CoGUI phishing platform sent 580 million emails to steal credentials

A new phishing kit named ‘CoGUI’ sent over 580 million emails to targets between January and April 2025, aiming to steal account credentials and payment data.
The messages impersonate major brands like Amazon, Rakuten, PayPal, Apple, tax agencies, and banks.
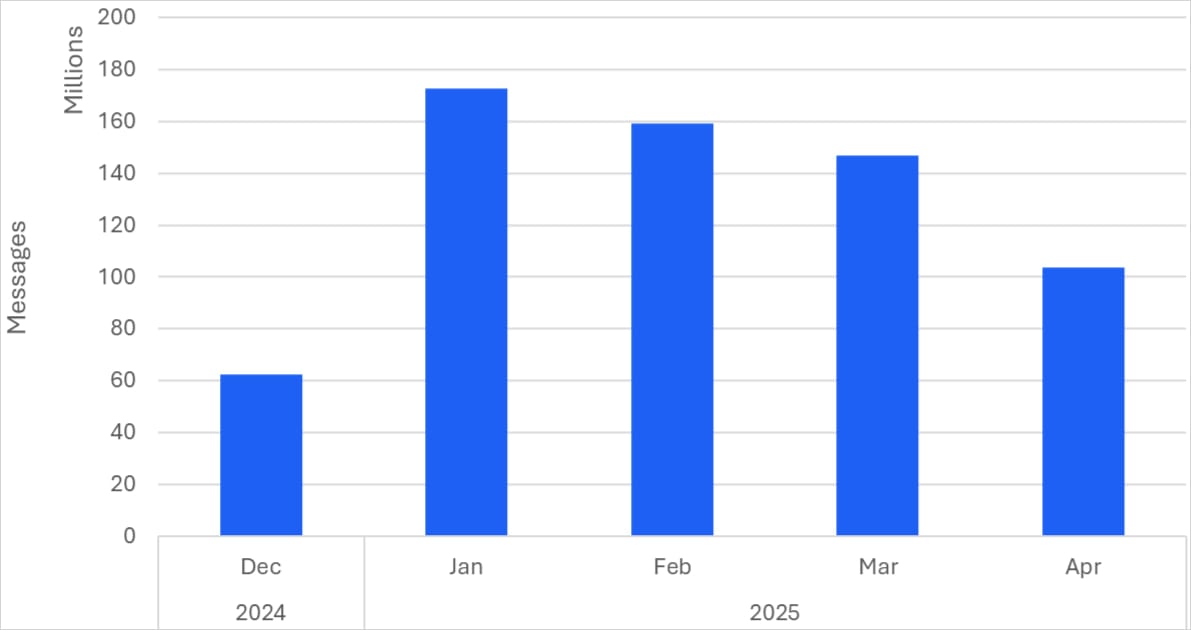
The activity culminated in January 2025, where 170 campaigns sent 172,000,000 phishing messages to targets, but the following months maintained equally impressive volumes.
Proofpoint researchers who discovered the CoGUI campaigns noted that it’s the highest volume phishing campaign they currently track. The attacks mainly target Japan, though smaller-scale campaigns were also directed at the United States, Canada, Australia, and New Zealand.
CoGUI has been active since at least October 2024, but Proofpoint started tracking it in December and onward.
Source: Proofpoint
The analysts found several similarities to the Darcula phishing kit, which has been linked to China-based operatives, and initially believed that the origin of the CoGUI attacks is the same.
However, upon deeper examination, Proofpoint concluded that the two phishing kits are unrelated even though they are both utilized by Chinese threat actors.
CoGUI attack chain
The attack starts with a phishing email impersonating a trusted brand, often having urgent subject lines requiring the recipient’s action.
The messages include a URL that redirects to a phishing website hosted on the CoGUI phishing platform, but the link only resolves if the target meets specific criteria pre-defined by the attackers.
These criteria include their IP address (location), browser language, operating system, screen resolution, and device type (mobile or desktop).
If the criteria aren’t met, victims are redirected to the brand’s legitimate site that was impersonated to reduce suspicion.
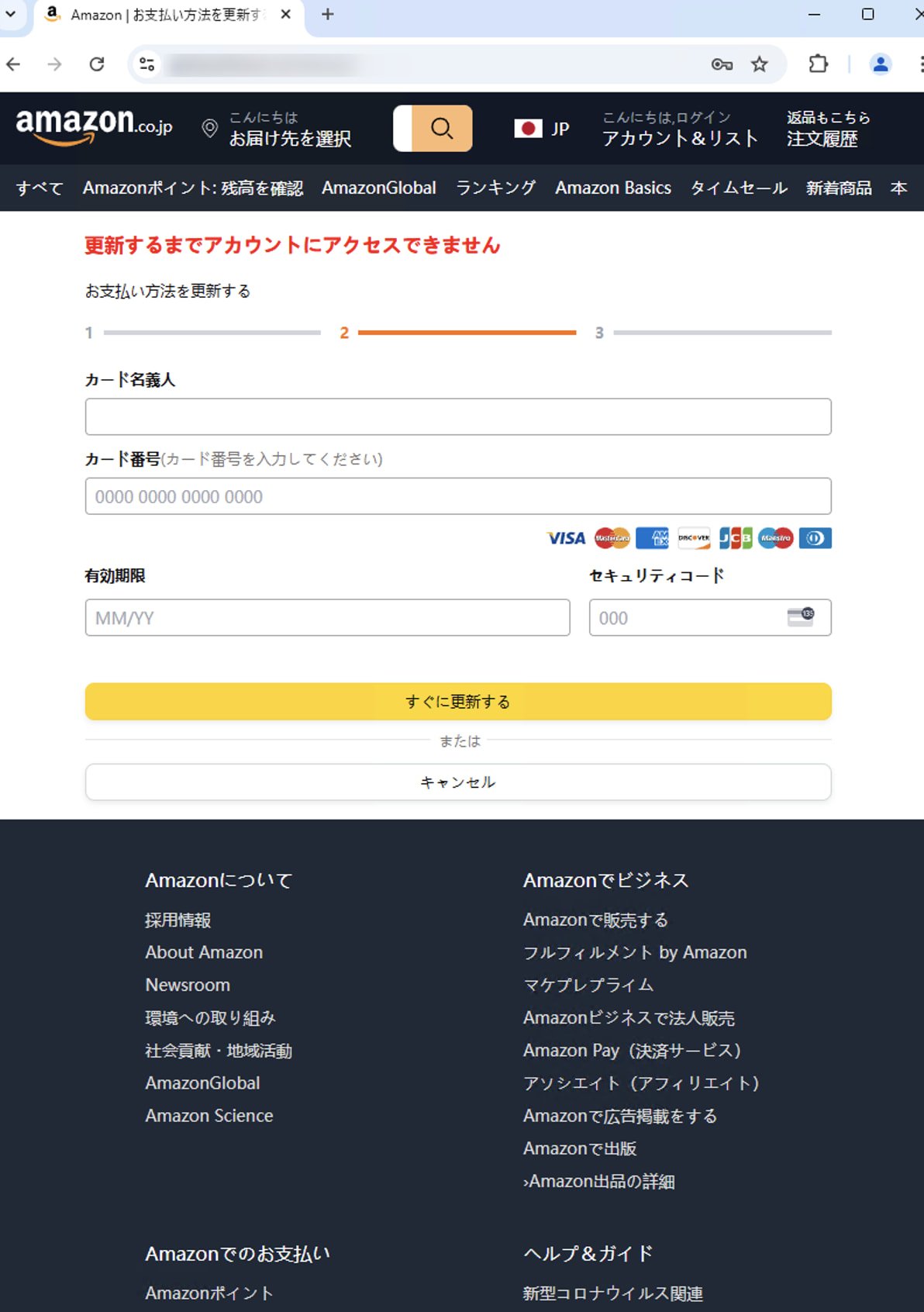
Valid targets are redirected to a phishing page featuring a fake login form that mimics the design of the real brand, tricking victims into entering their sensitive information.
Source: Proofpoint
Proofpoint has also found that CoGUI was behind smishing campaigns targeting the United States with ‘outstanding toll payment’ lures. However, it noted that most of that activity has now migrated to Darcula.
The researchers believe CoGUI facilitates the operations of multiple threat actors, primarily from China, who predominantly target Japanese users.
However, the kit could be adopted by other cybercriminals with a different targeting scope at any moment, resulting in massive attack waves hitting other countries.
The best way to mitigate phishing risks is never to act with haste when receiving emails requesting urgent action, and always log in to the claimed platform independently instead of following embedded links.
Source link