bypass
-
Blog

Hewlett Packard Enterprise warns of critical StoreOnce auth bypass
Hewlett Packard Enterprise (HPE) has issued a security bulletin to warn about eight vulnerabilities impacting StoreOnce, its disk-based backup and deduplication solution. Among the flaws fixed this time is a critical severity (CVSS v3.1 score: 9.8) authentication bypass vulnerability tracked under CVE-2025-37093, three remote code execution bugs, two directory traversal problems, and a server-side request forgery issue. The flaws impact…
Read More » -
Blog

Unpatched critical bugs in Versa Concerto lead to auth bypass, RCE
Critical vulnerabilities in Versa Concerto that are still unpatched could allow remote attackers to bypass authentication and execute arbitrary code on affected systems. Three security issues, two of them critical, were publicly disclosed by researchers at the vulnerability management firm ProjectDiscovery after reporting them to the vendor and receiving no confirmation of the bugs being addressed. Versa Concerto is the centralized management…
Read More » -
Blog

Google patches Chrome vulnerability used for account takeover and MFA bypass
“Unlike other browsers, Chrome resolves the Link header on subresource requests. But what’s the problem? The issue is that the Link header can set a referrer-policy. We can specify unsafe-url and capture the full query parameters,” he wrote. Link headers are used by websites to tell a browser about important page resources, for example, images, that it should preload. As…
Read More » -
Blog

New “Bring Your Own Installer” EDR bypass used in ransomware attack
A new “Bring Your Own Installer” EDR bypass technique is exploited in attacks to bypass SentinelOne’s tamper protection feature, allowing threat actors to disable endpoint detection and response (EDR) agents to install the Babuk ransomware. This technique exploits a gap in the agent upgrade process that allows the threat actors to terminate running EDR agents, leaving devices unprotected. The attack was…
Read More » -
Blog

ASUS warns of critical auth bypass flaw in routers using AiCloud
ASUS is warning about an authentication bypass vulnerability in routers with AiCloud enabled that could allow remote attackers to perform unauthorized execution of functions on the device. The vulnerability, tracked under CVE-2025-2492 and rated critical (CVSS v4 score: 9.2), is remotely exploitable via a specially crafted request and requires no authentication, making it particularly dangerous. “An improper authentication control vulnerability…
Read More » -
Blog

Hackers exploit WordPress plugin auth bypass hours after disclosure
Hackers started exploiting a high-severity flaw that allows bypassing authentication in the OttoKit (formerly SureTriggers) plugin for WordPress just hours after public disclosure. Users are strongly recommended to upgrade to the latest version of OttoKit/SureTriggers, currently 1.0.79, released at the beginning of the month. The OttoKit WordPress plugin allows users to connect plugins and external tools like WooCommerce, Mailchimp, and Google Sheets,…
Read More » -
Blog

Windows 11 Forces Microsoft Account Sign In & Removes Bypass Trick Option
Microsoft is making it increasingly difficult to set up Windows 11 without signing into a Microsoft Account. A popular workaround that previously allowed users to bypass the mandatory login is being removed, effectively requiring an internet connection and Microsoft Account during the initial setup. Goodbye, bypass trick For years, Windows users who preferred local accounts — or simply didn’t want…
Read More » -
Blog

New Windows 11 trick lets you bypass Microsoft Account requirement
A previously unknown trick lets you easily bypass using a Microsoft Account in Windows 11, just as Microsoft tries to make it harder to use local accounts. Since the release of Windows 11, Microsoft has been increasingly closing loopholes and making it harder to use a local account in the operating system. Instead, the company wants you to use a…
Read More » -
Blog
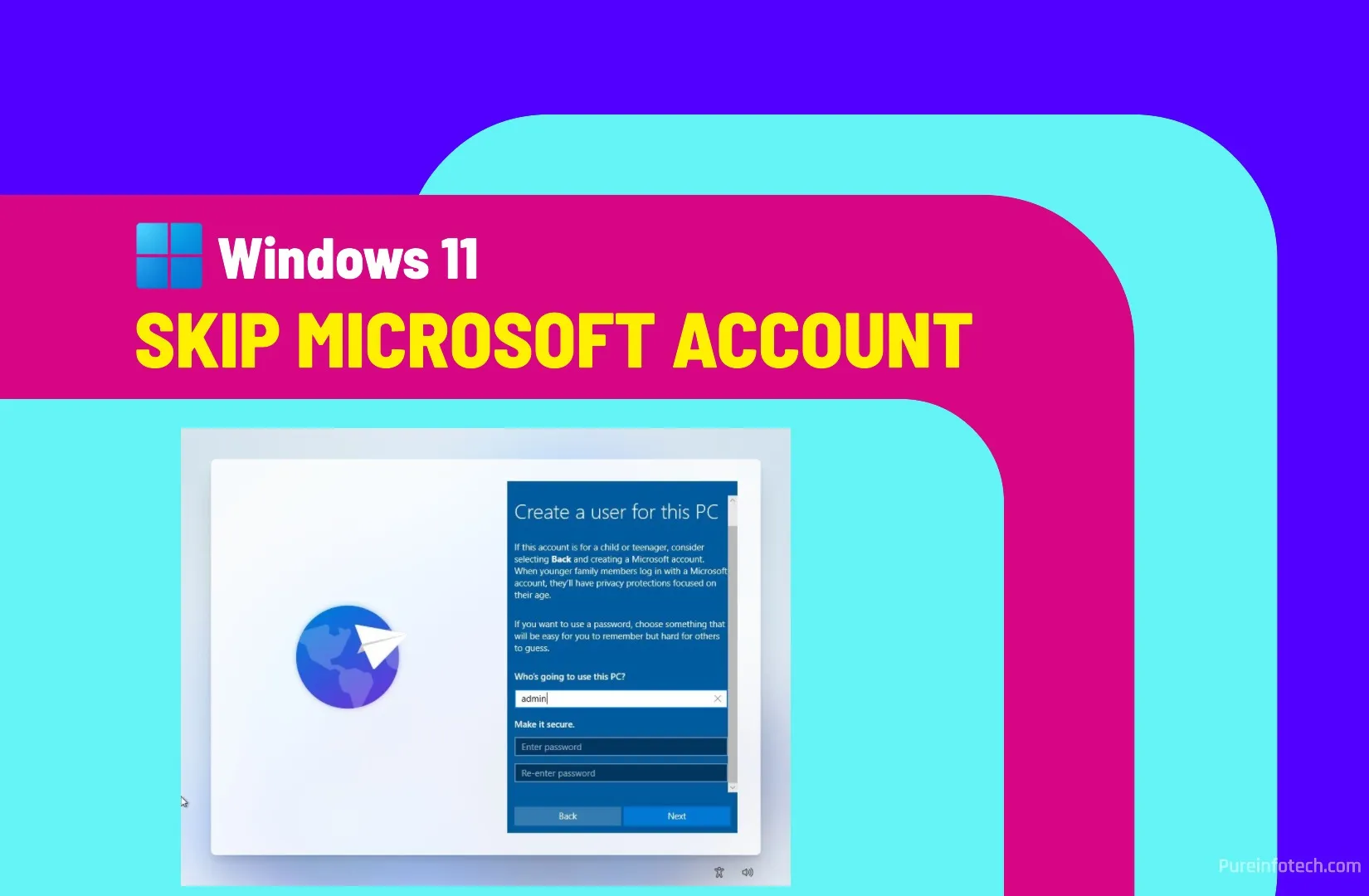
3 Better ways to bypass Microsoft Account during setup on Windows 11
You still have more than one way to skip the Microsoft Account to set up Windows 11 with a local account during the Out-of-box Experience (OOBE), and in this guide, I’ll explain how to complete this process. Starting with the release of Windows 11 build 26120.3653 (Beta) and build 26200.5516 (Dev), Microsoft has announced that it’s officially removing the ability…
Read More » -
Blog
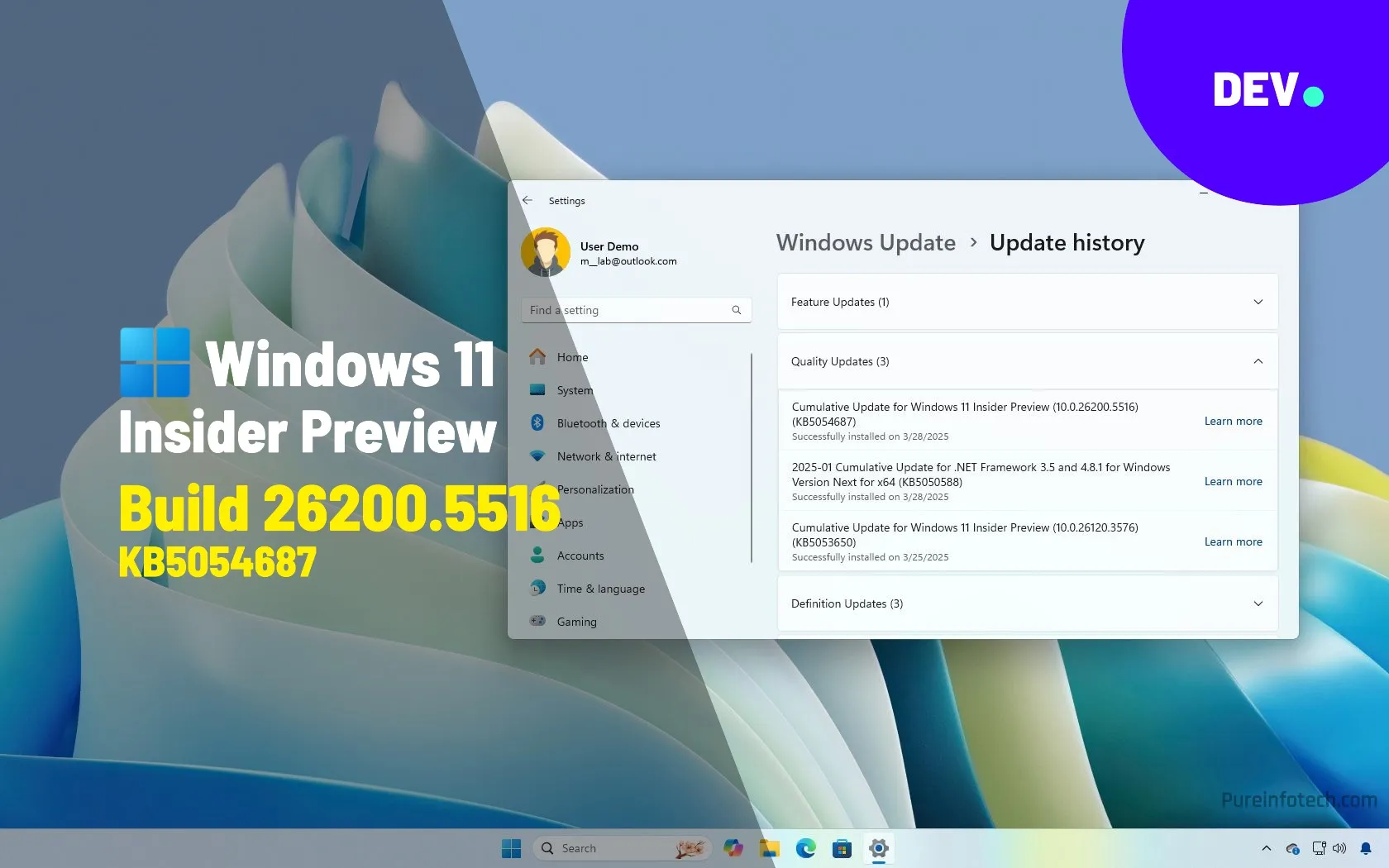
KB5054687 (build 26200.5516) for Windows 11 removes internet bypass in Dev Channel
Windows 11 build 26200.5516 is now rolling out in the Dev Channel as the update KB5054687 as part of the version 24H2 development. This preview introduces Local Semantic Search as well as other new features and changes like those available on Windows 11 build 26120.3653 in the Beta Channel, including a speech recap for Windows Narrator, a new interface to…
Read More »

