Fake “Security Alert” issues on GitHub use OAuth app to hijack accounts

A widespread phishing campaign has targeted nearly 12,000 GitHub repositories with fake “Security Alert” issues, tricking developers into authorizing a malicious OAuth app that grants attackers full control over their accounts and code.
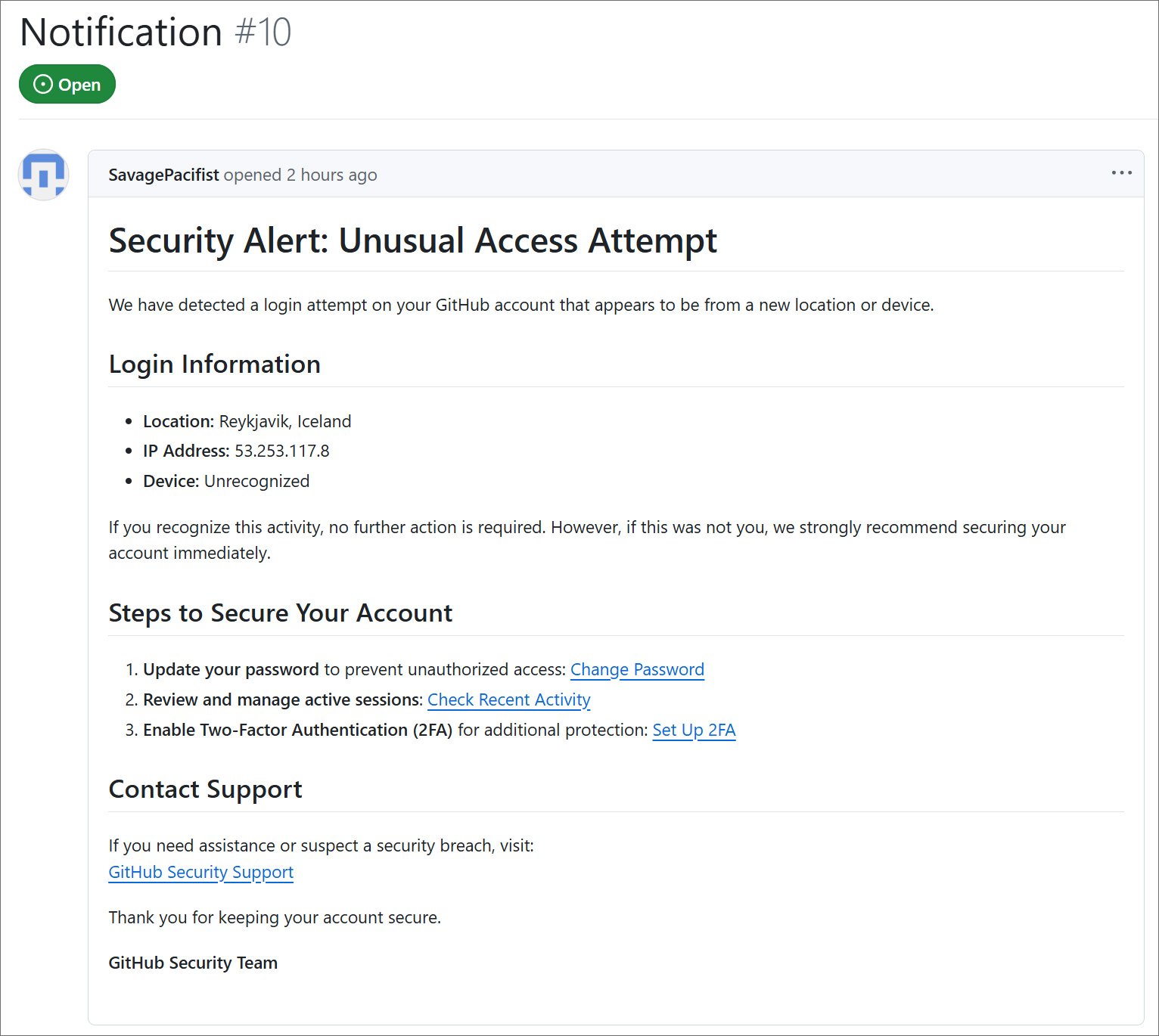
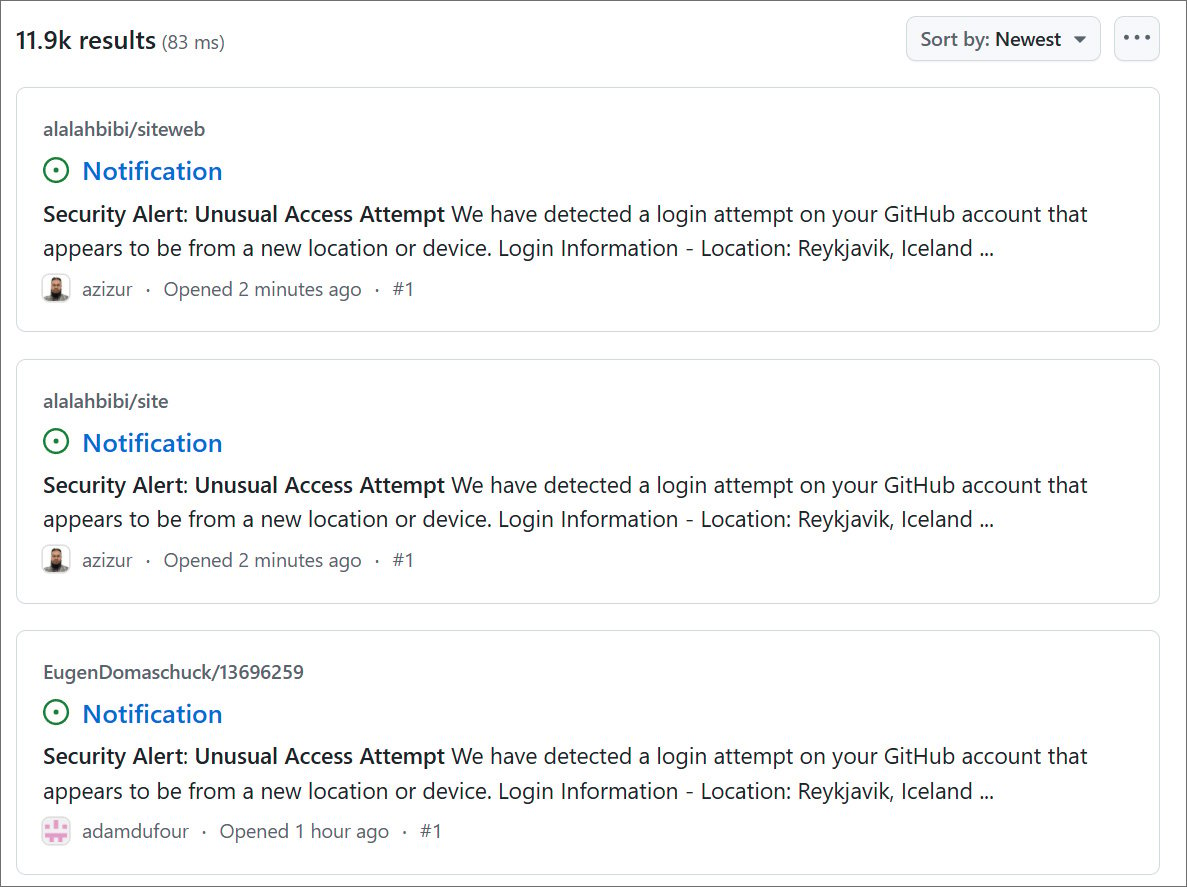
“Security Alert: Unusual Access Attempt We have detected a login attempt on your GitHub account that appears to be from a new location or device,” reads the GitHub phishing issue.
All of the GitHub phishing issues contain the same text, warning users that their was unusual activity on their account from Reykjavik, Iceland, and the 53.253.117.8 IP address.
Source: BleepingComputer
Cybersecurity researcher Luc4m first spotted the fake security alert, which warned GitHub users that their account was breached and that they should update their password, review and manage active sessions, and enable two-factor authentication to secure their accounts.
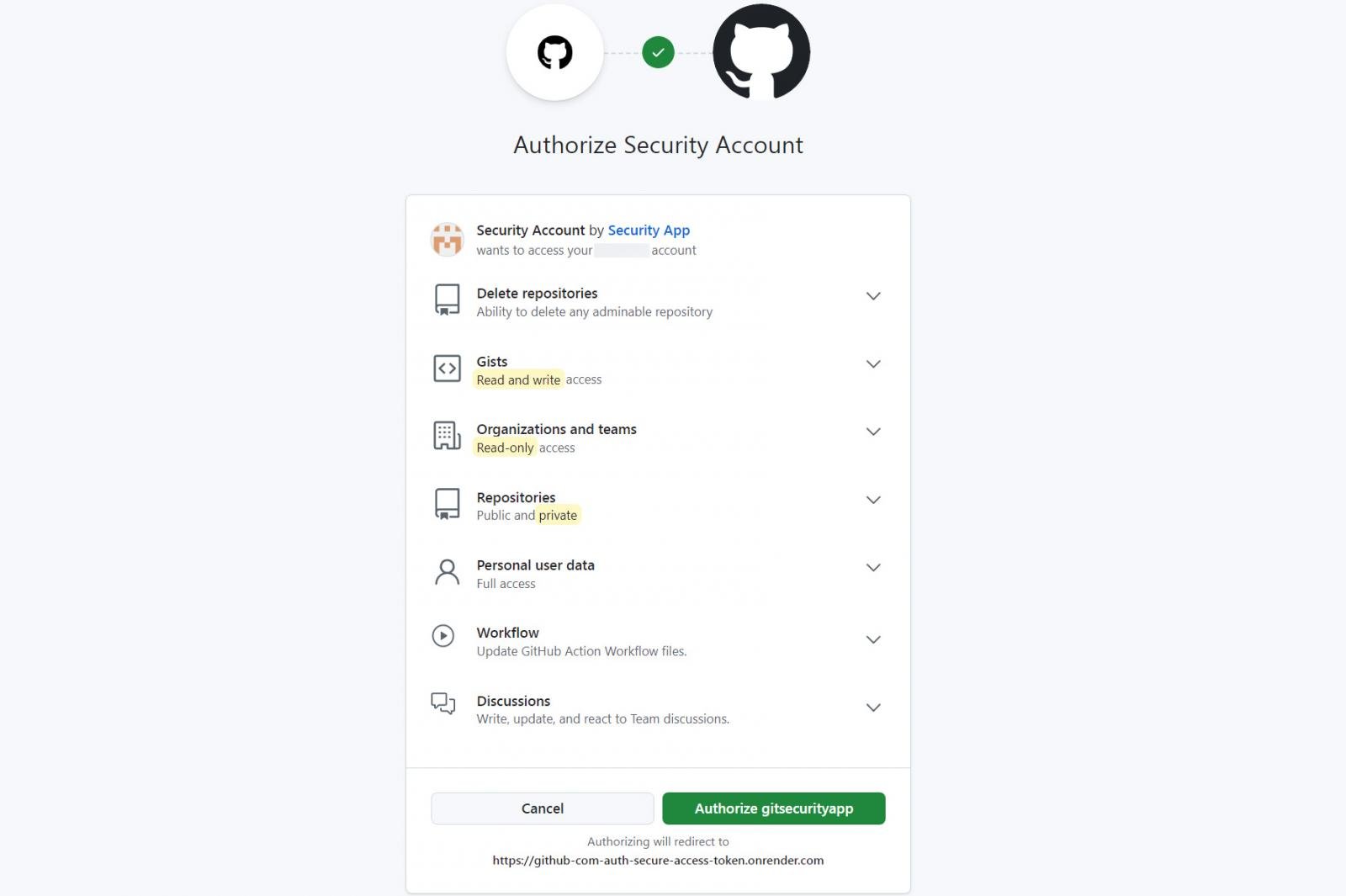
However, all of the links for these recommended actions lead to a GitHub authorization page for a “gitsecurityapp” OAuth app that requests a lot of very risky permissions (scopes) and would allow an attacker full access to a user’s account and repositories.
Source: BleepingComputer
The requested permissions and the access they provide are listed below:
- repo: Grants full access to public and private repositories
- user: Ability to read and write to the user profile
- read:org: Read organization membership, organization projects, and team membership
- read: discussion, write:discussion: Read and write access to discussions
- gist: Access to GitHub gists
- delete_repo: Permission to delete repositories
- workflows, workflow, write:workflow, read:workflow, update:workflow: Control over GitHub Actions workflows
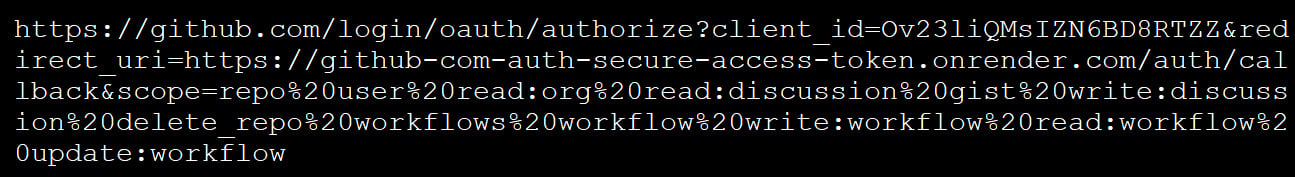
If a GitHub user logs in and authorizes the malicious OAuth app, an access token will generated and sent back to the app’s callback address, which in this campaign has been various web pages hosted on onrender.com (Render).
Source: BleepingComputer
The phishing campaign started this morning at 6:52 AM ET and is ongoing, with almost 12,000 repositories targeted in the attack. However, the number fluctuates, indicating that GitHub is likely responding to the attack.
Source: BleepingComputer
If you were impacted by this phishing attack and mistakenly gave authorization to the malicious OAuth app, you should immediately revoke its access by going into the GitHub Settings and then Applications.
From the Applications screen, revoke access to any GitHub Apps or OAuth apps that are unfamiliar or suspicious. In this campaign, you should look for apps named similarly to ‘gitsecurityapp.’
You should then look for new or unexpected GitHub Actions (Workflows) and whether private gists were created.
Finally, rotate your credentials and authorization tokens.
BleepingComputer contacted GitHub about the phishing campaign and will udpate this story when we get a response.
Source link