cisco vulnerabilities were discovered during this campaign,” states Cisco Talos in its report. “While there have been some reports that Salt Typhoon is abusing three other known Cisco vulnerabilities, we have not identified any evidence to confirm these claims.”
While Salt Typhoon primarily gained access to targeted networks using stolen credentials, the exact method of obtaining the credentials remains unclear.
Once inside, they expanded their access by extracting additional credentials from network device configurations and intercepting authentication traffic (SNMP, TACACS, and RADIUS).
They also exfiltrated device configurations over TFTP and FTP to facilitate lateral movement, which contained sensitive authentication data, weakly encrypted passwords, and network mapping details.
The attackers demonstrated advanced techniques for persistent access and evasion, including frequently pivoting between different networking devices to hide their traces and using compromised edge devices to pivot into partner telecom networks.
The threat actors were also observed modifying network configurations, enabling Guest Shell access to execute commands, altering access control lists (ACLs), and creating hidden accounts.
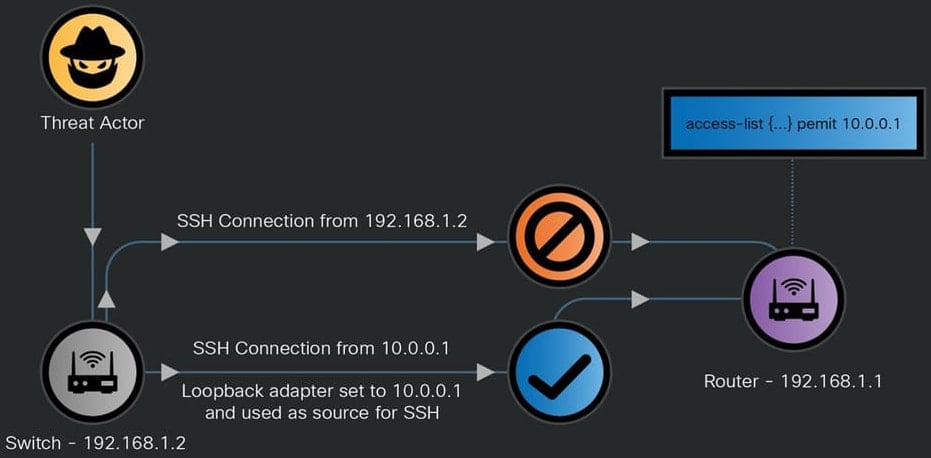
Source: Cisco
The custom JumbledPath malware
A primary component of the Salt Typhoon attacks was monitoring network activity and stealing data using packet-capturing tools like Tcpdump, Tpacap, Embedded Packet Capture, and a custom tool called JumbledPath.
JumpedPath is a Go-based ELF binary built for x86_64 Linux-based systems that allowed it to run on a variety of edge networking devices from different manufacturers, including Cisco Nexus devices.
JumbledPath allowed Salt Typhoon to initiate packet capture on a targeted Cisco device via a jump-host, an intermediary system that made the capture requests appear as if they originate from a trusted device inside the network while also obfuscating the attacker’s true location.
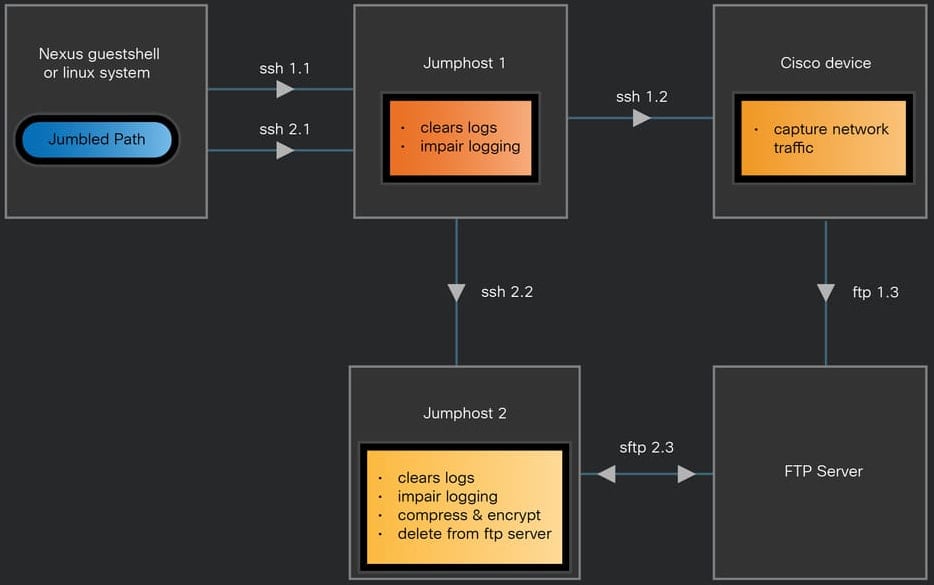
Source: Cisco
The same tool could also disable logging and clear existing logs to erase traces of its activity and make forensic investigations more difficult.
Cisco lists several recommendations to detect Salt Typhoon activity, such as monitoring for unauthorized SSH activity on non-standard ports, tracking log anomalies, including missing or unusually large ‘.bash_history’ files, and inspecting for unexpected configuration changes.
Over the past couple of years, Chinese threat actors have increasingly targeted edge networking devices to install custom malware that allows them to monitor network communications, steal credentials, or act as proxy servers for relayed attacks.
These attacks have targeted well-known manufacturers, including Fortinet, Barracuda, SonicWall, Check Point, D-Link, Cisco, Juniper, NetGear, and Sophos.
While many of these attacks exploited zero-day vulnerabilities, other devices were breached through compromised credentials or older vulnerabilities. Therefore, admins must apply patches to edge networking devices as soon as they are available.
Source link