Pros
-
Blog
Pros and Cons of Amazon Prime
Free same-day delivery: Orders that meet the minimum threshold, typically $25, qualify for free same-day delivery on more than 1 million items. Amazon will provide an estimated window of time for the delivery, and if your order doesn’t reach the minimum, you may still be able to pay a small fee for same-day shipping. Amazon Prime Day: Every summer, Amazon…
Read More » -
Blog

Tails OS Tutorial | Features, Installation, Pros, Cons
Tails is a Tor-based project inspired by the Debian Linux distro. Tails works on Tor Foundation, i.e., the onion router. It is supposed to be a secure OS and difficult to trace with ordinary tools/tricks. Tails is used to perform privacy-focused tasks without leaving digital traces. These tasks include accessing or monitoring the target, i.e., it is recommended to access…
Read More » -
Blog
Pros and Cons of a Bagged vs. Bagless Vacuum
If you’re looking to buy an upright or a canister vacuum, one of the first things you need to decide on is whether you want a bagged or a bagless model. As their names suggest, a bagged vacuum stores the dust it picks up in a disposable bag, while a bagless vacuum keeps the debris in a built-in canister that…
Read More » -
Blog
All-in-One Washer-Dryer Combos Pros and Cons
They can be pricey. All-in-one washer-dryers can cost $2,000 or more. The good news is that prices are leveling off. (GE’s combo washer-dryer launched at nearly $2,900; now it’s priced around $2,000.) By comparison, the Whirlpool washer-dryer we tested costs about the same as—or even a little less than—a Whirlpool front-loader in our ratings. Drying times are long. As noted…
Read More » -
Blog

HubSpot CRM Review 2025: Features, Pros & Cons
HubSpot’s fast facts Our star rating: 4/5 Pricing: Robust free version for up to 5 users. Paid tiers start at $15 per seat per month when billed annually. Key features: Lead prospecting and generation. Email templates and tracking. Document and payment management. Business forecasting. Powerful AI tools. 1,500+ integrations. Supports multiple industries. 1,500+ integrations. HubSpot is a popular customer relationship…
Read More » -
Blog

Features, Pricing, Security, Pros & Cons
Dashlane fast facts Our rating: 4.4 stars out of 5Pricing: Starts at $4.99 per monthKey features Secure password vault encryption. No recorded data breaches. Well-designed and intuitive user interface. Dashlane has become one of the most popular password managers available — and for good reason. It has top-tier zero-knowledge encryption for its password vault, a ton of convenient usability features,…
Read More » -
Blog

What is a Digital Wallet? The Pros, Cons, and How It Works
Gone are the days of the leather wallet and chunky billfold. Instead, people are turning to digital wallets: mobile phone-, tablet- and smartwatch-based tools that securely store payment details and other information. This technology is used to make payments in a more secure fashion than traditional credit card swipes and cash. But there are other benefits too, especially for small…
Read More » -
Blog

Pros, Cons, Pricing & Performance Insights
Hostinger fast facts Our rating: 4.15 out of 5 Pricing: Hostinger starts at $2.99 with a 48-month contract or $11.99 monthly. Key features: AI Website Builder AI Logo Maker WordPress auto-install tool Image: Hostinger Hostinger is a website-building application that performs as well or better than many popular website-building platforms today. Hostinger’s user-friendliness is aided by artificial intelligence (AI), which…
Read More » -
Blog
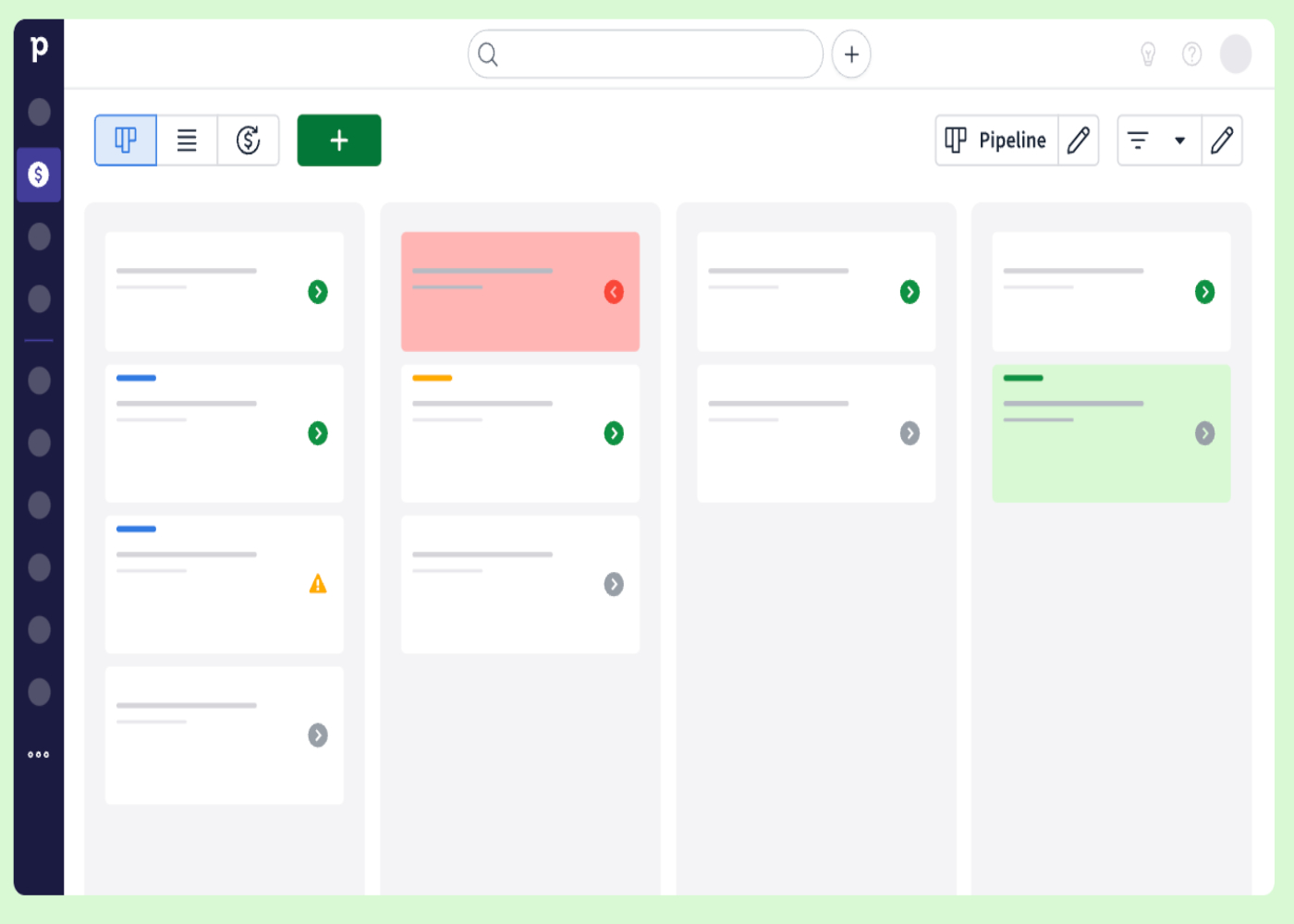
Features, Pricing, Pros & Cons
Pipedrive’s fast facts Our rating: 4.23 out of 5 Starting price: $14 per user per month, billed annually Key features: Visual pipeline management Web chat Lead scoring Communications tracking AI Sales Assistant Pipedrive’s CRM is a sales software offering custom pipeline management, activity and contact tracking, and reporting analytics. Pipedrive’s automations allow organizations to streamline workflows and reduce redundant sales…
Read More » -
Blog

The Pros and Cons of ‘Time of Use’ Utility Plans
It’s not just eggs—all the basics we need to live our lives are getting more expensive, including the energy we use to run our appliances, heat our homes, and do just about everything else. The average monthly cost for electricity and gas is already over $200, so when your utility bill spikes, it’s often a cause for panic. After all,…
Read More »




