Microsoft Trust Signing service abused to code-sign malware

Cybercriminals are abusing Microsoft’s Trusted Signing platform to code-sign malware executables with short-lived three-day certificates.
Threat actors have long sought after code-signing certificates as they can be used to sign malware to appear like they are from a legitimate company.
Signed malware also has the advantage of potentially bypassing security filters that would normally block unsigned executables, or at least treat them with less suspicion.
The holy grail for threat actors is to obtain Extended Validation (EV) code-signing certificates, as they automatically gain increased trust from many cybersecurity programs due to the more rigorous verification process. Even more important, EV certificates are believed to gain a reputation boost in SmartScreen, helping to bypass alerts that would normally be displayed for unknown files.
However, EV code-singing certificates can be difficult to obtain, requiring them to be stolen from other companies or for threat actors to set up fake businesses and spend thousands of dollars to purchase one. Furthermore, once the certificate is used in a malware campaign, it is usually revoked, making it unusable for future attacks.
Abusing Microsoft Trusted Signing service
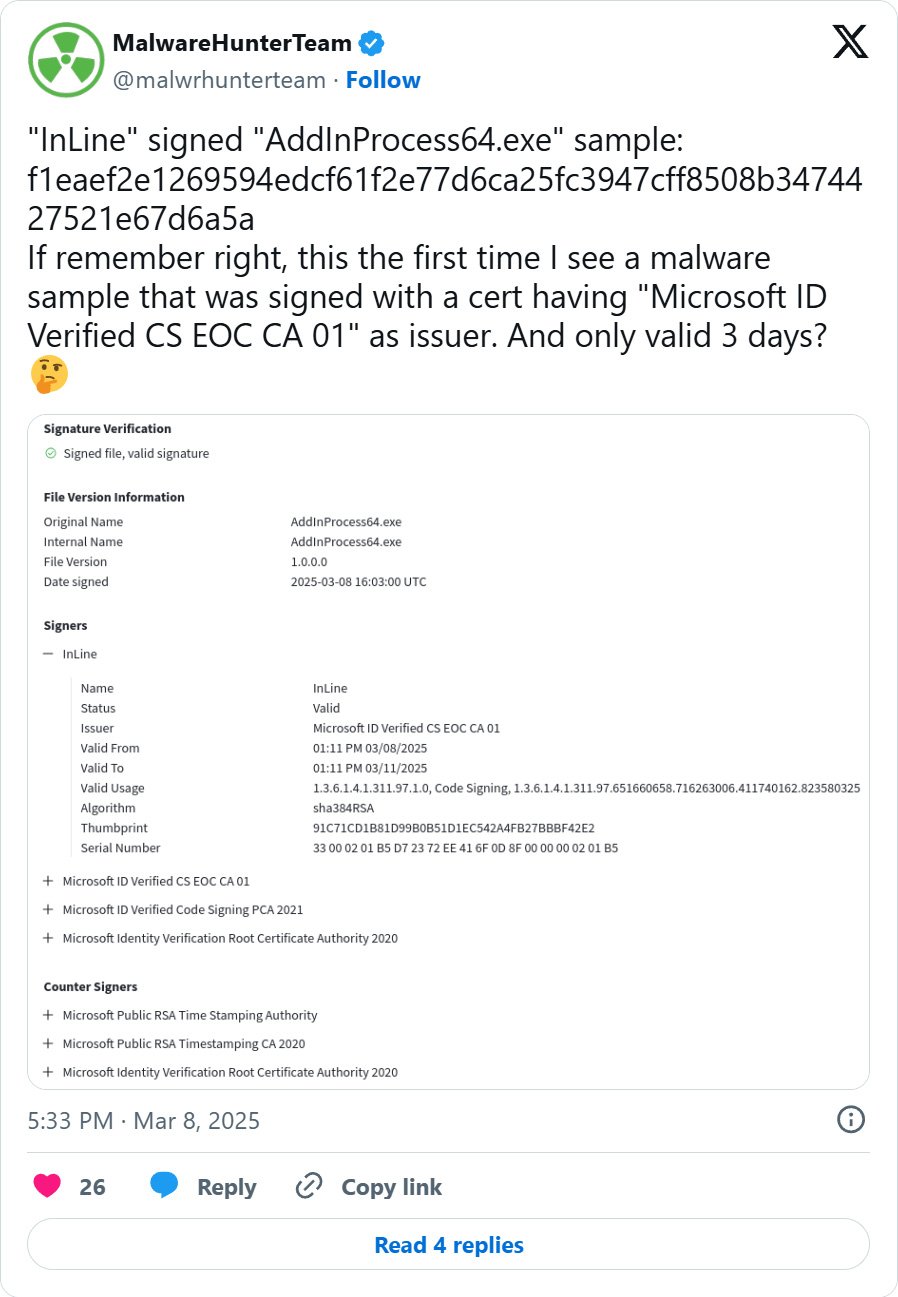
Recently, cybersecurity researchers have seen threat actors utilizing the Microsoft Trusted Signing service to sign their malware with short-lived, three-day code-signing certificates.
These malware samples are signed by “Microsoft ID Verified CS EOC CA 01” and the certificate is only valid for three days. While the certificate expires three days after being issued, it is important to note that executables signed with it will still be considered valid until the issuer revokes the certificate.
Since then other researchers and BleepingComputer have found numerous other samples used in ongoing malware campaigns, including those used in a Crazy Evil Traffers crypto-theft campaign [VirusTotal] and Lumma Stealer [VirusTotal] campaigns.
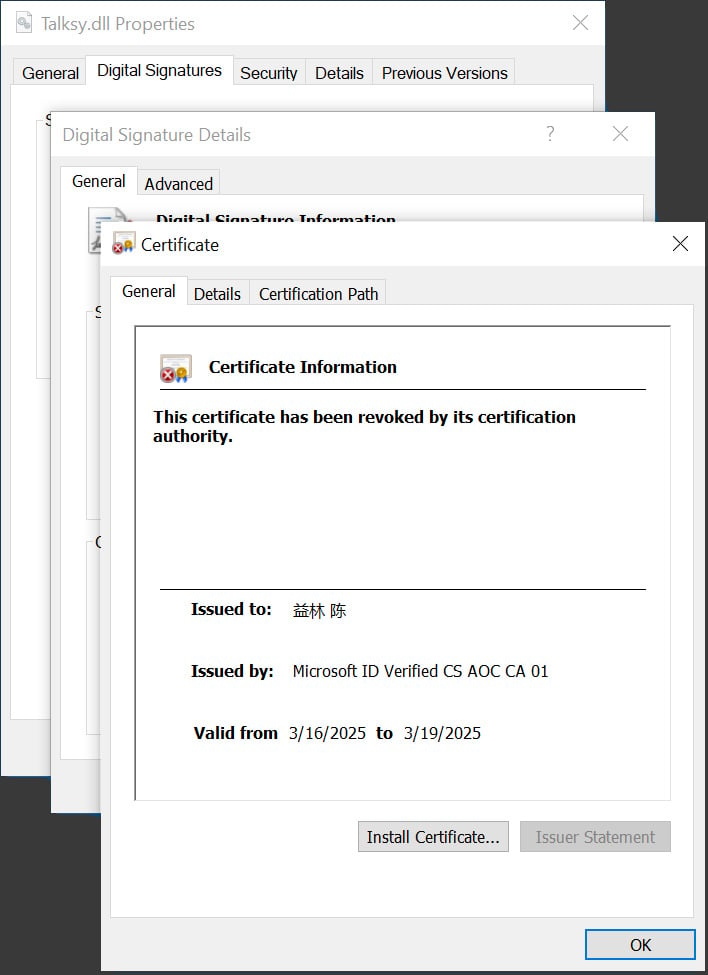
Source: BleepingComputer
The Microsoft Trusted Signing service launched in 2024 and is a cloud-based service that allows developers to easily have their programs signed by Microsoft.
“Trusted Signing is a complete code signing service with an intuitive experience for developers and IT professionals, backed by a Microsoft managed certification authority,” reads a Microsoft announcement for the service.
“The service supports both public and private trust signing scenarios and includes a timestamping service.”
The platform has a $9.99 monthly subscription service designed to make it easy for developers to sign their executables, while also offering additional security.
This increased security is accomplished by using short-lived certificates that can easily be revoked in the event of abuse and by never issuing the certificates directly to the developers, preventing them from being stolen in the event of a breach.
Microsoft also says certificates issued through the Trusted Signing service provide a similar SmartScreen reputation boost to executables signed by its service.
“A Trusted Signing signature ensures that your application is trusted by providing base reputation on smart screen, user mode trust on Windows, and integrity check signature validation compliant,” reads an FAQ on the Trusted Signing site.
To protect against abuse, Microsoft is currently only allowing certificates to be issued under a company name if they have been in business for three years.
However, individuals can sign up and get approved more easily if they are okay with the certificates being issued under their name.
A simpler path
A cybersecurity researcher and developer known as ‘Squiblydoo,’ who has been tracking malware campaigns abusing certificates for years, told BleepingComputer that they believe threat actors are switching to Microsoft’s service out of convenience.
“I think there are a few reasons for the change. For a long time, using EV certificates has been the standard, but Microsoft has announced changes to EV certificates,” Squiblydoo told BleepingComputer.
“However, the changes to EV certificates really aren’t clear to anyone: not certificate providers, not attackers. However, due to these potential changes and lack of clarity, just having a code-signing certificate may be adequate for attacker needs.”
“In this regard, the verification process for Microsoft’s certificates is substantially easier than the verification process for EV certificates: due to the ambiguity over EV certificates, it makes sense to use the Microsoft certificates.”
BleepingComputer contacted Microsoft about the abuse and was told that the company uses threat intelligence monitoring to find and revoke certificates as they are found.
“We use active threat intelligence monitoring to constantly look for any misuse or abuse of our signing service,” Microsoft told BleepingComputer.
“When we detect threats we immediately mitigate with actions such as broad certificate revocation and account suspension. The malware samples you shared are detected by our antimalware products and we have already taken action to revoke the certificates and prevent further account abuse.”
Source link