key
-
Blog

RSAC in focus: Key takeaways for CISOs
The RSAC Conference 2025 last month left CISOs to process a whirlwind of discussions, innovations, and evolving strategic imperatives. Building on themes that gained significant traction in previous years, 2025’s event solidified several critical areas demanding CISO attention, from the pervasive influence of AI to the increasing personal and professional pressures of the CISO role itself. For security leaders navigating…
Read More » -
Blog
ADA-Compliant Refrigerator Key Features for a Disabled User
Doors with pull handles are better than those with recessed handles for people with gross motor impairments. A refrigerator can be ADA compliant and still have recessed handles, so keep that in mind as you consider ADA fridges. You also want doors that aren’t too heavy to open and can be opened with one arm. Door-in-door compartments are convenient for…
Read More » -
Blog

Ivanti Workspace Control hardcoded key flaws expose SQL credentials
Ivanti has released security updates to fix three high-severity hardcoded key vulnerabilities in the company’s Workspace Control (IWC) solution. IWC helps enterprise admins manage desktops and applications, acting as an intermediary between the operating system and users and regulating access and workspace configuration. It provides centralized control over user workspaces and dynamically configures desktops, applications, and user settings based on…
Read More » -
Blog

Is Google Chat safe? Key risks and how to avoid them
It’s a fast and easy way to keep in touch with friends and colleagues, but is Google Chat safe? Well, it does offer solid basics like TLS encryption, 2FA, and spam filters, but its lack of end-to-end encryption leaves you open to snooping from Google and Workspace admins. Moreover, Google collects data from your chats to enhance its products, which…
Read More » -
Blog

Hackers are using fake tool installers to dupe victims – and AI tools like ChatGPT are a key target
Cyber criminals are spreading malware disguised as popular tool installers to target B2B sales and the technology and marketing sectors, according to new threat research. Cisco Talos said it has found the CyberLock and Lucky_Gh0$t ransomware, along with a newly-discovered malware dubbed ‘Numero’, masquerading as popular and legitimate AI tool installers to dupe victims. Chetan Raghuprasad, a cybersecurity researcher at…
Read More » -
Blog

‘A bold and highly strategic move’: Why Salesforce’s Informatica acquisition could be the key to Benioff’s agentic AI dream
Salesforce’s acquisition of Informatica could be a game changer for the company’s agentic AI ambitions, according to industry analysts, but questions still remain over how it will fit under the CRM giant’s umbrella. The $8 billion deal, announced earlier this week, will create the “most complete, agent-read data platform in the industry”, according to Salesforce CEO Marc Benioff. By bringing…
Read More » -
Blog
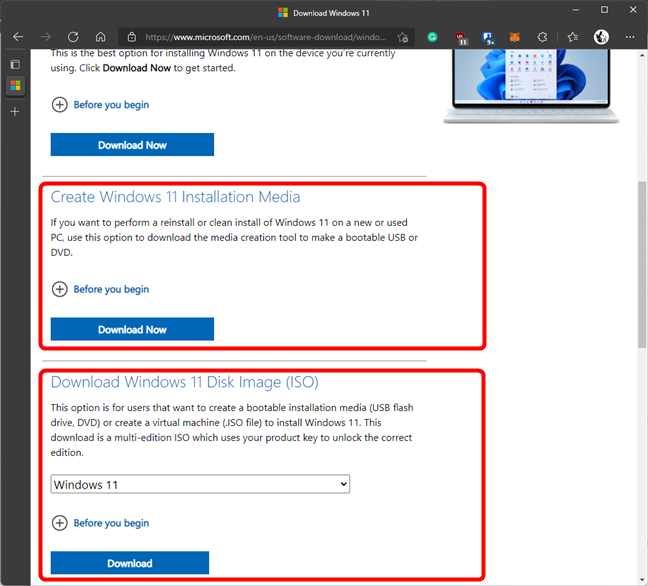
Windows 11 doesn’t require a product key to install and use
Yes, you read that correctly: you can install Windows 11 without a key and use it without ever activating it. Microsoft no longer forces you to provide a license during its setup, which means you can install Windows 11 without a product key and still access most of its features. However, what does this actually mean for you, and what…
Read More » -
Blog

CDAOs might be key to genAI success now — but that could change – Computerworld
After years of being focused primarily on data — not employee — management, surveys show CDOs often lack the skills to tackle the cultural challenges critical to a data-driven culture, Davenport said. “Surveys of CDOs also suggest that their jobs are less well understood than other C-level executives,” he added. In one recent article, Davenport argued there are too many…
Read More » -
Blog

DDoS Attacks Now Key Weapons in Geopolitical Conflicts, NETSCOUT Warns
Image: EV_Korobov/Adobe Stock Cyberattacks aren’t just about stealing data anymore — they’ve evolved into a key weapon in geopolitical fights, crippling vital infrastructure, and shaking public trust in governments. A new report by NETSCOUT reveals that hackers are increasingly using Distributed Denial of Service (DDoS) attacks to disrupt elections, protests, and policy debates, turning digital sabotage into a tool of…
Read More » -
Blog

First UK homes to be warmed by data center waste heat as key partnership is signed for West London development
The UK is to get its first district heat network powered by waste heat from a data center, thanks to a deal between Old Oak & Park Royal Development Corporation (OPDC) and district heating firm Hemiko. The first of half a dozen projects announced by the Department for Energy Security and Net Zero last year, the plan is to provide…
Read More »


