VPN
-
Blog

SonicWall warns of trojanized NetExtender stealing VPN logins
SonicWall is warning customers that threat actors are distributing a trojanized version of its NetExtender SSL VPN client used to steal VPN credentials. The fake software, which was discovered by SonicWall’s and Microsoft Threat Intelligence (MSTIC) researchers, mimics the legitimate NetExtender v10.3.2.27, the latest available version. The malicious installer file is hosted on a spoofed website that is made to appear…
Read More » -
Blog

How to set up a DIY torrent VPN kill switch
Torrenting is a great way to download and share large files efficiently. The trouble is that torrenting is built on peer-to-peer (P2P) file sharing, which means your IP address is visible to every user in the swarm. This runs the risk of privacy breaches and legal trouble in countries with strict copyright laws and aggressive enforcement. You might already have…
Read More » -
Blog

Does a VPN work without wifi?
If you’re worried about your online privacy as well as the security of your data when traveling, you’ll want to know if a VPN can protect you. Perhaps you’re using mobile data but can’t get your VPN to work, and want to troubleshoot the issue. Or maybe you’re wondering whether a VPN is even needed without wifi. Whatever the case, we’ll…
Read More » -
Blog

How to make your VPN undetectable in 10 simple steps
Some networks go out of their way to stop VPN traffic, whether it’s to control what you can access, limit your privacy, or avoid legal issues. Learning how to make your VPN undetectable with a few (mostly) easy tweaks can save you a lot of frustration and help you avoid blocks. Since no single method works every time, the best…
Read More » -
Blog

How to set up CyberGhost VPN on your ASUS Wi-Fi 7 router with VPN Fusion
VPN Fusion is one of the best features of ASUS extendable routers and ZenWiFi mesh systems. It allows users to connect their routers to multiple VPN servers and assign different network devices to specific VPN connections (or tunnels). For instance, your gaming console can be connected to a VPN server optimized for minimal latency when playing games online, while your…
Read More » -
Blog

Using VPN and Tor (Onion Browser) on iOS
If you’re looking to improve your privacy on your iPhone or iPad, you may find yourself considering a VPN or the Tor network. Unfortunately, things get a little tricky when it comes to iOS, regardless of whether you’re only using Tor or combining it with a VPN. Apple’s iOS operating system has some limitations that can make true anonymity more…
Read More » -
Blog
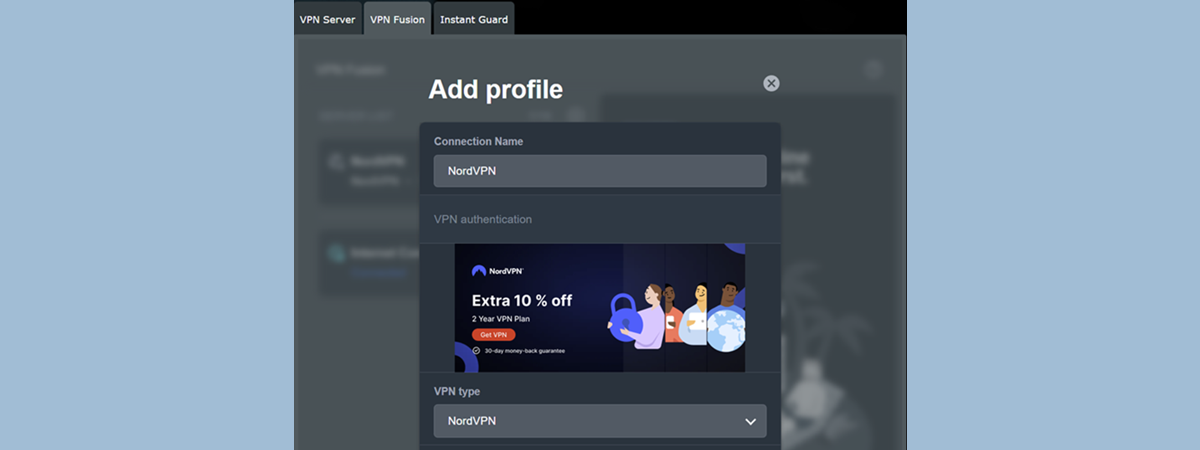
How to set up NordVPN on your ASUS Wi-Fi 7 router with VPN Fusion
VPN Fusion is one of the most popular features of ASUS extendable routers and ZenWiFi mesh systems. With VPN Fusion, you can connect to multiple VPN servers and assign different network devices to specific VPN connections (or tunnels). For instance, your Smart TV can be connected to a VPN server from a region that provides access to more content on…
Read More » -
Blog

Which iOS VPN protocol is best? Our recommendations
Selecting the right VPN protocol for your iOS device can dramatically impact performance, security, and battery life. This guide examines the leading protocols available for iPhone users, weighing real-world performance against technical specifications to help you make an informed decision. What are the VPN protocols on iOS? iOS supports several VPN protocols, each with distinct advantages: WireGuard: Modern, lightweight protocol…
Read More » -
Blog
Ever heard of a VPN? Take our survey and help shape our content
Here at Tom’s Guide, we love writing about the best VPNs and all the data privacy and cybersecurity news that come with them. Every day we’re testing various VPNs to see how effective they are – but we want to know what you think of VPNs, whether or not you use them, and what you think is the most important…
Read More » -
Blog

SMA100 VPN vulnerabilities now exploited in attacks
Cybersecurity company SonicWall has warned customers that several vulnerabilities impacting its Secure Mobile Access (SMA) appliances are now being actively exploited in attacks. On Tuesday, SonicWall updated security advisories for the CVE-2023-44221 and CVE-2024-38475 security flaws to tag the two vulnerabilities as “potentially being exploited in the wild.” CVE-2023-44221 is described as a high-severity command injection vulnerability caused by improper…
Read More »

