Malicious PirateFi game infects Steam users with Vidar malware

A free-to-play game named PirateFi in the Steam store has been distributing the Vidar infostealing malware to unsuspecting users.
The title was present in the Steam catalog for almost a week, between February 6th and February 12th, and was downloaded by up to 1,500 users. The distribution service is sending notices to potentially impacted users, advising them to reinstall Windows out of an abundance of caution.
Malware on Steam
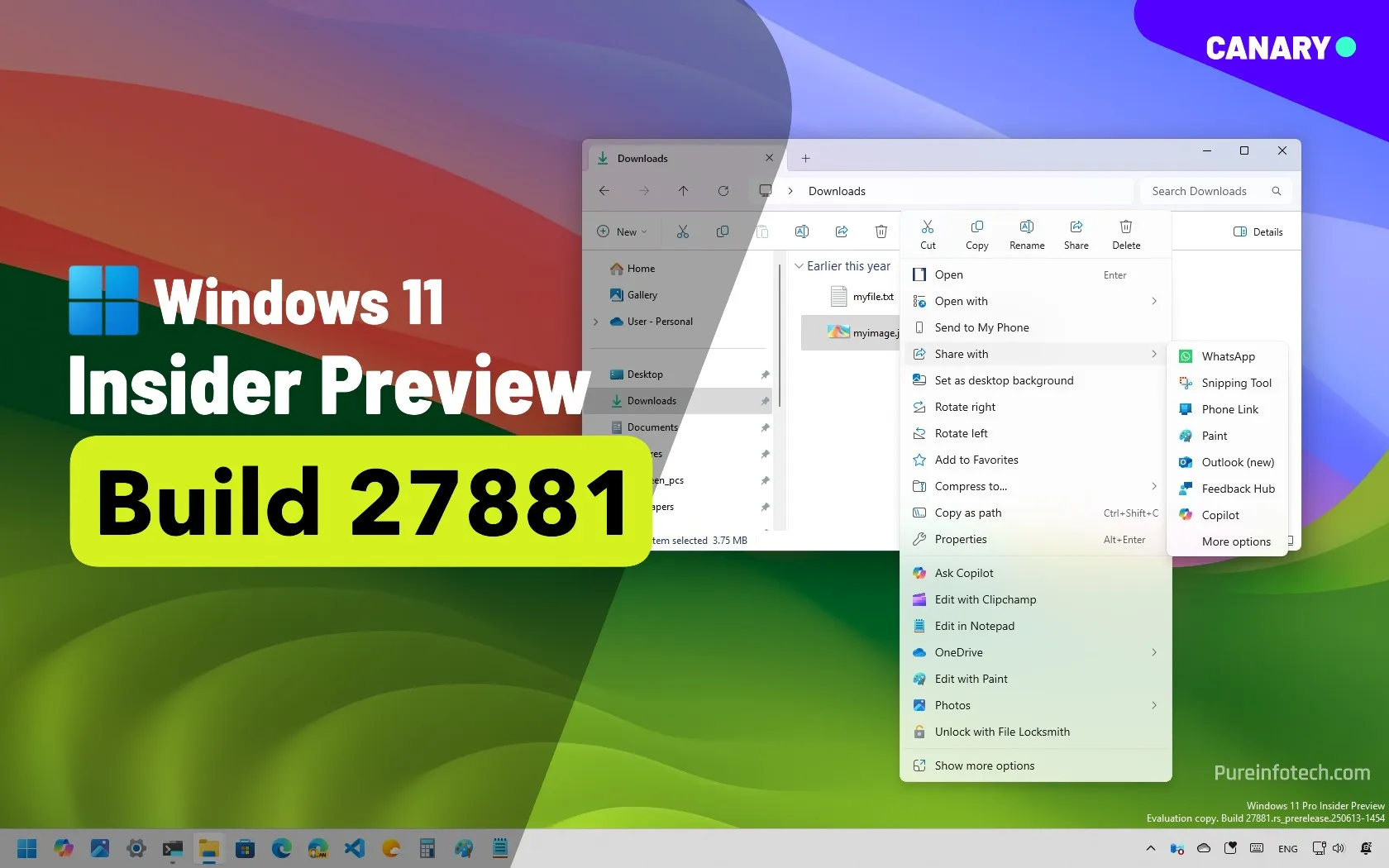
PirateFi was released on Steam last week by Seaworth Interactive, and received positive reviews. It is described as a survival game set in a low-poly world involving base building, weapon crafting and food gathering.
Source: Internet Archive
Earlier this week though, Steam discovered that the game contained malware but the service did not specify the exact type.
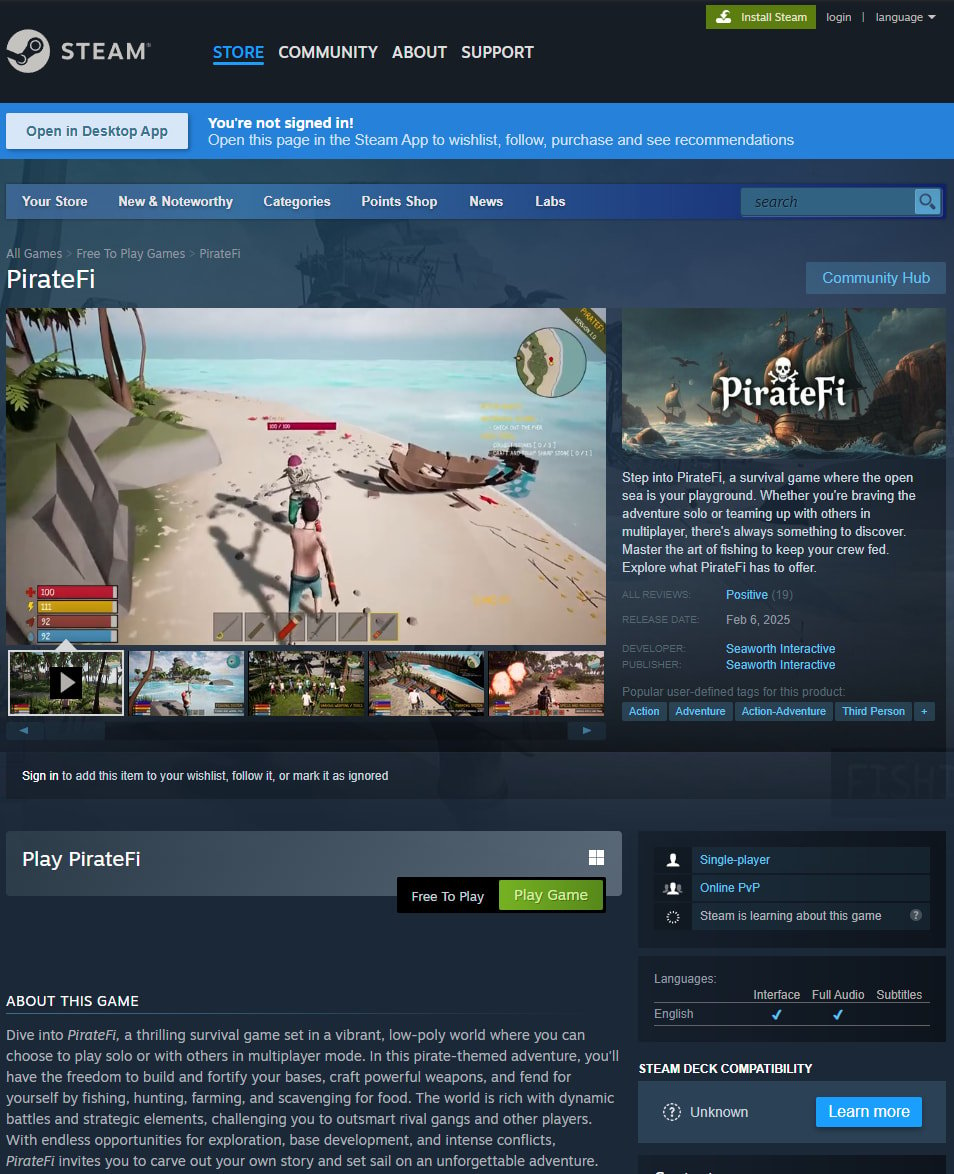
“The Steam account of the developer for this game uploaded builds to Steam that contained suspected malware,” reads the notification.
“You played PirateFi (3476470) on Steam while these builds were active, so it is likely that these malicious files launched on your computer,” the service warns.
The recommended measures for the notification recipients include running a full system scan using an up-to-date antivirus, checking for newly installed software they don’t recognize, and considering an OS format.
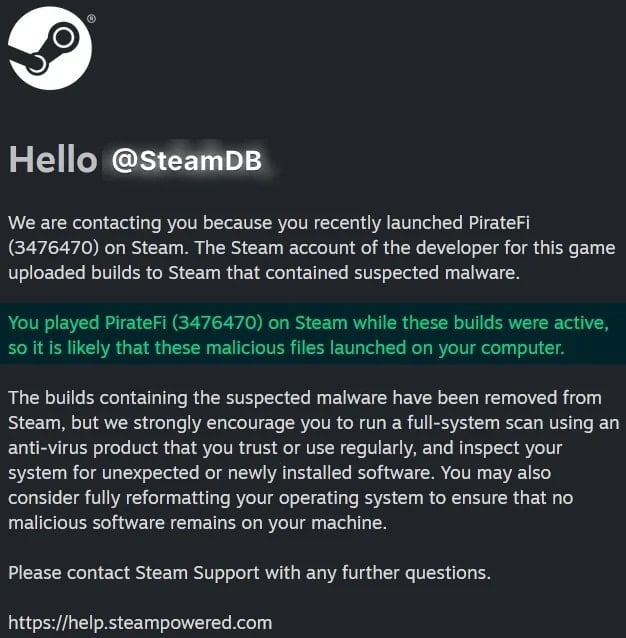
Source: SteamDB
Impacted users have also posted warnings on the title’s Steam Community page, telling others not to launch the game as their antivirus recognized it as malware.
Marius Genheimer of SECUINFRA Falcon Team obtained a sample of the malware distributed through PirateFi and identified it as a version of the Vidar infostealer.
“If you are one of the players who downloaded this “game”: Consider the credentials, session cookies and secrets saved in your browser, email client, cryptocurrency wallets etc. compromised,” advises SECUINFRA.
The recommendation is to change the passwords for all potentially affected accounts and activate the multi-factor authentication protection where possible.
The malware, identified as Vidar based on dynamic analysis and YARA signature matches, was hidden in a file called Pirate.exe as a payload (Howard.exe) packed with InnoSetup installer.
Genheimer told BleepingComputer that the threat actor modified the game files several times, using various obfuscation techniques and changing the command-and-control servers for credential exfiltration.
The researcher believes that the web3/blockchain/cryptocurrency references in the PirateFi name were intentional, to lure a specific player base
Steam did not publish figures on how many users have been impacted by the PirateFi malware but statistics on the title’s page shows that up to 1,500 individuals may be impacted.
Malware infiltrating the Steam store is not common, but it’s not unprecedented either. In February 2023, Steam users were targeted by malicious Dota 2 game modes that leveraged a Chrome n-day exploit to perform remote code execution on the players’ computers.
In December 2023, a mod for the then-popular Slay the Spire indie strategy game was compromised by hackers who injected an ‘Epsilon’ infostealer dropper into it.
Steam has introduced additional measures like SMS-based verification to protect players from unauthorized malicious updates, but the case of PirateFi shows that these measures are insufficient.
Source link